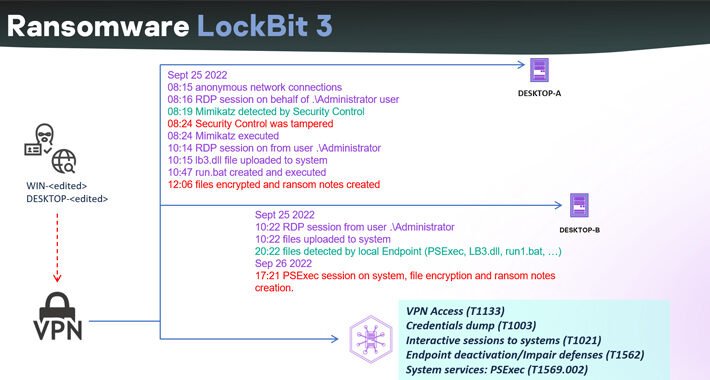
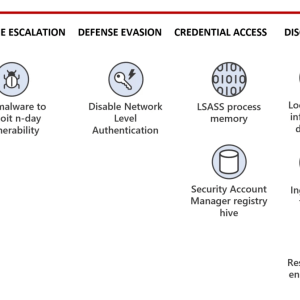
Source: thehackernews.com – Author: . The leak of the LockBit 3.0 ransomware builder last year has led to threat actors abusing the tool to spawn new...
Day: August 26, 2023
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 15
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 1
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 1
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 2
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 1
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
These 7 items should be on your CISO checklist for 2024 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: As a Chief Information Security Officer (CISO), you’re entrusted with orchestrating a harmonious convergence of technology, strategic acumen, and...
Friday Squid Blogging: China’s Squid Fishing Ban Ineffective – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier China imposed a “pilot program banning fishing in parts of the south-west Atlantic Ocean from July to October, and parts...
Hacking Food Labeling Laws – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier This article talks about new Mexican laws about food labeling, and the lengths to which food manufacturers are going to...
Kroll Employee SIM-Swapped for Crypto Investor Data – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Security consulting giant Kroll disclosed today that a SIM-swapping attack against one of its employees led to the theft of user...
China-linked Flax Typhoon APT targets Taiwan – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini China-linked APT group Flax Typhoon targeted dozens of organizations in Taiwan as part of a suspected espionage campaign. Microsoft linked...
Cisco Talos Research: New Lazarus Group Attack Malware Campaign Hits UK & US Businesses – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet The Cisco Talos report exposes new malware used by the group to target Internet backbone infrastructure and healthcare organizations in...
XLoader Malware Variant Targets MacOS Disguised as OfficeNote App – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet A new variant of malware called XLoader is targeting macOS users. XLoader’s execution, functionalities and distribution are detailed. Image: Sashkin/Adobe...
Kroll Suffers Data Breach: Employee Falls Victim to SIM Swapping Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 26, 2023THNData Breach / SIM Swapping Risk and financial advisory solutions provider Kroll on Friday disclosed that one of its...
How to Choose the Best XDR Solution for Your Organization? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The fact that malicious software gets smarter and more sophisticated every day that goes by is no news to any...
Genworth Financial Under Investigation for Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO, Aug. 24, 2023 /PRNewswire/ — Schubert Jonckheer & Kolbe LLP is investigating a data breach impacting the personal information of over...
China Unleashes Flax Typhoon APT to Live Off the Land, Microsoft Warns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A China-backed advanced persistent threat (APT) group dubbed Flax Typhoon has installed a web of persistent,...
Luna Grabber Malware Targets Roblox Gaming Devs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Since the start of this month, researchers at ReversingLabs have found a host of malicious, multistage packages...
‘Whiffy Recon’ Malware Transmits Device Location Every 60 Seconds – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading Researchers have uncovered the “Whiffy Recon” malware being deployed by the SmokeLoader botnet, which is a...
Is Bias in AI Algorithms a Threat to Cloud Security? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Amir Shachar, Director of AI and Research, Skyhawk Security Artificial intelligence (AI) has been helping humans in IT security operations since the...