Source: www.securityweek.com – Author: Ryan Naraine Enterprise technology vendor Progress Software on Thursday shipped patches for critical-level security flaws in its WS_FTP file transfer software, warning...
Day: September 29, 2023
Verisoul Raises $3.25 Million in Seed Funding to Detect Fake Users – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Verisoul, an Austin, Texas-based company that has developed a SaaS platform for detecting and blocking fake users, announced on Thursday...
Lumu Raises $30 Million for Threat Detection and Response Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Lumu, a cybersecurity firm that helps organizations identify and isolate potential compromises, on Wednesday announced that it has raised $30...
Government Shutdown Could Bench 80% of CISA Staff – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Roughly 80% of the staff at US cybersecurity agency CISA may be sent home at the end of the week...
12 Benefits of Zero Trust for Mid-Sized Businesses – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Antonia Din Zero Trust security is evolving from “nice to have” to an absolute must for organizations everywhere. Fortunately, Zero Trust offers...
Ransomware group demands $51 million from Johnson Controls after cyber attack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Johnson Controls, a multinational conglomerate that secures industrial control systems, security equipment, fire safety and air conditioning systems, has been...
Privacy Regulator Orders End to Spreadsheet FOI Responses – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s information commissioner has called for an immediate end to the use of excel spreadsheets to publish Freedom of Information (FOI)...
Microsoft Breach Exposed 60,000 State Department Emails – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A sophisticated Chinese cyber-espionage campaign targeting Microsoft Outlook accounts gave Beijing access to tens of thousands of private US government emails,...
MOVEit Developer Patches Critical File Transfer Bugs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Progress Software has urged customers to patch a critical new vulnerability in one of its flagship file transfer software products, which...
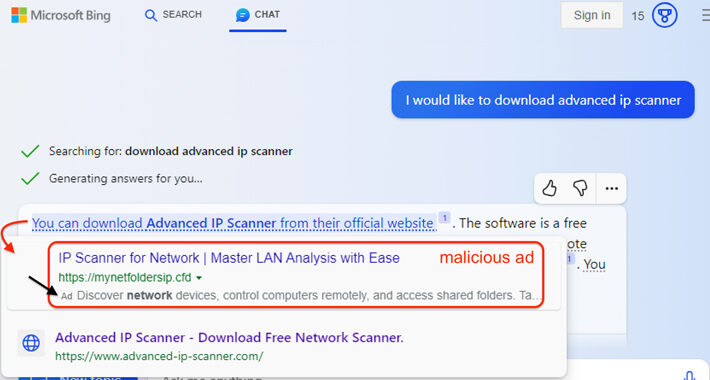
Microsoft’s AI-Powered Bing Chat Ads May Lead Users to Malware-Distributing Sites – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 29, 2023THNArtificial Intelligence / Malware Malicious ads served inside Microsoft Bing’s artificial intelligence (AI) chatbot are being used to distribute...
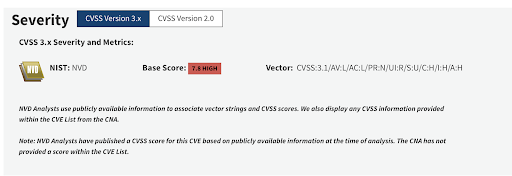
Progress Software Releases Urgent Hotfixes for Multiple Security Flaws in WS_FTP Server – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 29, 2023THNServer Security / Vulnerability Progress Software has released hotfixes for a critical security vulnerability, alongside seven other flaws, in...
Cisco Warns of Vulnerability in IOS and IOS XE Software After Exploitation Attempts – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 29, 2023THNVulnerability / Network Security Cisco is warning of attempted exploitation of a security flaw in its IOS Software and...
Progress warns of maximum severity WS_FTP Server vulnerability – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Progress Software, the maker of the MOVEit Transfer file-sharing platform recently exploited in widespread data theft attacks, warned customers to...
Microsoft breach led to theft of 60,000 US State Dept emails – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Chinese hackers stole tens of thousands of emails from U.S. State Department accounts after breaching Microsoft’s cloud-based Exchange email platform...
Bing Chat responses infiltrated by ads pushing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Malicious advertisements are now being injected into Microsoft’s AI-powered Bing Chat responses, promoting fake download sites that distribute malware. Bing...
FBI: Dual ransomware attack victims now get hit within 48 hours – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The FBI has warned about a new trend in ransomware attacks where multiple strains are deployed on victims’ networks to encrypt...
Cisco urges admins to fix IOS software zero-day exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Cisco warned customers on Wednesday to patch a zero-day IOS and IOS XE software vulnerability targeted by attackers in the...
Cisco Catalyst SD-WAN Manager flaw allows remote server access – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cisco is warning of five new Catalyst SD-WAN Manager products vulnerabilities with the most critical allowing unauthenticated remote access to...
Security researcher stopped at US border for investigating crypto scam – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Security researcher Sam Curry describes a stressful situation he encountered upon his return to the U.S. when border officials and...
Budworm hackers target telcos and govt orgs with custom malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A Chinese cyber-espionage hacking group tracked as Budworm has been observed targeting a telecommunication firm in the Middle East and...
How To Implement Zero Trust: Best Practices and Guidelines – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke on September 28, 2023, 12:23 PM EDT How To Implement Zero Trust: Best Practices and Guidelines Implement a Zero Trust...
NordVPN Review (2023): Pricing, Security & Performance – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares NordVPN Fast facts Our rating: 4.7 stars out of of 5 Pricing: Starts at $5.79 per month Key features Offers...
What You Need to Know About the libwebp Exploit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yael Citro libwebp exploit timeline CVE-2023-41064; CVE-2023-4863; CVE-2023-5129 On September 7th 2023, researchers at Citizen Lab reported a zero-click exploit that was...
Why Ordr? Why Now? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wes Wright I just joined Ordr as Chief Healthcare Officer and, as is often the case in life, there’s a story, personal...
Crocs enhances customer journey and safeguards revenue growth with Kasada – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kasada Customer background Crocs is one of the world’s top non-athletic footwear brands. With over 100 million pairs of shoes sold per...
Threat Spotlight: The Dark Web and AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare Executive Overview More than 200,000 credentials to AI language models are currently being sold on the dark web as part of...
Lawsuit Filed Against Google, Meta, H&R Block for Sharing Taxpayer Data – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Meta, Google, and giant tax preparer H&R Block are being accused of conspiring to illegally use spyware from the tech...
Cyber Week 2023 & The Israel National Cyber Directorate Presents – Red Alert – Europe Israel Cyber Security Summit – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/cyber-week-2023-the-israel-national-cyber-directorate-presents-red-alert-europe-israel-cyber-security-summit/ Category & Tags: CISO Suite,Governance, Risk &...
Sidecar Containers in Kubernetes: A Personal Journey – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthias Bertschy I had always wanted to use sidecars with Istio or Splunk forwarder in production, but as a Kubernetes maintainer, I...
Unlocking Endpoint Security as a Service: 2023 Insights! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Introduction In the evolving landscape of cyber threats, small businesses find themselves in the crosshairs, necessitating robust and dynamic security...