Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Month: August 2023
The Dark Side of Microservices: How to Protect Your Data from Breach Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tomer Rozentzvaig Hello and welcome back to my blog series on the dark side of microservices. In the previous blog we discussed...
Authorities Warn Health Sector of Attacks by Rhysida Group – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific New Ransomware Group Branches Out, Hits Multiple Hospitals, Provider Networks Marianne Kolbasuk...
Critical Bugs Found in PaperCut Allow RCE – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Vulnerability Could Allow Attackers to Read, Delete or Upload Arbitrary Files Prajeet Nair (@prajeetspeaks)...
Spanish Police Arrest 3 Behind Payment Card Fraud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Card Not Present Fraud , Cybercrime , Fraud Management & Cybercrime Cybercrime Group Defrauded Nearly 200,000 Euros Akshaya Asokan (asokan_akshaya) •...
Nigerian Man Admits to $1.3M Business Email Compromise Scam – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Email Compromise (BEC) , Fraud Management & Cybercrime Scammers Used Malware and Spoofed Domain Name to Trick UK Financial Services...
Hackers increasingly abuse Cloudflare Tunnels for stealthy connections – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are increasingly abusing the legitimate Cloudflare Tunnels feature to create stealthy HTTPS connections from compromised devices, bypass firewalls, and...
Hands on with Windows 11’s new modern File Explorer – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar With the introduction of Windows 11 23H2, Microsoft has modernized File Explorer on Windows 11, bringing a fresher look and...
Google Play apps with 2.5M installs load ads when screen’s off – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Google Play store was infiltrated by 43 Android applications with 2.5 million installs that secretly displayed advertisements while a...
North Korean hackers ‘ScarCruft’ breached Russian missile maker – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The North Korean state-sponsored hacking group ScarCruft has been linked to a cyberattack on the IT infrastructure and email server...
Research Eyes Misconfiguration Issues At Google, Amazon and Microsoft Cloud – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on August 7, 2023, 2:43 PM EDT Research Eyes Misconfiguration Issues At Google, Amazon and Microsoft Cloud Qualys report looks...
ChatGPT Security Concerns: Credentials on the Dark Web and More – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Image: DIgilife/Adobe Stock As artificial intelligence technology such as ChatGPT continues to improve, so does its potential for misuse by...
How an 8-Character Password Could be Cracked in Just a Few Minutes – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Lance Whitney Advances in graphics processing technology and AI have slashed the time needed to crack a password using brute force techniques,...
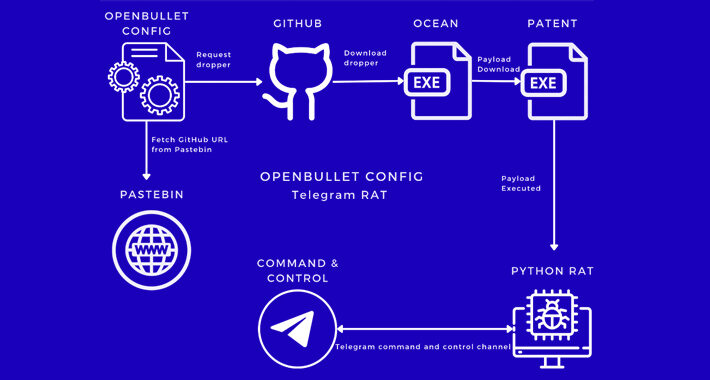
New Malware Campaign Targets Inexperienced Cyber Criminals with OpenBullet Configs – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 07, 2023THNCyber Crime / Malware A new malware campaign has been observed making use of malicious OpenBullet configuration files to...
North Korean Hackers Targets Russian Missile Engineering Firm – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 07, 2023THNCyber Attack Two different North Korean nation-state actors have been linked to a cyber intrusion against the major Russian...
Welcome to the New Have I Been Pwned Domain Search Subscription Service – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt This is a big one. A massive one. It’s the culmination of a solid 7 months of work that finally,...
Spanish Police Arrest 3 Behind Payment Card Fraud – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Card Not Present Fraud , Cybercrime , Fraud Management & Cybercrime Cybercrime Group Defrauded Nearly 200,000 Euros Akshaya Asokan (asokan_akshaya) •...
Colorado Warns Ransomware Attack Caused Massive Data Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Security Operations Information From 2004 to 2020 Exposed for High School Students, Teachers and Others Mathew J. Schwartz...
White House Pushes Cybersecurity Defense for K-12 Schools – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Fraud Management & Cybercrime , Government Educators Gird for Fresh Ransomware Attacks as Students Set to Return to...
New PaperCut Vulnerability Allows Remote Code Execution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Organizations have been warned about a new potentially serious vulnerability affecting the PaperCut NG/MF print management software. The flaw, tracked...
CISA Unveils Cybersecurity Strategic Plan for Next 3 Years – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The US Cybersecurity and Infrastructure Security Agency (CISA) has unveiled its Cybersecurity Strategic Plan for the next three years, focusing...
Colorado Department of Higher Education Discloses Ransomware Attack, Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Colorado Department of Higher Education (CDHE) has been targeted in a ransomware attack that resulted in a data breach...
US Primary Care Services Shuttered After Cyber-Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A widespread cyber-attack on hospital computer systems has caused significant disruptions across the United States, leading to the closure of emergency...
Invisible Ad Fraud Targets Korean Android Users – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts have discovered a new adware campaign specifically targeting Korean Android users. The discovery by McAfee’s Mobile Research Team shed...
FBI Warns Against Criminals Posing as NFT Developers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Federal Bureau of Investigation (FBI) has issued a warning concerning a growing wave of financial fraud within the Non-Fungible...
GUEST ESSAY: Why any sudden influx of spam emails is an indicator of a likely security issue – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Zac Amos We all get spam emails, and while it’s annoying, it’s not usually anything to worry about. However, getting...
Black Hat Fireside Chat: Horizon3.ai makes a strong case for continuous, self-service pentesting – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido LAS VEGAS — Penetration testing, traditionally, gave businesses a nice, pretty picture of their network security posture...
Russian Hacktivists Overwhelm Spanish Sites With DDoS – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading Spanish research institute has become the latest organization in the country to come under cyber-attack from Russia, after a...
Colorado Education Department Suffers Ransomware Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Former and current high school staff and students in Colorado have been put on notice that their personal information may have...
Clop Gang Offers Data Downloads Via Torrents – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Clop ransomware group has begun offering access to data stolen in MOVEit attacks via torrents, it has emerged. Security researcher...