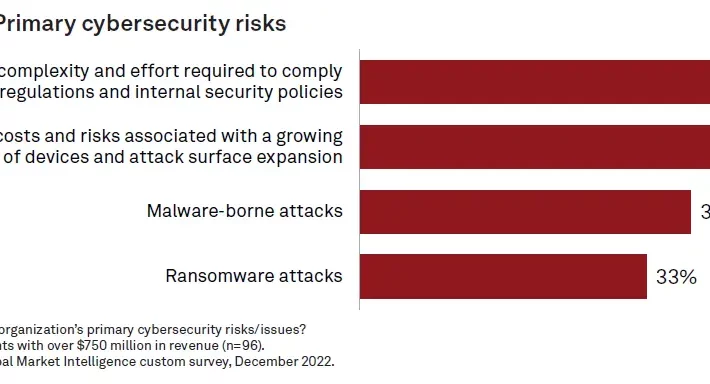
Source: securityboulevard.com – Author: Avast Blog Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
Month: August 2023
Hacker in Residence, on Black Hat USA 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jason Kent Attending many of the HackerSummerCamp activities involves attending a bunch of small meetups and social gatherings. Much of my peer...
Do we really need another cybersecurity tool? – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Research shows many companies now own and operate more than 60 disparate security tools, yet breaches continue to make headlines. Throwing...
BSidesTLV 2023 – Keren Elazari BSidesTLV 2023: Closing Words – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
Deepfactor 3.3 Includes Enhanced Prioritization of SCA Findings and New Free-Trial Offer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepfactor Deepfactor Release 3.3 Overview In Release 3.3 of Deepfactor Developer Security, we have made significant enhancements to the platform’s artifact scanner...
Ransomware Surges in Nuspire’s Q2 2023 Threat Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Nuspire’s latest threat report, which analyzes threat data from Q2 2023, reveals a jump in ransomware activity. In fact, the...
Lapsus$ Jury Says Teen Duo Did Do Crimes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Arion Kurtaj and anon minor: Part of group that hacked Uber, Nvidia, Microsoft, Rockstar Games and many more. Two teenage...
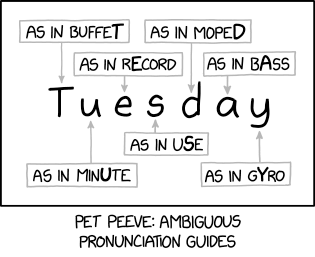
Randall Munroe’s XKCD ‘Pronunciation’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
What is ARMOR Foundational Visibility? Level 1 of The ARMOR Assessment Explained – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joel Wong The cybersecurity industry is riddled with challenges like how to prevent breaches, mitigate alert fatigue, connect siloed tools, and measure...
Founders of Crypto Mixer Tornado Cash Indicted for Laundering $1 Billion – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The U.S. government is taking a big swing at two founders of the Tornado Cash cryptocurrency mixer that allegedly laundered...
Scarab Ransomware Deployed Using SpaceColon Toolkit – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware Developers Appear To Be Preppring New Ransomware Malware Akshaya Asokan (asokan_akshaya) • August 24, 2023...
LIVE Webinar | Straighten Up Your (Security) Posture: 5 Pillars of Data Security – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Breach Roundup: Rhysida Ransom Gang Cops to Hospital Hacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Fraud Management & Cybercrime , Ransomware Also: Cyberattack Disrupts Expat Voting in Ecuador; Africa Arrests Cybercriminals Anviksha More...
LIVE Webinar | Humans vs Machines: Redefining How AI & People Can Work Together – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Tom Corn Chief Product Officer, Ontinue As Chief Product Officer for Ontinue, Tom drives the vision and development of Ontinue solutions....
Cryptohack Roundup: Tornado Cash in the Eye of the Storm – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: FBI Issues DPRK Alert; Incidents Affect Exactly, Harbor and...
Mississippi Hospital System Still Struggling With Attack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Healthcare The Gulf Coast Provider Is Among the Regional Health Systems Hit Recently Marianne...
Scarab Ransomware Deployed Using SpaceColon Toolkit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Developers Appear To Be Preppring New Ransomware Malware Akshaya Asokan (asokan_akshaya) • August 24, 2023...
LIVE Webinar | Straighten Up Your (Security) Posture: 5 Pillars of Data Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Breach Roundup: Rhysida Ransom Gang Cops to Hospital Hacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Fraud Management & Cybercrime , Ransomware Also: Cyberattack Disrupts Expat Voting in Ecuador; Africa Arrests Cybercriminals Anviksha More...
LIVE Webinar | Humans vs Machines: Redefining How AI & People Can Work Together – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Tom Corn Chief Product Officer, Ontinue As Chief Product Officer for Ontinue, Tom drives the vision and development of Ontinue solutions....
Cryptohack Roundup: Tornado Cash in the Eye of the Storm – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: FBI Issues DPRK Alert; Incidents Affect Exactly, Harbor and...
Mississippi Hospital System Still Struggling With Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Healthcare The Gulf Coast Provider Is Among the Regional Health Systems Hit Recently Marianne...
Chinese-backed APT ‘Flax Typhoon’ Hacks Taiwan with Minimal Malware Footprint – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Threat hunters at Microsoft have caught a Chinese government-backed APT actor hacking into organizations in Taiwan with minimal use of...
University of Minnesota Confirms Data Breach, Says Ransomware Not Involved – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The University of Minnesota has confirmed that a threat actor has exfiltrated data from its systems, but says no malware...
Cisco Patches Vulnerabilities Exposing Switches, Firewalls to DoS Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced patches for six vulnerabilities in its products, including three high-severity bugs in NX-OS and FXOS software...
Mysterious Malware Uses Wi-Fi Scanning to Get Location of Infected Device – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers at Secureworks have come across a mysterious piece of malware that scans for nearby Wi-Fi access points in an...
FBI: Patches for Recent Barracuda ESG Zero-Day Ineffective – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Federal Bureau of Investigation says that the patches released for a recent Barracuda Email Security Gateway (ESG) vulnerability were...
Rockwell ThinManager Vulnerabilities Could Expose Industrial HMIs to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Vulnerabilities discovered by researchers in Rockwell Automation’s ThinManager ThinServer product could be exploited in attacks aimed at industrial control systems...
Digital Identity Protection Firm SpyCloud Raises $110 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Account takeover and fraud prevention company SpyCloud on Wednesday announced that it has raised $110 million in a funding round...
Traders Targeted by Cybercriminals in Attack Exploiting WinRAR Zero-Day – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A financially motivated cybercrime group has exploited a zero-day vulnerability in the popular file archiving utility WinRAR to deliver malware...