Source: www.bleepingcomputer.com – Author: Mayank Parmar The highly anticipated Windows 11 23H2 update is around the corner, and Microsoft has released its best features to testers...
Day: September 3, 2023
University of Sydney data breach impacts recent applicants – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The University of Sydney (USYD) announced that a breach at a third-party service provider exposed personal information of recently applied...
Microsoft reminds users Windows will disable insecure TLS soon – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft reminded users that insecure Transport Layer Security (TLS) 1.0 and 1.1 protocols will be disabled soon in future Windows...
Children’s snack recalled after its website caught serving porn – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Supermarket chain Lidl has been recalling four types of PAW Patrol-themed snacks across the UK. Except, the reason for the...
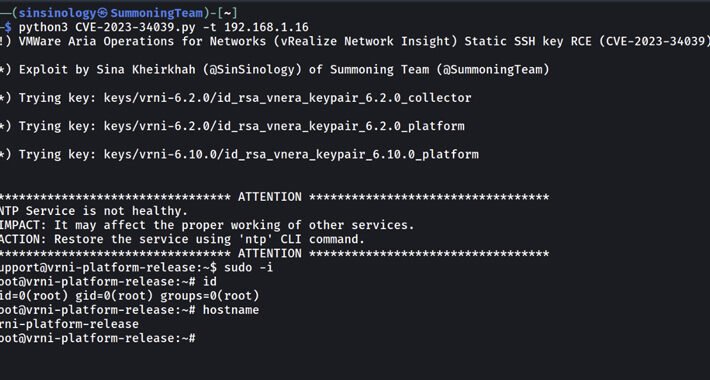
PoC exploit code released for CVE-2023-34039 bug in VMware Aria Operations for Networks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini PoC exploit code released for CVE-2023-34039 bug in VMware Aria Operations for Networks Pierluigi Paganini September 03, 2023 Researcher released...
Security Affairs newsletter Round 435 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
LockBit ransomware gang hit the Commission des services electriques de Montréal (CSEM) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini LockBit ransomware gang hit the Commission des services electriques de Montréal (CSEM) Pierluigi Paganini September 03, 2023 The LockBit ransomware...
Hackers Adding More Capabilities to Open Source Malware – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Application Security , Governance & Risk Management SapphireStealer Enables Hackers to Steal Sensitive Corporate Credentials Prajeet...
Freecycle users told to change passwords after data breach – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Freecycle, an online community that encourages sharing unwanted items with eachother than chucking them in the bin or taking them...
PoC Exploit Released for Critical VMware Aria’s SSH Auth Bypass Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 03, 2023THNNetwork Security / Vulnerability Proof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical...
Fake Signal and Telegram apps – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET research uncovers active campaigns targeting Android users and spreading espionage code through the Google Play store, Samsung Galaxy Store and dedicated...
What you need to know about iCloud Private Relay – Source:
Source: – Author: 1 If you want to try to enter the world of VPNs with a small dip, then iCloud Private Relay is your friend...
BadBazaar espionage tool targets Android users via trojanized Signal and Telegram apps – Source:
Source: – Author: 1 ESET researchers have discovered active campaigns linked to the China-aligned APT group known as GREF, distributing espionage code that has previously targeted...
Recovering from a supply-chain attack: What are the lessons to learn from the 3CX hack? – Source:
Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 2
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 13
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 15
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 16
Chrome extensions can steal plaintext passwords from websites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A team of researchers from the University of Wisconsin-Madison has uploaded to the Chrome Web Store a proof-of-concept extension that can...
Fake YouPorn extortion scam threatens to leak your sex tape – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A new sextortion scam is making the rounds that pretends to be an email from the adult site YouPorn, warning...
Yes, there’s an npm package called @(-.-)/env and some others like it – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Strangely named npm packages like -, @!-!/-, @(-.-)/env, and –hepl continue to exist on the internet’s largest software registry. While not all of...
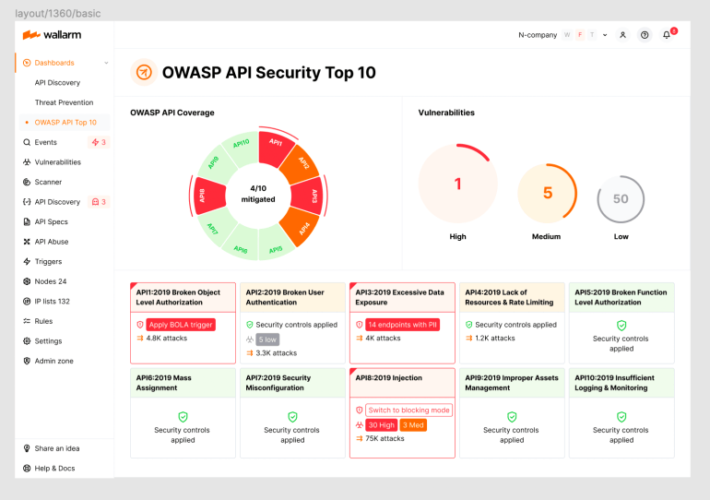
2023 OWASP Top-10 Series: API6:2023 Unrestricted Access to Sensitive Business Flows – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Welcome to the 7th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...
MSP Vs MSSP is there a distinction anymore? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Luby MSP v MSSP – is there a distinction anymore? Well, yes and no. Yes there’s a distinction because if you...