Source: thehackernews.com – Author: . Sep 12, 2023THNSoftware Security / Vulnerability A new vulnerability disclosed in GitHub could have exposed thousands of repositories at risk of...
Day: September 12, 2023
Check Point: Hackers Are Dropping USB Drives at Watering Holes – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Timon/Adobe Stock In its 2023 Mid-Year Cyber Security Report, Check Point Software spotlighted numerous exploits so far this year,...
Windows 10 and 11 in S Mode: What Is It and Should You Use It? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Mary Branscombe Pros of Windows in S mode Cons of Windows in S mode Additional security measures. Easier management of widespread enterprise...
Dreamforce 2023: Salesforce Expands Einstein AI and Data Cloud Platform – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Image: Sundry Photography/Adobe Stock Salesforce announced a rebrand of its Einstein 1 Data Cloud and new capabilities for the Einstein...
Want a New Job? Explore Opportunities at the 10 Top US Startup Ecosystems – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Amply on September 12, 2023, 4:24 AM EDT Want a New Job? Explore Opportunities at the 10 Top US Startup Ecosystems Written...
IT Staff Systems and Data Access Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: IT professionals, such as system and network administrators, help desk staff, management personnel and sometimes external vendor representatives, are routinely provided full...
Patch Management Policy: A Practical Guide – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu This post is also available in: Danish Patching, a highly necessary, yet sometimes neglected practice of resolving security risks related...
Ragnar Locker Claims Israel Hospital Cyberattack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The Ragnar Locker ransomware gang claims responsibility for the cyberattack on Mayanei Hayeshua hospital from Israel. The incident occurred in...
Free Download Manager backdoored – a possible supply chain attack on Linux machines – Source: securelist.com
Source: securelist.com – Author: Georgy Kucherin, Leonid Bezvershenko Over the last few years, Linux machines have become a more and more prominent target for all sorts...
Free Download Manager site redirected Linux users to malware for years – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A reported Free Download Manager supply chain attack redirected Linux users to a malicious Debian package repository that installed information-stealing...
Apple backports BLASTPASS zero-day fix to older iPhones – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Apple released security updates for older iPhones to fix a zero-day vulnerability tracked as CVE-2023-41064 that was actively exploited to...
Why Network Visibility Doesn’t Have to be so Complicated – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Firewalla Cybersecurity has become a core priority in the business world and, as Internet of Things (IoT) devices proliferate, home...
‘Redfly’ hackers infiltrated power supplier’s network for 6 months – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An espionage threat group tracked as ‘Redfly’ hacked a national electricity grid organization in Asia and quietly maintained access to...
World Security Report Finds Physical Security Incidents Cost Companies USD $1T in 2022 – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 IRVINE, Calif. — Sept. 11, 2023 — According to the first-ever World Security Report, large, global companies lost a combined $1 trillion in revenue in...
Google and Acalvio Partner to Deliver Active Defense to Protect Customers From Advanced Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Security is a top priority for all customers on Google Cloud, whether beginner, intermediate, or advanced users. Through our partnership with...
Cloudflare Announces Unified Data Protection Suite to Address Risks of Modern Coding and Increased AI Use – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 San Francisco, CA, September 7, 2023 – Cloudflare, Inc. (NYSE: NET), the security, performance, and reliability company helping to build a better Internet, today...
Iran’s Charming Kitten Pounces on Israeli Exchange Servers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading In the last two years, an Iranian state-backed threat actor has breached 32 Israeli organizations running...
Being Flexible Can Improve Your Security Posture – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joshua Goldfarb, Security and Fraud Architect, F5 Recently, I was working on a specific task. About an hour into the task, I...
‘Steal-It’ Campaign Uses OnlyFans Models as Lures – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A sophisticated cyber campaign is using images of OnlyFans models and geofencing to target specific victims across...
Cars Have Terrible Data Privacy – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Cars Have Terrible Data Privacy A new Mozilla Foundation report concludes that cars, all of them, have terrible data...
On Robots Killing People – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The robot revolution began long ago, and so did the killing. One day in 1979, a robot at a Ford...
7 Steps to Kickstart Your SaaS Security Program – Source:thehackernews.com
Source: thehackernews.com – Author: . SaaS applications are the backbone of modern businesses, constituting a staggering 70% of total software usage. Applications like Box, Google Workplace,...
Chinese Redfly Group Compromised a Nation’s Critical Grid in 6-Month ShadowPad Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 12, 2023THNCritical Infrastructure Security A threat actor called Redfly has been linked to a compromise of a national grid located...
Sophisticated Phishing Campaign Deploying Agent Tesla, OriginBotnet, and RedLine Clipper – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 12, 2023THNEndpoint Security / Malware A sophisticated phishing campaign is using a Microsoft Word document lure to distribute a trifecta...
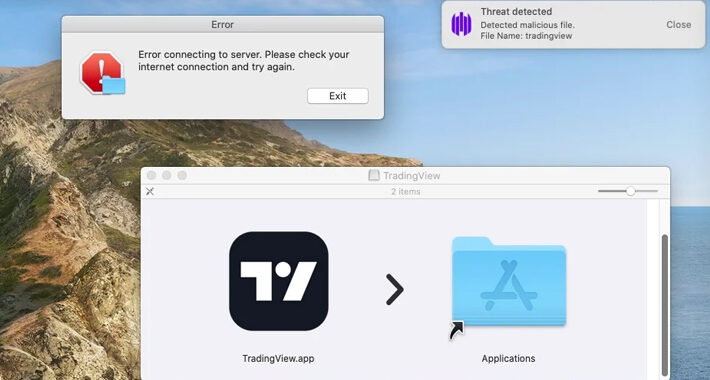
Beware: MetaStealer Malware Targets Apple macOS in Recent Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 12, 2023THNEndpoint Security / Data Security A new information stealer malware called MetaStealer has set its sights on Apple macOS,...
Google Rushes to Patch Critical Chrome Vulnerability Exploited in the Wild – Update Now – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 12, 2023THNBrowser Security / Zero Day Google on Monday rolled out out-of-band security patches to address a critical security flaw...
Ransomware: It Takes A Village, Says NCSC – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware UK Crime and Cybersecurity Agencies Urge ‘Holistic’ View of Ransomware Ecosystem Akshaya Asokan (asokan_akshaya) •...
Root Admin User: When Do Common Usernames Pose a Threat? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Access Management Honeypot Hits Reinforce Need for Strong Passwords and Multifactor Authentication Mathew J. Schwartz (euroinfosec) • September 11, 2023 ...
Judge Gives Green Light to Meta Pixel Web Tracker Lawsuit – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Governance & Risk Management , Healthcare Judge Dismisses Some Plaintiff Claims But Allows Proposed Class Action...
DarkGate Malware Operators on a Phishing Spree – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Vectors Includes Teams Phishing and Malvertising Mihir Bagwe (MihirBagwe) • September 11, 2023 ...