Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: As either a business or as an individual, losing financial resources to scams and fraud can be deeply difficult,...
Day: September 30, 2023
FBI Warns of Rising Trend of Dual Ransomware Attacks Targeting U.S. Companies – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 30, 2023THNRansomware / Cyber Threat The U.S. Federal Bureau of Investigation (FBI) is warning of a new trend of dual...
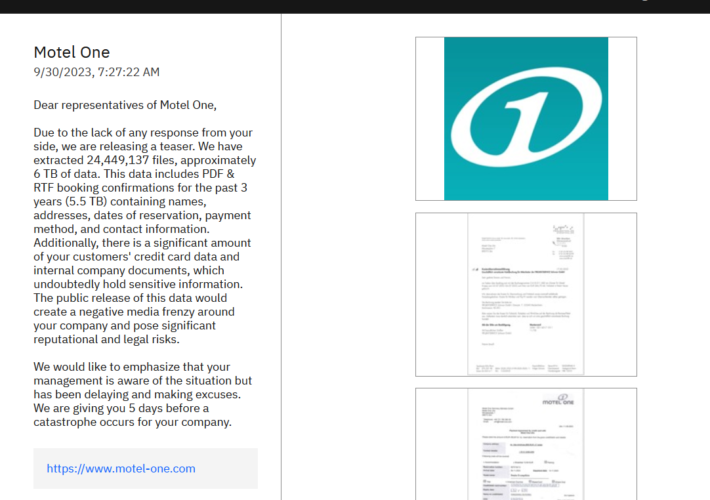
ALPHV/BlackCat ransomware gang hacked the hotel chain Motel One – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini ALPHV/BlackCat ransomware gang hacked the hotel chain Motel One Pierluigi Paganini September 30, 2023 The ALPHV/BlackCat ransomware gang added the...
FBI warns of dual ransomware attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini FBI warns of dual ransomware attacks Pierluigi Paganini September 30, 2023 The U.S. Federal Bureau of Investigation (FBI) warns of...
Progress Software fixed two critical severity flaws in WS_FTP Server – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Progress Software fixed two critical severity flaws in WS_FTP Server Pierluigi Paganini September 30, 2023 Progress Software has addressed a...
Child abuse site taken down, organized child exploitation crime suspected – exclusive – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Child abuse site taken down, organized child exploitation crime suspected – exclusive Pierluigi Paganini September 30, 2023 A child abuse...
A still unpatched zero-day RCE impacts more than 3.5M Exim servers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A still unpatched zero-day RCE impacts more than 3.5M Exim servers Pierluigi Paganini September 29, 2023 Experts warn of a...
Vulns Found In Another Progress Software File Transfer App – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management ‘There’s a 10-out-10 severity bug you need to patch right now!’ Prajeet Nair (@prajeetspeaks)...
Inside Look: FDA’s Cyber Review Process for Medical Devices – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Hardware / Chip-level Security , Healthcare Jessica Wilkerson of the FDA Details Agency’s ‘Refuse to Accept’ Policy and...
CrowdStrike Boosts Israeli Startup Ties With AWS Partnership – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Next-Generation Technologies & Secure Development AWS & CrowdStrike Cybersecurity Startup Accelerator Will Incubate Early-Stage Firms Michael Novinson (MichaelNovinson) • September 29,...
Editors’ Panel: What Impact Will Cisco’s Splunk Acquisition Have on Industry? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Operational Technology (OT) , Security Information & Event Management (SIEM) Also: OT Security Trends, Challenges; FDA...
NSA Stands Up New Organization to Harness AI – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development A US Advantage on AI Should ‘Not Be Taken For...
Securing AI: What You Should Know – Source: www.darkreading.com
Source: www.darkreading.com – Author: Anton Chuvakin, Security Advisor at Office of the CISO, Google Cloud Machine-learning tools have been a part of standard business and IT...
How Can Your Security Team Help Developers Shift Left? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Scott Gerlach, Co-Founder and Chief Security Officer, StackHawk Question: How can I get my organization to shift its security left without slowing...
DHS: Physical Security a Concern in Johnson Controls Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In the latest development around the cyberattack impacting Johnson Controls International (JIC), officials at the Department of Homeland...
Friday Squid Blogging: Protecting Cephalopods in Medical Research – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier From Nature: Cephalopods such as octopuses and squid could soon receive the same legal protection as mice and monkeys do...
Three men found guilty of laundering $2.5 million in Target gift card tech support scam – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Three Californian residents have been convicted of laundering millions of dollars tricked out of older adults who had fallen victim...
ZeroFont trick makes users think that message has been scanned for threats – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley It’s nothing new for cybercriminals to use sneaky HTML tricks in their attempt to infect computers or dupe unsuspecting recipients...
Weekly Update 367 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Ah, home 😊 It’s been more than a month since I’ve been able to sit at this desk and stream...
Bankrupt IronNet Shuts Down Operations – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The lights have flickered shut at IronNet, the once-promising network security company founded by former NSA director General Keith Alexander....
AWS Using MadPot Decoy System to Disrupt APTs, Botnets – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Cloud computing giant AWS says an internal threat intel decoy system called MadPot has been used successfully to trap malicious...
Generative AI Startup Nexusflow Raises $10.6 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire California startup Nexusflow on Thursday announced that it has raised $10.6 million in seed funding to work on technology to...
In Other News: RSA Encryption Attack, Meta AI Privacy, ShinyHunters Hacker Guilty Plea – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Researchers Extract Sounds From Still Images on Smartphone Cameras – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A group of academic researchers has devised a technique to extract sounds from still images captured using smartphone cameras with...
National Security Agency is Starting an Artificial Intelligence Security Center – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The National Security Agency is starting an artificial intelligence security center — a crucial mission as AI capabilities are increasingly...
CISA Warns of Old JBoss RichFaces Vulnerability Being Exploited in Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs US cybersecurity agency CISA is warning organizations that an old vulnerability affecting JBoss RichFaces has been exploited in attacks. The...
Hackers Set Sights on Apache NiFi Flaw That Exposes Many Organizations to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A high-severity remote code execution (RCE) vulnerability in Apache NiFi, for which an exploitation tool already exists, can lead to...
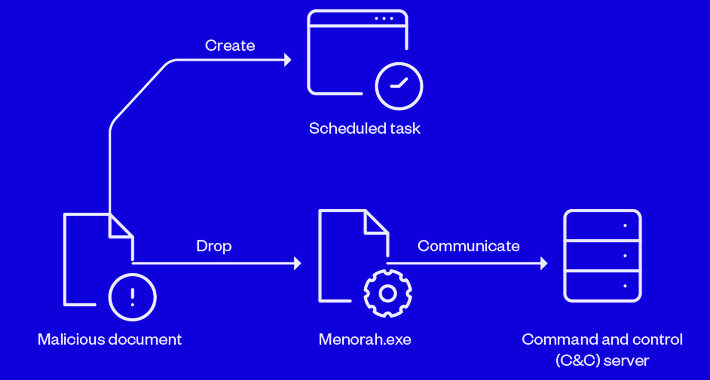
Iranian APT Group OilRig Using New Menorah Malware for Covert Operations – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 30, 2023THNCyber Espionage / Malware Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing...
New Critical Security Flaws Expose Exim Mail Servers to Remote Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 30, 2023THNEmail Security / Hacking News Multiple security vulnerabilities have been disclosed in the Exim mail transfer agent that, if...
Progress Software Releases Urgent Patches to Fix WS_FTP Server Vulnerabilities – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Progress Software, the developer behind the MOVEit Transfer file-sharing platform recently issued a patch for a maximum severity vulnerability in...