Source: www.govinfosecurity.com – Author: 1 Critical Infrastructure Security , Cybersecurity Spending , Government Annual Federal Funding Will Expire in 12 Days Marianne Kolbasuk McGee (HealthInfoSec) •...
Day: September 19, 2023
Journey to the Cloud: Navigating the Transformation – Part 2 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Security Operations Nikko Asset Management’s Marcus Rameke on the Advantages of HCI On-Premises CyberEdBoard • September 19, 2023...
Generative AI: Embrace It, But Put Up Guardrails – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance Cisco’s Pam Lindemoen and Daniel...
Why Entities Should Review Their Online Tracker Use ASAP – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Healthcare , HIPAA/HITECH Nick Heesters of HHS OCR on the Agency’s Top Areas of HIPAA Scrutiny...
CrowdStrike to Buy AppSec Startup Bionic for Reported $350M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Security Operations Deal Will Offer Visibility Into Application Behavior, Vulnerability Prioritization Michael Novinson (MichaelNovinson) • September 19, 2023...
CrowdStrike to Acquire Application Intelligence Startup Bionic – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Cybersecurity vendor CrowdStrike on Tuesday announced plans to acquire Bionic, a Silicon Valley startup selling tools in the Application Security...
HiddenLayer Raises Hefty $50M Round for AI Security Tech – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Texas startup HiddenLayer has bagged a hefty $50 million in new venture capital funding as investors continue to pour money...
Venafi Leverages Generative AI to Manage Machine Identities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Machine identity firm Venafi has launched a proprietary generative AI (gen-AI) model to help with the mammoth, complex, and expanding...
‘Cybersecurity Incident’ Hits ICC – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP The International Criminal Court said Tuesday it had been affected by what it called “anomalous activity” regarding its IT systems and...
Clorox Blames Damaging Cyberattack for Product Shortage – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Cleaning products manufacturer Clorox says the recent cyberattack has been contained, but production is still not fully restored and some...
Alcion Raises $21 Million for Backup-as-a-Service Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Data management startup Alcion today announced that it has raised $21 million in a Series A funding round that brings...
Pakistani APT Uses YouTube-Mimicking RAT to Spy on Android Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Pakistan-linked state-sponsored threat actor Transparent Tribe has been observed using new versions of the CapraRAT Android trojan that mimic the...
Thousands of Juniper Appliances Vulnerable to New Exploit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat intelligence firm VulnCheck has published details on a new exploit targeting a recent Junos OS vulnerability and says that...
Trend Micro Patches Exploited Zero-Day Vulnerability in Endpoint Security Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Trend Micro on Tuesday released an advisory to warn customers that a critical vulnerability affecting Apex One and other endpoint...
Hacker Conversations: Casey Ellis, Hacker and Ringmaster at Bugcrowd – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend In this edition of Hacker Conversations, SecurityWeek talks to Casey Ellis, founder, chairman and CTO at Bugcrowd – and hacker....
ShroudedSnooper’s HTTPSnoop Backdoor Targets Middle East Telecom Companies – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 19, 2023THNMalware / Cyber Threat Telecommunication service providers in the Middle East are the target of a new intrusion set...
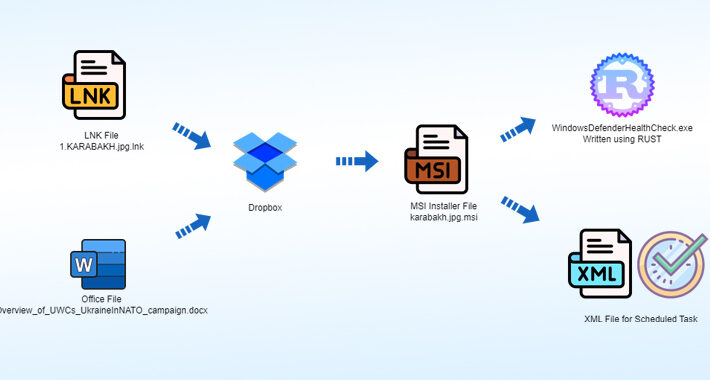
Operation Rusty Flag: Azerbaijan Targeted in New Rust-Based Malware Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 19, 2023THNCyber Attack / Threat Intel Targets located in Azerbaijan have been singled out as part of a new campaign...
Inside the Code of a New XWorm Variant – Source:thehackernews.com
Source: thehackernews.com – Author: . XWorm is a relatively new representative of the remote access trojan cohort that has already earned its spot among the most...
Earth Lusca’s New SprySOCKS Linux Backdoor Targets Government Entities – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 19, 2023THNEndpoint Security / Malware The China-linked threat actor known as Earth Lusca has been observed targeting government entities using...
Hackers breached International Criminal Court’s systems last week – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The International Criminal Court (ICC) disclosed a cyberattack on Tuesday after discovering last week that its systems had been breached....
GitLab urges users to install security updates for critical pipeline flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas GitLab has released security updates to address a critical severity vulnerability that allows attackers to run pipelines as other users...
Microsoft to start retiring Exchange Web Services in October 2026 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft said today that the Exchange Web Services (EWS) API for Exchange Online and Office 365 will be retired in approximately...
Hackers backdoor telecom providers with new HTTPSnoop malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas New malware named HTTPSnoop and PipeSnoop are used in cyberattacks on telecommunication service providers in the Middle East, allowing threat...
#mWISE: Chinese Cyber Power Bigger Than the Rest of the World Combined – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 While most people won’t be surprised to hear that China is investing heavily in cybersecurity, the extent of the country’s cyber...
Chinese Group Exploiting Linux Backdoor to Target Governments – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Chinese-linked threat actor known as ‘Earth Lusca’ has been conducting cyber espionage campaigns against governments around the world via a...
#mWISE: FBI Director Urges Greater Private-Public Collaboration Against Cybercrime – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 “I’m here to recruit you.” Was Christopher Wray, director of the FBI, really joking when he said that hiring people for...
7 dynamic cloud security trends that you can’t afford to miss – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the past year, 80% of organizations have encountered a major cloud-based cyber threat. To limit risk and to...
Threat Actor Claims Major TransUnion Data Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A notorious threat actor linked to previous big-name breaches has released several gigabytes of personal data stolen from credit agency TransUnion,...
Clorox Struggling to Recover From August Cyber-Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading US manufacturer of cleaning products has admitted its operations are still experiencing major disruption after the firm experienced a...
Microsoft AI Researchers Leak 38TB of Private Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft accidentally revealed a huge trove of sensitive internal information dating back over three years via a public GitHub repository, it...