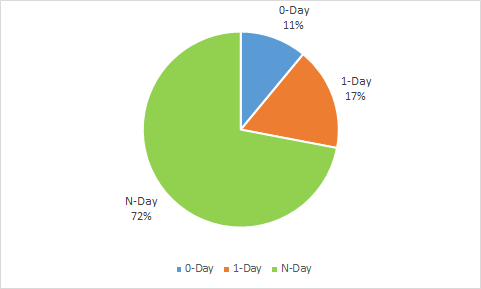
Source: securityboulevard.com – Author: NSFOCUS Recently, NSFOCUS SOC team summarized the findings from attack and defense drills in the first half of 2023. In these smokeless...
Day: September 12, 2023
Ekran System to Exhibit at it-sa Expo&Congress 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: yana.storchak@apriorit.com Ekran System will participate in the upcoming it-sa Expo&Congress 2023 in Nuremberg, Germany. The event takes place October 10–12, 2023, at...
A Comprehensive Guide to User Access Review: Best Practices and Pitfalls – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wesley Van Zyl, Senior Compliance Success Manager, Scytale We say it all the time; your employees are your first line of defense;...
Data Breach of AP Stylebook Leads to Phishing Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Users of the AP Stylebook have been targeted in phishing campaigns by bad actors using personal information stolen in a...
Ransomware: It Takes A Village, Says NCSC – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware UK Crime and Cybersecurity Agencies Urge ‘Holistic’ View of Ransomware Ecosystem Akshaya Asokan (asokan_akshaya) •...
Root Admin User: When Do Common Usernames Pose a Threat? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Access Management Honeypot Hits Reinforce Need for Strong Passwords and Multifactor Authentication Mathew J. Schwartz (euroinfosec) • September 11, 2023 ...
Judge Gives Green Light to Meta Pixel Web Tracker Lawsuit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Governance & Risk Management , Healthcare Judge Dismisses Some Plaintiff Claims But Allows Proposed Class Action...
DarkGate Malware Operators on a Phishing Spree – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Vectors Includes Teams Phishing and Malvertising Mihir Bagwe (MihirBagwe) • September 11, 2023 ...
Navigating PAM Implementation Risks: A Comprehensive Guide for CISOs – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa Chief Information Security Officers (CISOs) bear the responsibility of safeguarding their organizations against an ever-evolving array of cyber threats. Among...
What Is Token-Based Authentication? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Antonia Din Secured authentication to databases and systems is essential to enterprise cybersecurity management. According to the 2023 Data Breach Investigations Report,...