Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Day: September 26, 2023
Polish Privacy Regulator Probes OpenAI’s ChatGPT – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , General Data Protection Regulation (GDPR) , Next-Generation Technologies & Secure Development Agency Is the Latest...
UAE-Linked APT Targets Middle East Government With New ‘Deadglyph’ Backdoor – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The advanced persistent threat (APT) actor Stealth Falcon has been observed deploying a new backdoor on the systems of a...
Sony Investigating After Hackers Offer to Sell Stolen Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Sony has launched an investigation after a cybercrime group claimed to have compromised the company’s systems, offering to sell stolen...
The CISO Carousel and its Effect on Enterprise Cybersecurity – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The average tenure of a Chief Information Security Officer said to sit between 18 to 24 months. This is barely...
Xenomorph Android Banking Trojan Targeting Users in US, Canada – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Recently identified Xenomorph Android banking trojan samples show an expanded target list that now includes North American users, online fraud...
$200 Million in Cryptocurrency Stolen in Mixin Network Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Peer-to-peer digital asset transactional network Mixin Network has suspended deposits and withdrawals after hackers stole $200 million. The Hong Kong-based...
How to Create and Copy SSH Keys with 2 Simple Commands – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen TechRepublic Premium TechRepublic Premium Mental Health Policy Poor mental health can affect work performance in the form of burnout, absenteeism,...
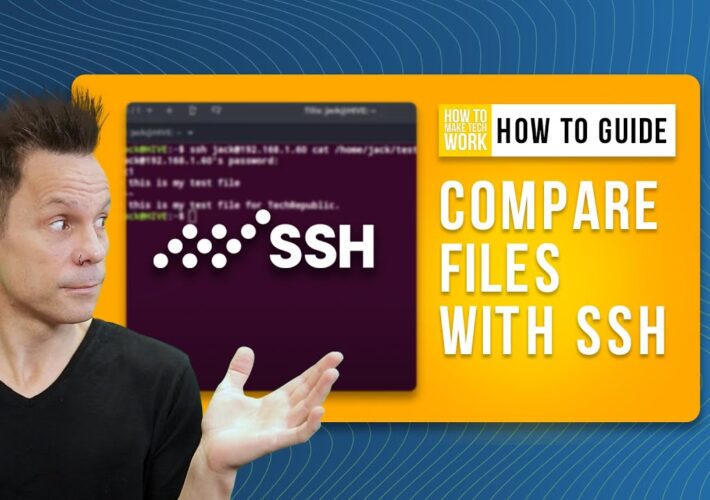
How to Compare the Contents of Local & Remote Files with the Help of SSH – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen TechRepublic Premium TechRepublic Premium Mental Health Policy Poor mental health can affect work performance in the form of burnout, absenteeism,...
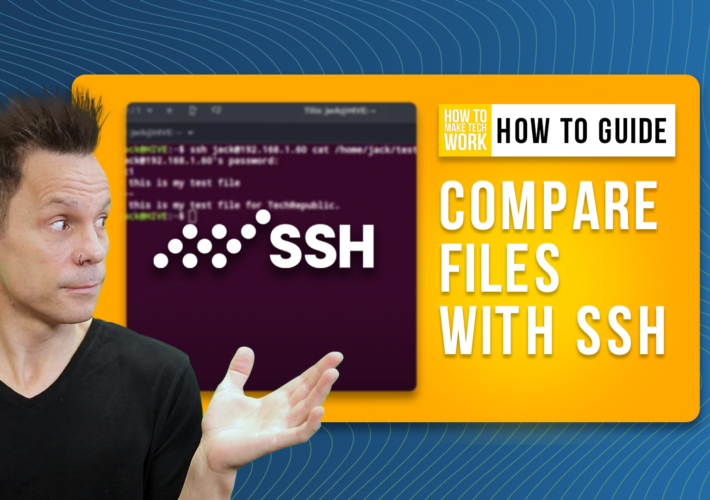
How to Compare the Contents of Local & Remote Files With the Help of SSH – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen on September 25, 2023, 3:05 PM EDT How to Compare the Contents of Local & Remote Files With the Help...
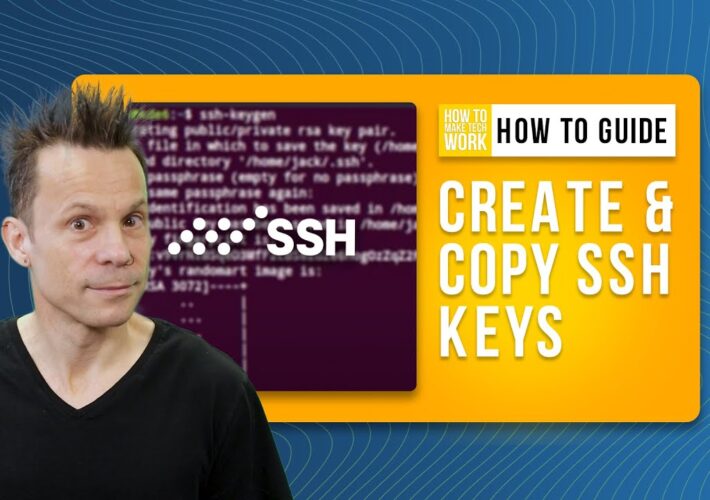
How to Create and Copy SSH Keys with 2 Simple Commands (+Video Tutorial) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen on September 25, 2023, 8:34 AM EDT How to Create and Copy SSH Keys with 2 Simple Commands (+Video Tutorial)...
Half of Cyber-Attacks Go Unreported – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Fear, ignorance and forgetfulness are some of the reasons for widespread shortcomings in reporting cyber-attacks and breaches, both internally and externally,...
Tech Giants Launch Post-Quantum Cryptography Coalition – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new tech consortium launched today with a mission to drive adoption of post-quantum cryptography (PQC). The PQC Coalition features Microsoft,...
CISA Publishes Hardware Bill of Materials Framework – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Cybersecurity and Infrastructure Security Agency (CISA) has published new guidance designed to improve the accuracy of risk assessments related...
Pension Firms Report 4000% Surge in Breaches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Pension providers reported a staggering quadruple-digit percentage increase in data breaches to the UK regulator last year, according to new data...
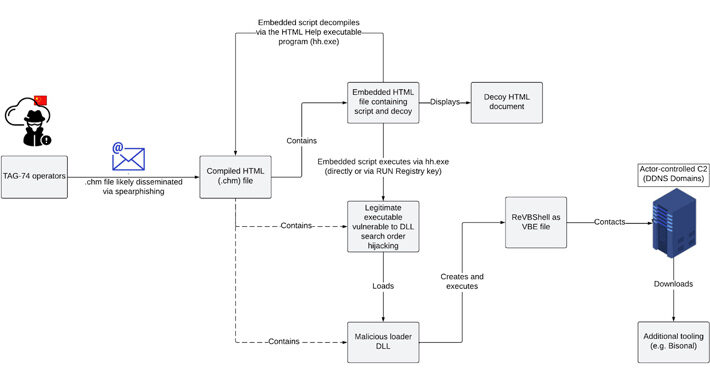
Chinese Hackers TAG-74 Targets South Korean Organizations in a Multi-Year Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 26, 2023THNCyber Espionage / Malware A “multi-year” Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political,...
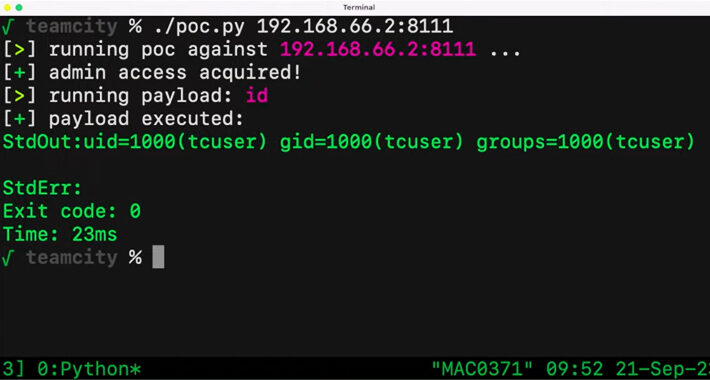
Critical JetBrains TeamCity Flaw Could Expose Source Code and Build Pipelines to Attackers – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 26, 2023THNVulnerability / Source Code A critical security vulnerability in the JetBrains TeamCity continuous integration and continuous deployment (CI/CD) software...
BORN Ontario child registry data breach affects 3.4 million people – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Better Outcomes Registry & Network (BORN), a healthcare organization funded by the government of Ontario, has announced that it is...
Google is retiring its Gmail Basic HTML view in January 2024 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google is notifying Gmail users that the webmail’s Basic HTML view will be deprecated in January 2024, and users will...
Xenomorph Android malware now targets U.S. banks and crypto wallets – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers discovered a new campaign that distributes a new version of the Xenomorph malware to Android users in the...
Mixin Network suspends operations following $200 million hack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Mixin Network, an open-source, peer-to-peer transactional network for digital assets, has announced today on Twitter that deposits and withdrawals are...
Fake celebrity photo leak videos flood TikTok with Temu referral codes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams TikTok is flooded with videos promoting fake nude celebrity photo leaks used to push referral rewards for the Temu online...
New stealthy and modular Deadglyph malware used in govt attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A novel and sophisticated backdoor malware named ‘Deadglyph’ was seen used in a cyberespionage attack against a government agency in...
“The good and the bad that comes with the growth of AI” – watch this series of webinars with Abnormal, OpenAI, and others – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Graham Cluley Security News is sponsored this week by the folks at Abnormal. Thanks to the great team there for...
iOS 17 update secretly changed your privacy settings; here’s how to set them back – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Many iPhone users who upgraded their iPhones to the recently-released iOS 17 will be alarmed to hear that they may...
Axiad and Okta Partner to Revolutionize Authentication with Phishing Resistant MFA – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axiad Passwords present several pain points, both from a security and usability standpoint. Malicious actors can use a compromised set of credentials...
Cyber Week 2023 & The Israel National Cyber Directorate Presents – Watch Live: Cyber – Week 2023 – Main Plenary, Day 2 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/cyber-week-2023-the-israel-national-cyber-directorate-presents-watch-live-cyber-week-2023-main-plenary-day-2/ Category & Tags: CISO Suite,Governance, Risk &...
Data Breaches from MOVEit Zero-Day Still Piling Up – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Cybercrime groups exploiting the zero-day flaw in the MOVEit managed file transfer software linked to the Cl0p ransomware gang continue...
Unlock Cyber Security as a Service: 2023 Insights! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Toback Introduction In today’s rapidly evolving digital world, the significance of robust cybersecurity mechanisms cannot be overstated. This is especially true...
More iOS Zero Days, More Mercenary Spyware — This Time: Cytrox Predator – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Egyptian opposition presidential candidate Ahmed Eltantawy targeted “by the government.” Would-be president pwned by President: Former Egyptian politician Ahmed Tantawy (pictured)...