Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are utilizing a new trick of using zero-point fonts in emails to make malicious emails appear as safely scanned...
Day: September 26, 2023
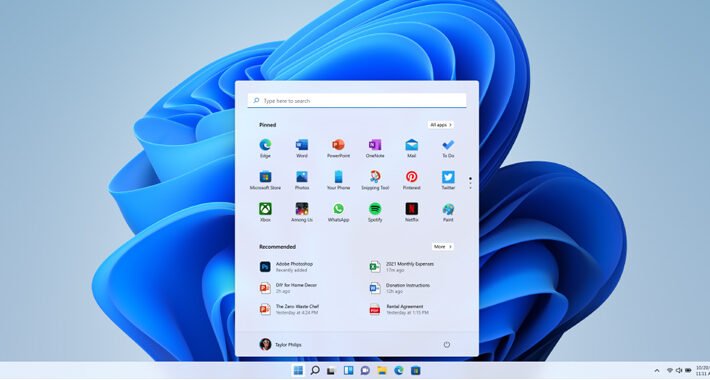
Windows 11’s new ‘Never Combine’ icons feature is almost usable – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams After almost three years, Microsoft has finally added the ‘Never combine taskbar button’ back to Windows, and it still doesn’t...
Sony investigates cyberattack as hackers fight over who’s responsible – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Sony says that it is investigating allegations of a cyberattack this week as different hackers have stepped up to claim responsibility for...
Windows 11 23H2 now rolling out to Release Preview Insiders – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has started rolling out the next major version of its operating system, Windows 11 23H2, to Insiders enrolled in...
Windows 11 KB5030310 update adds recommended websites, fixes 24 issues – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has released the September 2023 preview update for Windows 11, version 22H2, which adds frequently visited websites to the...
Windows 11 ‘Moment 4’ update released, here are the many new features – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has released the Windows 11 22H2 ‘Moment 4’ update, bringing 150 new features, including new AI-powered versions of Paint,...
Windows 11 22H2 adds a built-in passkey manager for Windows Hello – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Today’s Windows 11 update includes several security improvements, including a new passkeys management dashboard designed to help users go passwordless...
Google assigns new maximum rated CVE to libwebp bug exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google has assigned a new CVE ID (CVE-2023-5129) to a libwebp security vulnerability exploited as a zero-day in attacks and...
New AtlasCross hackers use American Red Cross as phishing lure – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new APT hacking group named ‘AtlasCross’ targets organizations with phishing lures impersonating the American Red Cross to deliver backdoor...
Hackers actively exploiting Openfire flaw to encrypt servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are actively exploiting a high-severity vulnerability in Openfire messaging servers to encrypt servers with ransomware and deploy cryptominers. Openfire...
Microsoft is Rolling out Support for Passkeys in Windows 11 – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 26, 2023THNEndpoint Security / Password Microsoft is officially rolling out support for passkeys in Windows 11 today as part of...
ShadowSyndicate: A New Cybercrime Group Linked to 7 Ransomware Families – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity experts have shed light on a new cybercrime group known as ShadowSyndicate (formerly Infra Storm) that may have leveraged as...
Essential Guide to Cybersecurity Compliance – Source:thehackernews.com
Source: thehackernews.com – Author: . SOC 2, ISO, HIPAA, Cyber Essentials – all the security frameworks and certifications today are an acronym soup that can make...
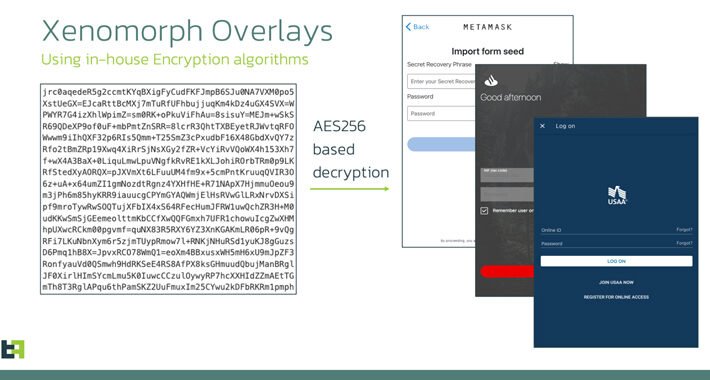
Xenomorph Banking Trojan: A New Variant Targeting 35+ U.S. Financial Institutions – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 26, 2023THNMobile Security / Malware An updated version of an Android banking trojan called Xenomorph has set its sights on...
Threat Report: The High Tech Industry Targeted the Most with 46% of NLX-Tagged Attack Traffic – Source:thehackernews.com
Source: thehackernews.com – Author: . How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your industry Gain...
4 Pillars for Building a Responsible Cybersecurity Disclosure Program – Source: www.darkreading.com
Source: www.darkreading.com – Author: Omer Cohen, CISO, Descope Software vulnerabilities are a lot like landmines in a war zone: they’re hidden in plain sight, seemingly everywhere,...
Chad Taps Huawei for Digital Modernization Project – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Chinese technology manufacturer Huawei has signed an agreement with Chad to build a national data center and technology...
Amidst MGM, Caesar’s Incidents, Attackers Focus on Luxury Hotels – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Even as the effects of the show-stopping cyberattacks on MGM Grand and Caesars are still being felt,...
Proactive Security: What It Means for Enterprise Security Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Eric Parizo, Principal Analyst, Omdia Automotive icon Henry Ford is credited with saying, “If you do what you’ve always done, you’ll get...
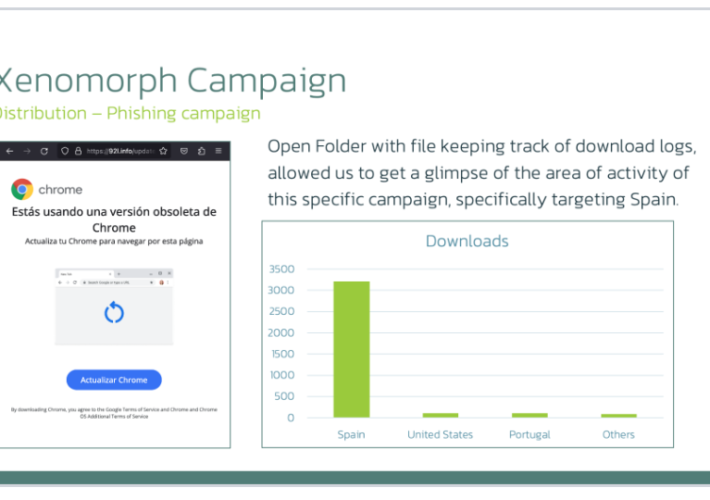
More than 30 US Banks Targeted in New Xenomorph Malware Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Xenomorph malware has reemerged in a new distribution campaign, expanding its scope to target over 30 US banks along with various...
ZenRAT Malware Uncovered in Bitwarden Impersonation – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new malware strain called ZenRAT has emerged, concealed within counterfeit Bitwarden installation packages. Discovered by Proofpoint, ZenRAT is a modular...
ShadowSyndicate Investigation Reveals RaaS Ties – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A recent collaborative investigation by Group-IB Threat Intelligence, Bridewell and threat researcher Michael Koczwara has exposed the existence of a new threat...
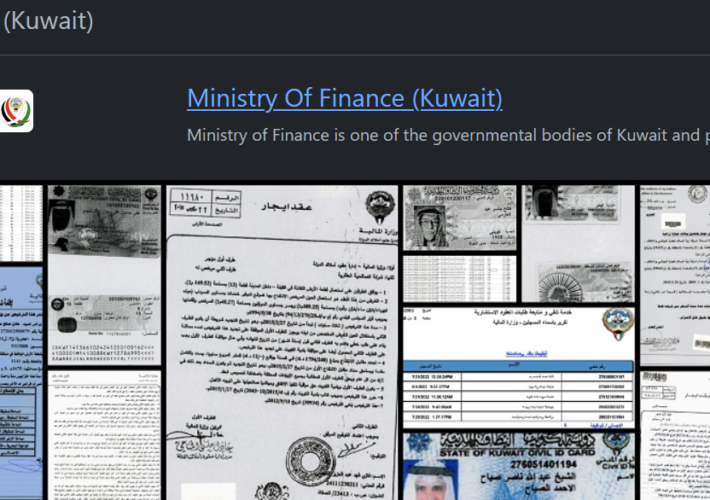
The Rhysida ransomware group hit the Kuwait Ministry of Finance – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Rhysida ransomware group hit the Kuwait Ministry of Finance Pierluigi Paganini September 26, 2023 This week the Rhysida ransomware...
BORN Ontario data breach impacted 3.4 million newborns and pregnancy care patients – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini BORN Ontario data breach impacted 3.4 million newborns and pregnancy care patients Pierluigi Paganini September 26, 2023 The Better Outcomes...
Xenomorph malware is back after months of hiatus and expands the list of targets – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Xenomorph malware is back after months of hiatus and expands the list of targets Pierluigi Paganini September 26, 2023 A...
Smishing Triad Stretches Its Tentacles into the United Arab Emirates – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Smishing Triad Stretches Its Tentacles into the United Arab Emirates Pierluigi Paganini September 26, 2023 Resecurity research found that the...
Crooks stole $200 million worth of assets from Mixin Network – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Crooks stole $200 million worth of assets from Mixin Network Pierluigi Paganini September 25, 2023 Crooks stole $200 million from...
A phishing campaign targets Ukrainian military entities with drone manual lures – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A phishing campaign targets Ukrainian military entities with drone manual lures Pierluigi Paganini September 25, 2023 A phishing campaign targets...
London Cybersecurity Summit Spotlights AI and Ransomware – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Fraud Management & Cybercrime , Leadership & Executive Communication Experts Emphasize Proactive Security Measures and...
Deadglyph Backdoor Targeting Middle Eastern Government – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Backdoor Is Associated With Stealth Falcon APT Group Prajeet Nair (@prajeetspeaks) •...