Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido Once again, politicians are playing political football, threatening a fourth partial government shutdown in a decade. Related:...
Day: September 29, 2023
Cybercriminals Using New ASMCrypt Malware Loader Flying Under the Radar – Source:thehackernews.com
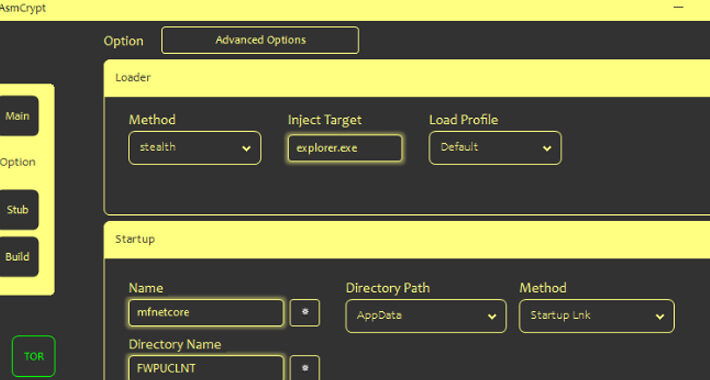
Source: thehackernews.com – Author: . Threat actors are selling a new crypter and loader called ASMCrypt, which has been described as an “evolved version” of another...
Lazarus Group Impersonates Recruiter from Meta to Target Spanish Aerospace Firm – Source:thehackernews.com
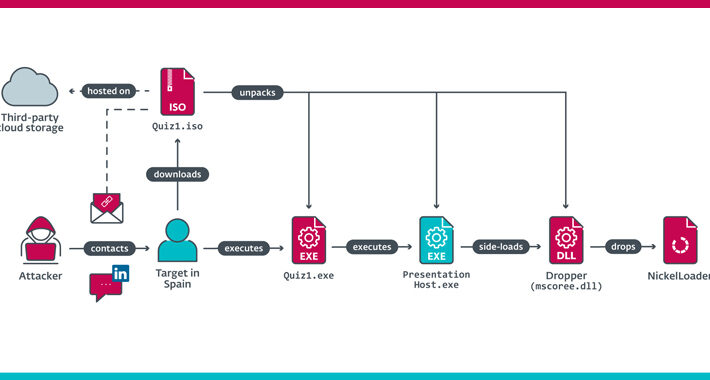
Source: thehackernews.com – Author: . Sep 29, 2023THNCyber Espionage / Malware The North Korea-linked Lazarus Group has been linked to a cyber espionage attack targeting an...
Post-Quantum Cryptography: Finally Real in Consumer Apps? – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 29, 2023The Hacker NewsQuantum Computing / Network Security Most people are barely thinking about basic cybersecurity, let alone post-quantum cryptography....
Russian Company Offers $20m For Non-NATO Mobile Exploits – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Russian firm Operation Zero has announced a staggering $20m reward for hacking tools capable of compromising iPhones and Android devices. ...
Microsoft’s Bing AI Faces Malware Threat From Deceptive Ads – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft’s Bing Chat has come under scrutiny due to a significant security concern – the infiltration of malicious ads. Malwarebytes researchers...
Phishing, Smishing Surge Targets US Postal Service – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Recent weeks have witnessed a significant increase in cyber-attacks targeting the US Postal Service (USPS), mainly through phishing and smishing campaigns. ...
Chinese threat actors stole around 60,000 emails from US State Department in Microsoft breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Chinese threat actors stole around 60,000 emails from US State Department in Microsoft breach Pierluigi Paganini September 29, 2023 China-linked...
Misconfigured WBSC server leaks thousands of passports – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Misconfigured WBSC server leaks thousands of passports Pierluigi Paganini September 29, 2023 The World Baseball Softball Confederation (WBSC) left open...
CISA adds JBoss RichFaces Framework flaw to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds JBoss RichFaces Framework flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September 29, 2023 US CISA added...
Spyware Vendor Targets Egyptian Orgs With Rare iOS Exploit Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading An Israeli surveillanceware company used the three Apple zero-day vulnerabilities disclosed last week to develop an...
DHS Calls Into Question Physical Security in Johnson Controls Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In the latest development of the cyberattack impacting Johnson Controls International (JIC), officials at the Department of...
Cybersecurity Gaps Plague US State Department, GAO Report Warns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading The US Department of State must fully implement its cybersecurity risk program and take additional steps...
Move Over, MOVEit: Critical Progress Bug Infests WS_FTP Software – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading For the second time in recent months, Progress Software is requiring enterprise security teams to drop...
People Still Matter in Cybersecurity Management – Source: www.darkreading.com
Source: www.darkreading.com – Author: Curtis Franklin, Senior Analyst, Omdia In the run-up to the 1992 US presidential election, Bill Clinton’s campaign famously had a large sign...
Attacks on Azerbaijan Businesses Drop Malware via Fake Image Files – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading A spear-phishing email posing as a memo from the president of an Azerbaijan company hid malware...
QR Code 101: What the Threats Look Like – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading As QR codes have become ubiquitous, their proliferation has given rise to new and emerging security...
7 Ways SMBs Can Secure Their WordPress Sites – Source: www.darkreading.com
Source: www.darkreading.com – Author: Suhaib Zaheer, Senior VP & General Manager, Cloudways Enterprises large and small rely on WordPress: At least 43% of websites on the...
How the Okta Cross-Tenant Impersonation Attacks Succeeded – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nigel Douglas, Senior Technical Manager, Detection & Response, Sysdig A series of highly sophisticated attacks have sparked significant concerns among organizations that...
Chrome Patches 0-Day Exploited by Commercial Spyware Vendor – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management Limited Details Disclosed but Google said it is a Heap-based Buffer Overflow Bug Mihir...
Zero Trust, Auditability and Identity Governance – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Two years after President Biden’s landmark cybersecurity Executive Order, the question remains: How are federal agencies adapting to the new focus...
Study Reveals Conti Affiliates Money Laundering Practices – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cryptocurrency Fraud , Fraud Management & Cybercrime , Ransomware Affiliates Relied on Less Complex, Trackable Methods, It Says Akshaya Asokan (asokan_akshaya)...
Infusion Firm Faces Lawsuit After Hackers Hit Parent Company – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Proposed Class Action Claim Against Amerita Linked to Larger PharMerica...
Nord Security Raises $100M on $3B Valuation to Go After M&A – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Security Operations , Web Application Firewalls (WAF) VPN Service Behemoth Doubles Valuation In Just 17 Months Despite Economic Headwinds Michael Novinson...
Cloudflare Users Exposed to Attacks Launched From Within Cloudflare: Researchers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Gaps in Cloudflare’s security controls allow users to bypass customer-configured protection mechanisms and target other users from the platform itself,...
A Key US Government Surveillance Tool Should Face New Limits, a Divided Privacy Oversight Board Says – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Federal spy agencies should be required to get court approval before reviewing the communications of U.S. citizens collected through a...
NIST Publishes Final Version of 800-82r3 OT Security Guide – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs NIST announced on Thursday that it has published the final version of its latest guide to operational technology (OT) security. ...
FBI Warns Organizations of Dual Ransomware, Wiper Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The FBI is warning organizations of new trends in ransomware attacks, where victims are targeted by multiple file-encrypting malware families...
Johnson Controls Hit by Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Building technology giant Johnson Controls has confirmed being hit by a disruptive cyberattack that appears to have been carried out...
US State Department Says 60,000 Emails Taken in Alleged Chinese Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP The US State Department said Thursday that hackers took around 60,000 emails, although none of them classified, in an attack which...