Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at Sophos X-Ops have uncovered a wave of attacks targeting unpatched Citrix NetScaler systems exposed to the internet. Describing...
Month: August 2023
Mom’s Meals Warns of Major Data Breach Affecting Over 1.2 Million Individuals – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Mom’s Meals, a medical meal delivery service operated by PurFoods in the U.S., has alerted its users about a significant...
How to Manage XDR Alerts with Heimdal – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Adelina Deaconu Heimdal XDR offers you full visibility into network traffic, user behavior, and endpoint activity. It makes investigating threats much easier,...
Nordic Users Targeted by National Danish Police Phishing Attack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Vladimir Unterfingher A new type of cyber-attack is currently spreading like wildfire in the Nordics, targeting email addresses indiscriminate of user profiles...
How to Implement an XDR Software? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Traditional security solutions are no longer enough to protect your business from sophisticated attacks. As a cybersecurity professional, you have...
Eggs-cellent email: How cooking with eggs showcases the promise & peril of email security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Jeremy Fuchs is the Content Marketing Specialist for Harmony Email & Collaboration. Previously, he worked at Avanan, which was acquired by...
10 SASE benefits that you should be aware of – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The Secure Access Service Edge (SASE) framework emerged in 2019, as industry analysts observed new use cases and buying...
GUEST ESSAY: Where we stand on mitigating software risks associated with fly-by-wire jetliners – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Vance Hilderman The threat of bad actors hacking into airplane systems mid-flight has become a major concern for airlines and...
Report Reveals Growing Disparity in Cyber Insurance Landscape – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Delinea’s 2023 State of Cyber Insurance Report has revealed a growing disconnect between carriers and enterprises seeking robust coverage. Insights from...
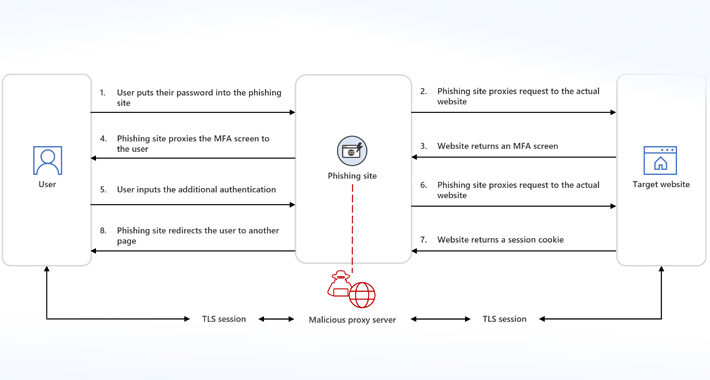
Microsoft Warns of Adversary-in-the-Middle Uptick on Phishing Platforms – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by Microsoft has observed a proliferation of adversary-in-the-middle (AiTM) techniques deployed through phishing-as-a-service (PhaaS) platforms, the company explained in a...
Four in Five Cyber-Attacks Powered by Just Three Malware Loaders – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity provider ReliaQuest observed that cyber-criminals used seven different malware loaders to deploy their intrusion campaigns in the first half of...
FIN8-linked actor targets Citrix NetScaler systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini FIN8-linked actor targets Citrix NetScaler systems A financially motivated actor linked to the FIN8 group exploits the CVE-2023-3519 RCE in...
Japan’s JPCERT warns of new ‘MalDoc in PDF’ attack technique – Source: securityaffairs.com
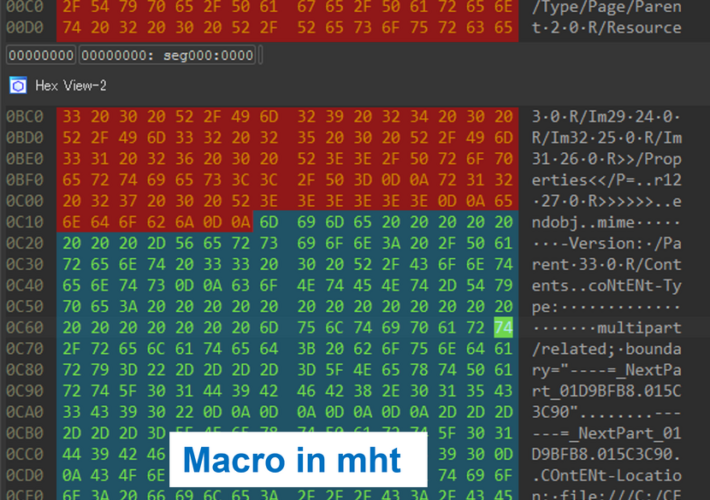
Source: securityaffairs.com – Author: Pierluigi Paganini Japan’s JPCERT warns of new ‘MalDoc in PDF’ attack technique Japan’s JPCERT warns of a new recently detected ‘MalDoc in...
Attackers can discover IP address by sending a link over the Skype mobile app – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Attackers can discover IP address by sending a link over the Skype mobile app A security researcher demonstrated how to...
Researchers published PoC exploit code for Juniper SRX firewall flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers published PoC exploit code for Juniper SRX firewall flaws Researchers published a PoC exploit code for Juniper SRX firewall...
Attacks on Citrix NetScaler systems linked to ransomware actor – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A threat actor believed to be tied to the FIN8 hacking group exploits the CVE-2023-3519 remote code execution flaw to...
MalDoc in PDFs: Hiding malicious Word docs in PDF files – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Japan’s computer emergency response team (JPCERT) is sharing a new ‘MalDoc in PDF’ attack detected in July 2023 that bypasses...
Microsoft will enable Exchange Extended Protection by default this fall – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft announced today that Windows Extended Protection will be enabled by default on servers running Exchange Server 2019 starting this...
Spain warns of LockBit Locker ransomware phishing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The National Police of Spain is warning of an ongoing ‘LockBit Locker’ ransomware campaign targeting architecture companies in the country...
Microsoft blames ‘unsupported processor’ blue screens on OEM vendors – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says the recent wave of blue screens impacting some Windows users is not caused by issues in its August...
Citrix NetScaler Alert: Ransomware Hackers Exploiting Critical Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 29, 2023The Hacker NewsVulnerability / Network Security Unpatched Citrix NetScaler systems exposed to the internet are being targeted by unknown...
Phishing-as-a-Service Gets Smarter: Microsoft Sounds Alarm on AiTM Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 29, 2023THNOnline Security / Cyber Threat Microsoft is warning of an increase in adversary-in-the-middle (AiTM) phishing techniques, which are being...
Motherboard Mishaps Undermine Trust, Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Microsoft’s latest Windows Preview appears to trigger a bug on some motherboards made by computer hardware...
BreachLock Intelligence Report Reveals Critical Insights From Thousands of Penetration Tests – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 NEW YORK, Aug. 28, 2023 /PRNewswire/ — BreachLock, the global leader in Penetration Testing Services, announces the release of its highly anticipated 2023 BreachLock Penetration Testing Intelligence...
Cybercriminals Harness Leaked LockBit Builder in Wave of New Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Threat actors are using and customizing leaked Lockbit code to carry out their own ransomware attacks....
Considerations for Reducing Risk When Migrating to the Cloud – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Sadowski, Director, Trust & Security Product Marketing for Google Cloud at Google The moment your organization begins planning for a cloud...
Financial Firms Breached in MOVEit Cyberattacks Now Face Lawsuits – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Financial services companies breached as a result of MOVEit zero-day vulnerability are facing a flurry of class...
London Police Warned to Stay Vigilant Amid Major Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Greater London’s Metropolitan Police have been warned that their information — names, ranks, ID numbers, vetting levels,...
5 Ways to Prepare for Google’s 90-Day TLS Certificate Expiration – Source: www.darkreading.com
Source: www.darkreading.com – Author: Murali Palanisamy, Chief Solutions Officer, AppViewX Digital certificates are not like fine wine — they don’t get better with age. They’re more...
Authentication Outage Underscores Why ‘Fail Safe’ Is Key – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading One week ago today, social media accounts for the information-system services at several universities and colleges...