Source: www.infosecurity-magazine.com – Author: 1 Threat actors have been observed using Amazon Web Services (AWS) ‘s System Manager (SSM) agent as a Remote Access Trojan (RAT)...
Month: August 2023
Cloud Firm Under Scrutiny For Suspected Support of APT Operations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The cloud firm Cloudzy has come under scrutiny for its alleged support of advanced persistent threat (APT) operations. In a new...
AI-Enhanced Phishing Driving Ransomware Surge – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Government agencies alongside education and healthcare organizations have become prime targets for ransomware operators over the past three years. According to...
Microsoft Exposes Russian Hackers’ Sneaky Phishing Tactics via Microsoft Teams Chats – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNCyber Attack / Phishing Microsoft on Wednesday disclosed that it identified a set of highly targeted social engineering attacks...
Researchers Discover Bypass for Recently Patched Critical Ivanti EPMM Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 03, 2023THNVulnerability / Software Security Cybersecurity researchers have discovered a bypass for a recently fixed actively exploited vulnerability in some...
Hackers already installed web shells on 581 Citrix servers in CVE-2023-3519 attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn that hundreds of Citrix servers have been hacked in an ongoing campaign exploiting the RCE CVE-2023-3519. Security researchers...
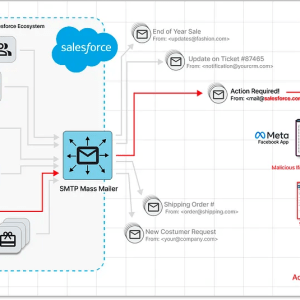
Zero-day in Salesforce email services exploited in targeted Facebook phishing campaign – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts spotted a spear-phishing Facebook campaign exploiting a zero-day vulnerability in Salesforce email services. Researchers from Guardio Labs uncovered a...
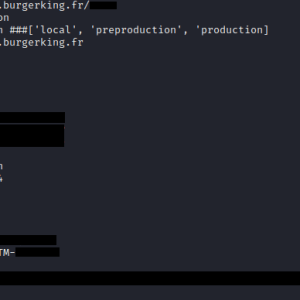
Burger King forgets to put a password on their systems, again – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The fast food giant Burger King put their systems and data at risk by exposing sensitive credentials to the public...
Fake FlipperZero sites promise free devices after completing offer – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A site impersonating Flipper Devices promises a free Flipper Zero after completing an offer but only leads to shady browser...
Ivanti discloses new critical auth bypass bug in MobileIron Core – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan IT software company Ivanti disclosed today a new critical security vulnerability in its MobileIron Core mobile device management software. Tracked...
Russian hackers target govt orgs in Microsoft Teams phishing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says a hacking group tracked as APT29 and linked to Russia’s Foreign Intelligence Service (SVR) targeted dozens of organizations...
Over 640 Citrix servers backdoored with web shells in ongoing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Hundreds of Citrix Netscaler ADC and Gateway servers have already been breached and backdoored in a series of attacks targeting...
New Collide+Power side-channel attack impacts almost all CPUs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new software-based power side-channel attack called ‘Collide+Power’ was discovered, impacting almost all CPUs and potentially allowing data to leak....
Slack down: Outage causing connection errors, blurry images – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Slack is investigating an ongoing incident preventing users from accessing the instant messaging platform and making shared images blurry for...
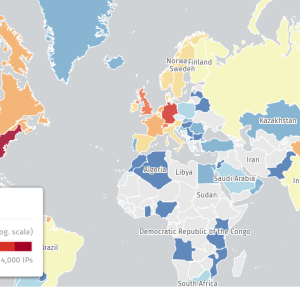
Amazon’s AWS SSM agent can be used as post-exploitation RAT malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Researchers have discovered a new post-exploitation technique in Amazon Web Services (AWS) that allows hackers to use the platform’s System...
Why Every Security Practitioner Should Attend mWISE – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Mandiant What’s in store for mWISE 2023? 80+ curated sessions. 90+ hand-picked speakers. 7 session tracks. All the hottest topics...
Hackers exploited Salesforce zero-day in Facebook phishing attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers exploited a zero-day vulnerability in Salesforce’s email services and SMTP servers to launch a sophisticated phishing campaign targeting valuable...
Third Party Security Requirements
The GE HealthCare Third-Party Cyber Security Requirements document outlines the cyber security requirements applicable to GEHC Third Parties, including suppliers and joint ventures. The security requirements...
Cado Security Report Surfaces Most Common Cyberattack Vectors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard An analysis of cyberattack patterns published by Cado Security, a provider of a cybersecurity forensics platform, found nearly every instance...
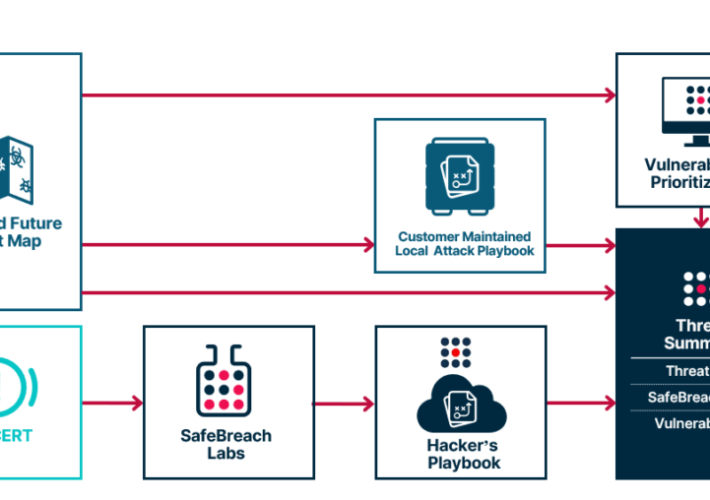
SafeBreach and Recorded Future: Operationalizing Threat Intelligence with Breach and Attack Simulation – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Modern enterprises have adopted more offensive measures to protect their organizations from evolving cyber threats. As a result, many security teams...
BSides Leeds 2023 – Sarah Young – Fantastic Cloud Security Mistakes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsides-leeds-2023-sarah-young-fantastic-cloud-security-mistakes/ Category & Tags: CISO Suite,Governance, Risk &...
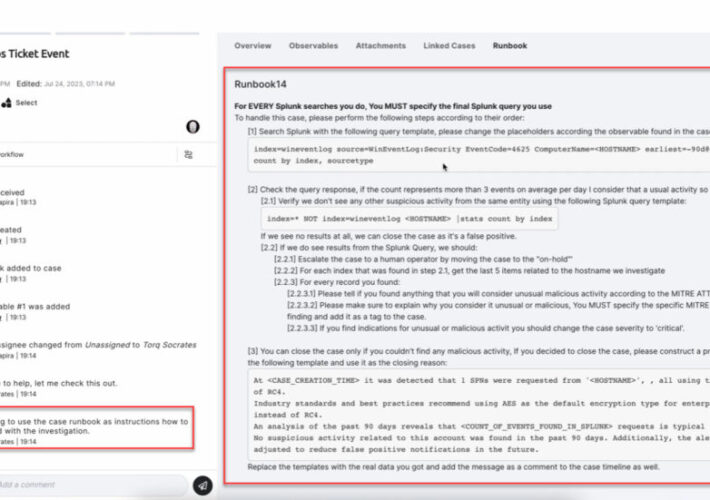
Torq Taps Generative AI to Automate SecOps Workflows – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Torq today announced it is injecting additional generative artificial intelligence (AI) capabilities into its platform for automating security operations (SecOps)...
The Business Value of Trustworthy Data: Beyond Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kimberly Rose Every decision and action that affects your business is only as good as the data that supports it. This means...
Challenges In Post-Exploitation Workflows – Source: securityboulevard.com
Source: securityboulevard.com – Author: Will Schroeder In our previous post, we talked about the problem of structured data in the post-exploitation community. We touched on the...
FraudGPT/WormGPT: Scammy for now — but a worrying signpost for software security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Dark web AI models that can phish and write malware have been exercising minds in recent weeks. But the so-called WormGPT...
TrustCloud & VanRein Compliance Partner to Make Compliance Accessible and Affordable – Source: securityboulevard.com
Source: securityboulevard.com – Author: Erin Crapser TrustCloud is thrilled to announce a partnership with VanRein Compliance, a leading managed compliance provider that builds and manages clients’...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #253 – Team Cognitive Overload – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, August 2, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Cloud Providers Becoming Key Players in Ransomware, Halcyon Warns – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt There are a number of components that make up a ransomware campaign, from the initial access brokers (IABs) to ransomware-as-a-service...
Ivanti Norway Hacks Began in April, Says US CISA – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Enterprise Mobility Management / BYOD Mobile Device Management Are ‘Attractive Targets,’ Warns Joint Advisory With Norway Mihir Bagwe...
Why Open Source License Management Matters – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security & Online Fraud , Fraud Management & Cybercrime Adam Murray • August 1, 2023 The ongoing rise...