Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware New Group Has Connections to Name-Brand Ransomware-as-a-Service Groups Mihir Bagwe (MihirBagwe) • September 27, 2023...
Day: September 28, 2023
Cisco Warns of IOS Software Zero-Day Exploitation Attempts – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco this week announced patches for multiple vulnerabilities impacting its products, including a medium-severity flaw in IOS and IOS XE...
Russian Zero-Day Acquisition Firm Offers $20 Million for Android, iOS Exploits – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Operation Zero, a Russian zero-day acquisition firm, announced this week that it is offering up to $20 million for full...
Sysdig Launches Realtime Attack Graph for Cloud Environments – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Cloud security firm Sysdig has enhanced the cloud detection and response capabilities of its CNAPP offering with a realtime cloud...
Google Rushes to Patch New Zero-Day Exploited by Spyware Vendor – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Google has rushed to patch another Chrome zero-day vulnerability exploited by a commercial spyware vendor. The internet giant announced on...
Chinese Gov Hackers Caught Hiding in Cisco Router Firmware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine A Chinese state-sponsored APT called BlackTech has been caught hacking into network edge devices and using firmware implants to stay...
CISA Unveils New HBOM Framework to Track Hardware Components – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The US government’s cybersecurity agency CISA has unveiled a new Hardware Bill of Materials (HBOM) framework offering a consistent, repeatable...
Google fixes fifth actively exploited Chrome zero-day of 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google has patched the fifth Chrome zero-day vulnerability exploited in attacks since the start of the year in emergency security...
SSH keys stolen by stream of malicious PyPI and npm packages – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A stream of malicious npm and PyPi packages have been found stealing a wide range of sensitive data from software...
Fake Bitwarden sites push new ZenRAT password-stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Fake Bitwarden sites are pushing installers purportedly for the open-source password manager that carry a new password-stealing malware that security...
Building automation giant Johnson Controls hit by ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Johnson Controls International has suffered what is described as a massive ransomware attack that encrypted many of the company devices,...
US and Japan Warn of Chinese Router Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US and Japanese authorities have urged multi-nationals to consider implementing zero trust models to mitigate a sophisticated Chinese state-backed cyber-espionage...
Google Patches Chrome Zero-Day Used in Spyware Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Google has patched three high-severity flaws in the latest release of its Chrome browser, including one zero-day vulnerability it said is...
UK Logistics Firm Forced to Close After Ransomware Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 One of the UK’s largest privately owned logistics firms has entered administration following major disruption to its business caused by a...
Atlas VPN Review (2023): Features, Pricing, Alternatives – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares AtlasVPN Fast Facts Our rating: 3.50 stars out of 5 Pricing: Starts at $4.08 per month Key features: IP address...
ProtonVPN vs. AtlasVPN (2023): Which VPN Should You Use? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Both Proton and Atlas VPN provide solid encryption and privacy protection for you and your business. For those concerned about...
Update Chrome Now: Google Releases Patch for Actively Exploited Zero-Day Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 28, 2023THNZero Day / Vulnerability Google on Wednesday rolled out fixes to address a new actively exploited zero-day in the...
Smashing Security podcast #341: Another T-Mobile breach, ThemeBleed, and farewell Naked Security – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Mix TikTok with facial recognition, and you’ve got a doxxing nightmare, T-Mobile users report bizarre behaviour in their accounts, and...
British charities warn supporters their personal data has been breached – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley UK charities including Shelter, the RSPCA, the Dogs Trust, Battersea Dogs and Cats Home, and Friends of the Earth have...
CAPTCHAs Easy for Humans, Hard for Bots – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Proton, the company behind the end-to-end encrypted Proton Mail, released PRoton CAPTCHA, a layered system to differentiate...
A Preview of Windows 11’s Passkeys Support – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer, Dark Reading Back in May 2022, Microsoft promised support for passwordless authentication using passkeys in the Windows operating...
Fortinet Announces Formation of Veterans Program Advisory Council to Narrow the Cybersecurity Skills Gap With Military Veteran Talent – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SUNNYVALE, Calif. – Sep 27, 2023 — John Maddison, EVP of Product Strategy and CMO at Fortinet “Military veterans can be vital to...
Netscout Identified Nearly 7.9M DDOS Attacks in the First Half of 2023 – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 WESTFORD, Mass., September 26, 2023 – NETSCOUT SYSTEMS, INC., (NASDAQ: NTCT) today announced findings from its 1H2023 DDoS Threat Intelligence Report. Cybercriminals launched...
Critical Vulnerability in libwebp Library – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Both Apple and Google have recently reported critical vulnerabilities in their systems—iOS and Chrome, respectively—that are ultimately the result of...
Researchers Release Details of New RCE Exploit Chain for SharePoint – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Researchers who discovered two critical vulnerabilities in Microsoft SharePoint Server have released details of an exploit...
China APT Cracks Cisco Firmware in Attacks Against the US and Japan – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading An old Chinese state-linked threat actor has been quietly manipulating Cisco routers to breach multinational organizations...
Microsoft Adds Passkeys to Windows 11 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In a major update to its Windows 11 operating system this week, Microsoft has integrated Passkeys alongside...
Threat Data Feeds and Threat Intelligence Are Not the Same Thing – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kurtis Minder, Co-Founder & CEO, GroupSense In cybersecurity, “threat data feeds” and “threat intelligence” are often used interchangeably. They are, however, quite...
Hackers Trick Outlook Into Showing Fake AV Scans – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Threat actors are employing an existing technique of zero-point font obfuscation in a new way to fool...
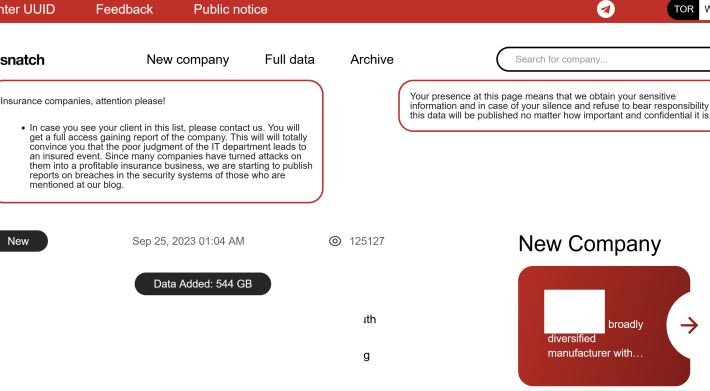
‘Snatch’ Ransom Group Exposes Visitor IP Addresses – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The victim shaming site operated by the Snatch ransomware group is leaking data about its true online location and internal operations,...