Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Month: August 2023
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 2
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
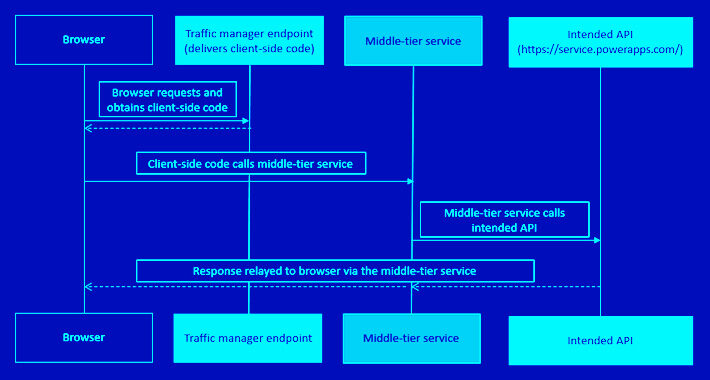
Experts Uncover How Cybercriminals Could Exploit Microsoft Entra ID for Elevated Privilege – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 28, 2023THNVulnerability / Active Directory Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID...
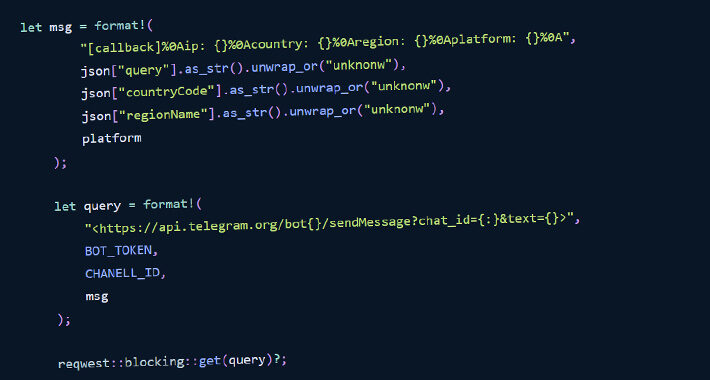
Developers Beware: Malicious Rust Libraries Caught Transmitting OS Info to Telegram Channel – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 28, 2023THNSupply Chain / Software Security In yet another sign that developers continue to be targets of software supply chain...
Cyberattacks Targeting E-commerce Applications – Source:thehackernews.com
Source: thehackernews.com – Author: . Cyber attacks on e-commerce applications are a common trend in 2023 as e-commerce businesses become more omnichannel, they build and deploy...
Cyber Info-Sharing Guide for Healthcare Sector Updated – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Healthcare , Industry Specific , Next-Generation Technologies & Secure Development Sector Urged to Broaden Info Sharing Beyond Traditional Indicators Marianne Kolbasuk...
Ransomware Attack Cleanup Costs: $10M So Far for Rackspace – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Incident & Breach Response , Ransomware Fallout From Crypto-Locking Malware Attacks and Data Exfiltration Remains Costly...
Why a Wiz-SentinelOne Deal Makes Sense, and Why It Might Not – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Open XDR , Security Operations Despite the Financial Hurdles, the Perks of Building a CNAPP-XDR Platform Are Clear...
Crypto Investor Data Stolen From Kroll In SIM Swap – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime FTX, BlockFI and Genesis Claimants at Risk of Phishing Mihir...
Met Police Officers at Risk After Serious Data Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Cybercrime , Endpoint Security Scotland Yard Probes Impact of Suspected Hack Attack Against Service Provider Mathew J. Schwartz...
Global Privacy Agencies Urge Social Media to Protect User Data from Scraping – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac In a statement published online, 12 data protection and privacy authorities from around the world urge social media platforms to...
French Unemployment Agency Announces a Data Breach – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Pole emploi, the government’s unemployment registration and financial assistance office in France, announced a data breach. The incident affected 10...
Acquisition Chatter Swirls Around SentinelOne, BlackBerry – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Prominent anti-malware vendors SentinelOne and BlackBerry have been separately named in public acquisition chatter, underscoring a clear signal of impending...
10 Million Likely Impacted by Data Breach at French Unemployment Agency – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The personal information of roughly 10 million individuals was likely compromised in a data breach at French governmental unemployment agency...
Signs of Malware Attack Targeting Rust Developers Found on Crates.io – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Crates.io Rust package registry was targeted recently in what appeared to be the initial phase of a malware attack...
3 Malware Loaders Detected in 80% of Attacks: Security Firm – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire QakBot, SocGholish, and Raspberry Robin are the three most popular malware loaders among cybercriminals, accounting for 80% of the observed...
Two Men Arrested Following Poland Railway Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Polish police on Sunday arrested two men suspected of illegally hacking into the national railway’s communications network, which destabilized traffic in...
Leaseweb Reports Cloud Disruptions Due to Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Dutch infrastructure-as-a-service and cloud solutions provider Leaseweb shut down some critical systems last week due to a cyberattack. The company...
Ohio History Organization Says Personal Information Stolen in Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Ohio History Connection (OHC) has confirmed that personal information of thousands of individuals was stolen in a July ransomware attack...
3 Cryptocurrency Firms Suffer Data Breach After Kroll SIM Swapping Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Three bankrupt cryptocurrency companies — FTX, BlockFi and Genesis — have suffered data breaches following a SIM swapping attack that...
Remotely Stopping Polish Trains – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Turns out that it’s easy to broadcast radio commands that force Polish trains to stop: …the saboteurs appear to have...
Exploit released for Juniper firewall bugs allowing RCE attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Proof-of-concept exploit code has been publicly released for vulnerabilities in Juniper SRX firewalls that, when chained, can allow unauthenticated attackers...
Mom’s Meals discloses data breach impacting 1.2 million people – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas PurFoods, which conducts business in the U.S. as ‘Mom’s Meals,’ is warning of a data breach after the personal information...
Four common password mistakes hackers love to exploit – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Our brains are incredibly good at pattern completion – it’s why we see animals in the clouds and...
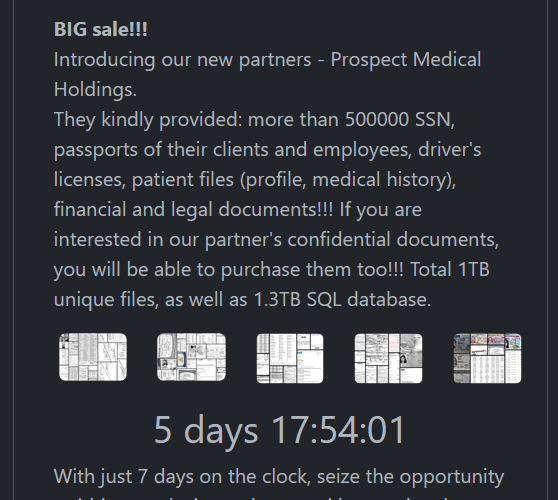
Rhysida claims ransomware attack on Prospect Medical, threatens to sell data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The Rhysida ransomware gang has claimed responsibility for the massive cyberattack on Prospect Medical Holdings, claiming to have stolen 500,000...
Microsoft wants you to learn more about new features in Windows 11 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft is experimenting with different approaches to introduce new users to Windows 11’s features as soon as they complete the...
ICO calls on social media firms to protect user’s data from scraping – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas UK’s Information Commissioner’s Office (ICO), together with eleven data protection and privacy authorities from around the world, have published a...
Black Hat Fireside Chat: How to achieve API security — as AI-boosted attacks intensify – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido API security has arisen as a cornerstone of securing massively interconnected cloud applications. At Black Hat USA...
Rhysida ransomware group claims the hack of Prospect Medical – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Rhysida ransomware group claims the hack of Prospect Medical The Rhysida ransomware group claimed to have hacked Prospect Medical Holdings...