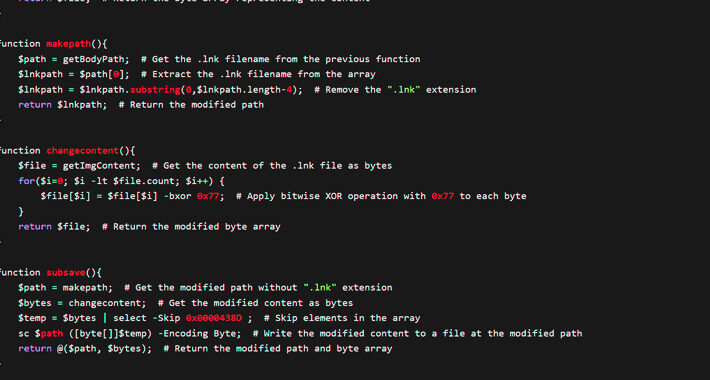
Source: www.bleepingcomputer.com – Author: Bill Toulas Forever 21 clothing and accessories retailer is sending data breach notifications to more than half a million individuals who had...
Day: September 1, 2023
Sophisticated Cyber-Espionage Group Earth Estries Exposed – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A sophisticated cyber-espionage group named “Earth Estries” has been exposed by cybersecurity firm Trend Micro. Operating since at least 2020, the group...
Adobe ColdFusion Critical Vulnerabilities Exploited Despite Patches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Fortinet has observed significant threat exploitation targeting Adobe ColdFusion, a web development computing platform. This is despite a series of security...
Russian State-Backed ‘Infamous Chisel’ Android Malware Targets Ukrainian Military – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity and intelligence agencies from Australia, Canada, New Zealand, the U.K., and the U.S. on Thursday disclosed details of a mobile...
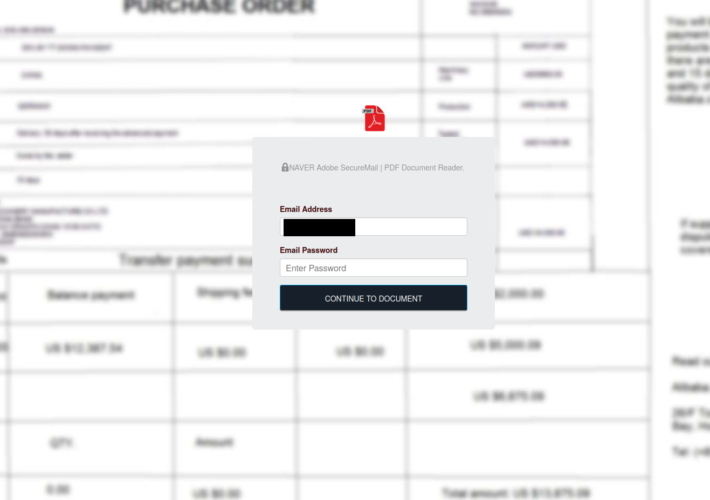
New SuperBear Trojan Emerges in Targeted Phishing Attack on South Korean Activists – Source:thehackernews.com
Source: thehackernews.com – Author: . A new phishing attack likely targeting civil society groups in South Korea has led to the discovery of a novel remote...
It’s a Zero-day? It’s Malware? No! It’s Username and Password – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 01, 2023The Hacker NewsUnified Identity Protection As cyber threats continue to evolve, adversaries are deploying a range of tools to...
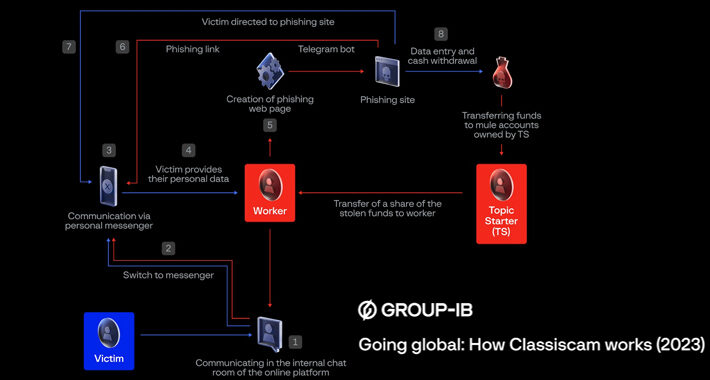
Classiscam Scam-as-a-Service Raked $64.5 Million During the COVID-19 Pandemic – Source:thehackernews.com
Source: thehackernews.com – Author: . The Classiscam scam-as-a-service program has reaped the criminal actors $64.5 million in illicit earnings since its emergence in 2019. “Classiscam campaigns...
68k Phishing Victims are Now Searchable in Have I Been Pwned, Courtesy of CERT Poland – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Last week I was contacted by CERT Poland. They’d observed a phishing campaign that had collected 68k credentials from unsuspecting...
National Cybersecurity Alliance Receives 200K Grant From Craig Newmark Philanthropies for HBCU Cybersecurity Program – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 August 28, 2023- WASHINGTON – The National Cybersecurity Alliance (NCA) today announced it has received a significant boost in funding from Craig...
Cygna Labs Corp. Announces Expansion of its DNS Firewall Service – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 MIAMI, Aug. 31, 2023 /PRNewswire-PRWeb/ — Cygna Labs , a highly specialized software developer with a focus on providing enterprises worldwide and a leading provider...
Introducing SafeUTM: The Free Version of NGFW – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ALEXANDRIA, Va., Aug. 31, 2023 /PRNewswire/ — SafeUTM, a product with a new approach and a player in the network security field of...
3 out of 4 Cyberattacks in the Education Sector Are Associated With a Compromised On‑Premises User or Admin Account – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 FRISCO, Texas, Aug. 31, 2023 /PRNewswire/ — Netwrix, a cybersecurity vendor that makes data security easy, today revealed additional findings for the education sector from its...
UN: Southeast Asia Gangs Are Trafficking Cybercrime Workers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A new report released by the United Nations regarding online scam operations in Southeast Asia details the...
Insurance Costs Rise, Coverage Shrinks, but Policies Remain Essential – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Companies need to reassess their cyber insurance policies as significant breaches and growing payouts have led...
Cybercriminals Team Up to Upgrade ‘SapphireStealer’ Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Cybercriminals are mining the capabilities of an open source infostealer called “SapphireStealer,” developing a legion of variants that are helping...
UK Agrees to Support Kuwait’s Cybersecurity Center – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The governments of the United Kingdom and Kuwait have agreed on a deal whereby the UK will...
Another data breach at Forever 21 leaks details of 500,000 current and former employees – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Fashion chain Forever 21 has suffered what it has described as a “data security incident” that saw a hacker gain...
Paramount, Forever 21 Data Breaches Set Stage for Follow-on Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A pair of breaches have hit media giant Paramount Global and fashion purveyor Forever 21,...
Apple iPhone 14 Pro Offered Up to the Hacking Masses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Apple has designated the iPhone 14 Pro as the target device to be used for research conducted in...
BadBazaar espionage tool targets Android users via trojanized Signal and Telegram apps – Source:
Source: – Author: 1 ESET researchers have discovered active campaigns linked to the China-aligned APT group known as GREF, distributing espionage code that has previously targeted...
Recovering from a supply-chain attack: What are the lessons to learn from the 3CX hack? – Source:
Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 2
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 15
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....