Source: www.schneier.com – Author: Bruce Schneier Really interesting “systematization of knowledge” paper: “SoK: The Ghost Trilemma” Abstract: Trolls, bots, and sybils distort online discourse and compromise...
Month: August 2023
A CISO playbook: Elevating resilience through advanced paradigms – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Worried about the spectacular array of adversaries and threat methodologies extant in today’s vast cyber landscape? The CISO playbook, when it...
News alert: DigiCert extends cert management platform to support Microsoft CA, AWS Private CA – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Lehi, Utah, Aug. 8, 2023 – DigiCert today announced the expansion of its certificate management platform, DigiCert Trust Lifecycle Manager, to provide full lifecycle support for...
Multiple Flaws Found in the Avada WordPress Theme and Plugin – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Multiple vulnerabilities have been identified in the widely used Avada theme and its accompanying Avada Builder plugin. These security flaws, uncovered...
Lapsus$ Hacker Group Exposed in Latest CSRB Report – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Cyber Safety Review Board (CSRB) has issued a comprehensive report shedding light on the operations of the notorious extortion-focused...
DHS to Review Microsoft’s Security in Chinese Email Hack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Department of Homeland Security (DHS) has announced it will investigate Microsoft’s security practices in relation to the recent Chinese...
Downfall Vulnerability Affects Millions of Intel CPUs With Strong Data Leak Impact – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Learn technical details about this newly disclosed security vulnerability, as well as mitigation recommendations from the Google researcher who discovered...
Best Encryption Software and Tools for 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jonathan Kalibbala on August 11, 2023, 12:50 PM EDT Best Encryption Software and Tools for 2023 This is a comprehensive list of...
Black Hat 2023 Keynote: Navigating Generative AI in Today’s Cybersecurity Landscape – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Azaria Labs CEO and founder Maria Markstedter speaks at Black Hat 2023 in Las Vegas on Aug. 10, 2023. Image:...
Ransomware Prevention Kit – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Premium TechRepublic Premium Web Hosting Services Comparison Tool Whether your business is a well-established powerhouse or just barely getting off the...
Talk with a Ransomware Recovery Expert – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Premium TechRepublic Premium Web Hosting Services Comparison Tool Whether your business is a well-established powerhouse or just barely getting off the...
Overcome Ransomware with a Single Solution – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Premium TechRepublic Premium Web Hosting Services Comparison Tool Whether your business is a well-established powerhouse or just barely getting off the...
The Evolution of API: From Commerce to Cloud – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini API (or Application Programming Interface) is a ubiquitous term in the tech community today, and it’s one with a long...
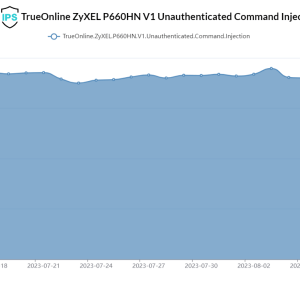
Gafgyt botnet is targeting EoL Zyxel routers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn that the Gafgyt botnet is actively exploiting a vulnerability impacting the end-of-life Zyxel P660HN-T1A router. A variant of...
Charming Kitten APT is targeting Iranian dissidents in Germany – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Germany’s Federal Office for the Protection of the Constitution (BfV) warns that the Charming Kitten APT group targeted Iranian dissidents...
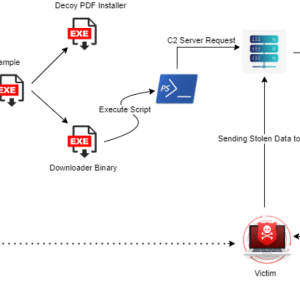
Statc Stealer, a new sophisticated info-stealing malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn that a new info-stealer named Statc Stealer is infecting Windows devices to steal a broad range of sensitive information. Zscaler...
CISA discovered a new backdoor, named Whirlpool, used in Barracuda ESG attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. Cybersecurity & Infrastructure Security Agency (CISA) observed a new backdoor, named Whirlpool, in attacks on Barracuda ESG appliances....
Privacy-invading LetMeSpy stalkerware announces it is shutting down after hack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley I doubt there will be many people shedding tears at the news that a stalkerware company has announced it is...
10,000 N Ireland police officers and staff have their details exposed after spreadsheet screw-up – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Earlier this week, the details of all 10,000 staff at the Police Service of Northern Ireland (PSNI) were exposed after...
Rhysida ransomware – what you need to know – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley What is Rhysida? Rhysida is a Windows-based ransomware operation that has come to prominence since May 2023, after being linked...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...