Source: www.securityweek.com – Author: Ionut Arghire The Air Force Office of Special Investigations (AFOSI), the Federal Bureau of Investigation (FBI), and the National Counterintelligence and Security...
Month: August 2023
Webinar Tomorrow: ZTNA Superpowers CISOs Should Know – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News You’re invited to join Cloudflare and SecurityWeek for a live webinar on Tuesday, August 22nd we discuss “VPN Replacement: Other...
Brazilian Hacker Claims Bolsonaro Asked Him to Hack Into the Voting System Ahead of 2022 Vote – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A Brazilian hacker claimed at a congressional hearing Thursday that then-President Jair Bolsonaro wanted him to hack into the country’s...
Flaws in Juniper Switches and Firewalls Can Be Chained for Remote Code Execution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Networking appliances maker Juniper Networks has announced patches for four vulnerabilities in the J-Web interface of Junos OS, which could...
Tesla Discloses Data Breach Related to Whistleblower Leak – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Tesla has disclosed a data breach impacting roughly 75,000 people, but the incident is the result of a whistleblower leak...
Deceptive AI Bots Spread Malware, Raise Security Concerns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by Cyber-criminals have been exploiting fraudulent artificial intelligence (AI) bots to attempt and install malicious software under the guise of...
New Chrome Feature Alerts Users About Malicious Extensions – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Google has announced an update set to be introduced in Chrome 117. This new feature aims to proactively inform users when...
New NCUA Rule Requires Swift Cyber Incident Reporting – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Federally insured credit unions have been notified by the National Credit Union Administration (NCUA) of a new regulation set to take...
US Space Industry Under Threat from Foreign Cyber Espionage – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Foreign intelligence services could use direct and supply chain cyber-attacks to gain access to the US space industry, according to US intelligence....
Government Urges More Students to Be Cyber Explorers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The government is urging more schools to enrol their students in a government scheme designed to boost cyber skills, claiming that...
Police Insider Tipped Off Criminal Friend About EncroChat Bust – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 An intelligence analyst working for police in the North West of England shared information about a major countrywide operation with a...
Cuba Ransomware Group Steals Credentials Via Veeam Exploit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A notorious Russian-speaking ransomware group has updated its attack tooling to include a Veeam exploit designed to harvest logins, according to...
UK Competition Regulator Clears Broadcom, VMware Merger – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security Broadcom Anticipates It Can Close Deal Before Oct. 30 Akshaya Asokan (asokan_akshaya) • August 21, 2023 Image:...
US CISA Urges Security by Design for AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Part of Agency’s Campaign to Align Design, Development With Security...
Why Managed File Transfer Products Are a Hacker’s Paradise – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware , Video John Dwyer of IBM Security X-Force on Using Predictive Threat Intelligence Tom Field...
The Hidden Benefits of Negotiating With Ransomware Attackers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware , Video GuidePoint Security’s Mark Lance on Ways to Delay and Gather Info on Cybercriminals...
White House Announces AI Cybersecurity Challenge – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier At Black Hat last week, the White House announced an AI Cyber Challenge. Gizmodo reports: The new AI cyber challenge...
New WinRAR Vulnerability Could Allow Hackers to Take Control of Your PC – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 21, 2023THNVulnerability / Cyber Threat A high-severity security flaw has been disclosed in the WinRAR utility that could be potentially...
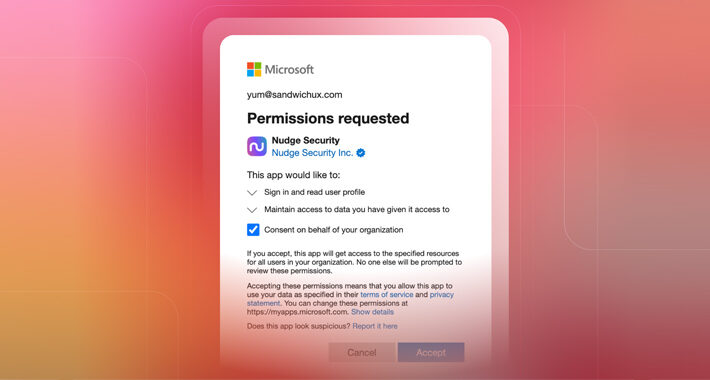
How to Investigate an OAuth Grant for Suspicious Activity or Overly Permissive Scopes – Source:thehackernews.com
Source: thehackernews.com – Author: . From a user’s perspective, OAuth works like magic. In just a few keystrokes, you can whisk through the account creation process...
Fighting API Bots with Cloudflare’s Invisible Turnstile – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt There’s a “hidden” API on HIBP. Well, it’s not “hidden” insofar as it’s easily discoverable if you watch the network...
Generative AI Is Scraping Your Data. So, Now What? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Benjamin Fabre, Co-Founder & CEO, DataDome There’s no denying ChatGPT and other generative AI models are a double-edged sword: While they can...
DEF CON’s AI Village Pits Hackers Against LLMs to Find Flaws – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading DEF CON 2023 — Las Vegas — DEF CON’s most buzzed-about event, the AI Village, let thousands...
Visibility Is Just Not Enough to Secure Operational Technology Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 For anyone new to securing an operational technology (OT) network or industrial control systems (ICS) from cyber threats, gaining full visibility...
Hands on with Windows 11’s ‘never combine’ taskbar feature – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Windows 11, already a monumental shift in design from its predecessor, continues to evolve. In its upcoming 23H2 release slated for...
This Malware Turned Thousands of Hacked Windows and macOS PCs into Proxy Servers – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 21, 2023THNMalware / Privacy Threat actors are leveraging access to malware-infected Windows and macOS machines to deliver a proxy server...
HiatusRAT Malware Resurfaces: Taiwan Firms and U.S. Military Under Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 21, 2023THNCyber Threat / Malware The threat actors behind the HiatusRAT malware have returned from their hiatus with a new...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker’s convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the convention due to a...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...