Source: www.darkreading.com – Author: Daniel dos Santos, Head of Security Research, Forescout’s Vedere Labs Routing protocols play a critical role in the functioning of the Internet...
Month: August 2023
Fastly Launches Certainly CA – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Edge cloud platform provider Fastly has announced the general availability of Certainly, its publicly trusted Transport Layer...
Confusion Surrounds SEC’s New Cybersecurity Material Rule – Source: www.darkreading.com
Source: www.darkreading.com – Author: Evan Schuman, Contributing Writer, Dark Reading One of the aims of the new cybersecurity disclosure rules approved by the Securities Exchange Commission...
Infoblox Blows Whistle On ‘Decoy Dog,’ Advocates For Better DNS Monitoring – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Renée Burton of Infoblox unveils the inner workings of Decoy Dog/Pupy, the RAT toolkit that uses the...
TXOne: How to Improve Your Operational Technology Security Posture – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading As operational technology (OT) gets more networked, these industrial networks are more prone to ransomware and supply...
Cribl, Exabeam Partner on Threat Detection, Investigation, and Response – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Abby Strong of Cribl and Chris Cesio of Exabeam talk about their companies’ recent partnership designed to...
Interpres: Getting the Most Out of Threat Intelligence Resources – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Nick Lantuh of Interpres talks about the shortcomings of the threat intel industry and how security pros...
Qualys Offers Threat Forecast For Cloud, and Tips For Reducing Cloud Risks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Sumedh Thakar of Qualys talks about how security vendors must translate cloud customer needs into effective solutions,...
Normalyze: How Focusing on Data Can Improve Cloud Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Normalyze’s Ravi Ithal deconstructs data security posture management (DPSM), how it differs from conventional data security management,...
White House Orders Federal Agencies to Bolster Cyber Safeguards – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The White House has ordered federal agencies to get their cybersecurity safeguards up to date as they...
Bots Are Better than Humans at Solving CAPTCHAs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting research: “An Empirical Study & Evaluation of Modern CAPTCHAs“: Abstract: For nearly two decades, CAPTCHAS have been widely used...
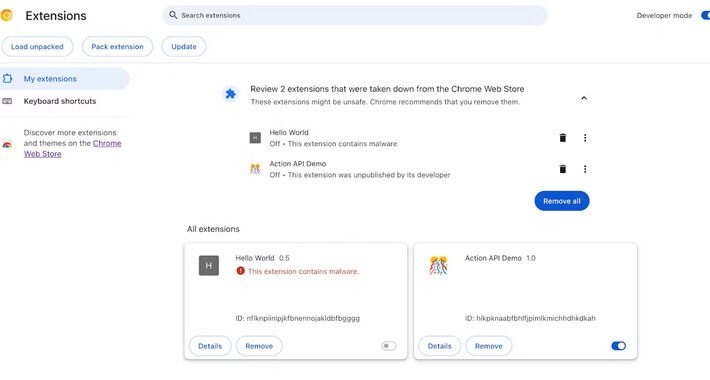
Google Chrome’s New Feature Alerts Users About Auto-Removal of Malicious Extensions – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 18, 2023THNBrowser Security / Malware Google has announced plans to add a new feature in the upcoming version of its...
Microsoft: BlackCat’s Sphynx ransomware embeds Impacket, RemCom – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has discovered a new version of the BlackCat ransomware that embeds the Impacket networking framework and the Remcom hacking...
Hackers ask $120,000 for access to multi-billion auction house – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Hackers claim to have breached the network of a major auction house and offered access to whoever was willing to...
Microsoft PowerShell Gallery vulnerable to spoofing, supply chain attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Lax policies for package naming on Microsoft’s PowerShell Gallery code repository allow threat actors to perform typosquatting attacks, spoof popular...
Phishing campaign steals accounts for Zimbra email servers worlwide – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An ongoing phishing campaign has been underway since at least April 2023 that attempts to steal credentials for Zimbra Collaboration...
Windows Task Manager refresh can be paused using CTRL key – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A very useful and previously unknown Windows tip was revealed this week, where you can halt process jumping in Task...
Thousands of Android APKs use compression trick to thwart analysis – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Threat actors increasingly distribute malicious Android APKs (packaged app installers) that resist decompilation using unsupported, unknown, or heavily tweaked compression...
Triple Extortion Ransomware and the Cybercrime Supply Chain – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Flare Ransomware attacks continue to grow both in sophistication and quantity. 2023 has already seen more ransomware attacks involving data...
Malware Is Turning Windows Machines Into Proxies – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime as-a-service , Fraud Management & Cybercrime , Social Engineering Proxy App Is Covertly Installed Via Alluring Offers or Compromised Software...
LIVE Webinar | Why Data Security is the Foundation for Your Security Posture – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Inside the Rise of ‘Dark’ AI Tools – Scary, But Effective? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development WormGPT, DarkGPT and Their Ilk Underdelivered – or Were Scams,...
Panel Discussion | Before & After AWS: Transforming Cloud’s Most Common Pitfalls into Progress – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Nate Kettlewell Principal, Application Security, Coalfire Nate Kettlewell is a specialist in information security, network engineering, and web application security. His...
LIVE Webinar | Straighten Up Your (Security) Posture: A Data Security Deep Dive – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Breach Roundup: Raccoon Stealer Makes a Comeback – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: QR Codes Used in Phishing Campaign; Belarus ISPs Used...
Cryptohack Roundup: Argentina Investigates WorldCoin – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Access Security Brokers (CASB) , Cybercrime , Fraud Management & Cybercrime Also: Milk Sad Vulnerability, FBI Forfeiture, X Crypto Scams...
Karma Catches Up to Global Phishing Service 16Shop – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs You’ve probably never heard of “16Shop,” but there’s a good chance someone using it has tried to phish you. A 16Shop...
ProjectDiscovery Lands $25M Investment for Cloud Security Tech – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine San Francisco cloud security startup ProjectDiscovery has banked $25 million in early-stage financing as investors continue to place bets on...
Google Brings AI Magic to Fuzz Testing With Eye-Opening Results – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Google has sprinkled the magic of artificial intelligence into its open source fuzz testing infrastructure and the results suggest LLM...
Rapid7 Says ROI for Ransomware Remains High; Zero-Day Usage Expands – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Rapid7 mid-year review of the threat landscape is not reassuring. Ransomware remains high, basic security defenses are not being...