Source: thehackernews.com – Author: . Aug 25, 2023THNCyber Crime / Data Breach Two U.K. teenagers have been convicted by a jury in London for being part...
Day: August 25, 2023
Learn How Your Business Data Can Amplify Your AI/ML Threat Detection Capabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 25, 2023The Hacker NewsThreat Detection / Artificial Intelligence In today’s digital landscape, your business data is more than just numbers—it’s...
Navigating Legacy Infrastructure: A CISO’s Actionable Strategy for Success – Source:thehackernews.com
Source: thehackernews.com – Author: . Every company has some level of tech debt. Unless you’re a brand new start-up, you most likely have a patchwork of...
China-Linked Flax Typhoon Cyber Espionage Targets Taiwan’s Key Sectors – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 25, 2023THNCyber Espionage A nation-state activity group originating from China has been linked to cyber attacks on dozens of organizations...
In Other News: Africa Cybercrime Crackdown, Unpatched macOS Flaw, Investor Disclosures – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
North Korean APT Hacks Internet Infrastructure Provider via ManageEngine Flaw – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The North Korea-linked advanced persistent threat (APT) actor Lazarus Group has been observed exploiting a Zoho ManageEngine vulnerability to compromise...
Cypago Raises $13 Million for GRC Automation Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Israeli startup Cypago on Thursday announced that it has raised $13 million in a funding round led by Entrée Capital,...
Lawmaker Wants Federal Contractors to Have Vulnerability Disclosure Policies – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Congresswoman Nancy Mace (R-SC) this week introduced a bill that would require federal contractors to implement a Vulnerability Disclosure Policy...
Europe is Cracking Down on Big Tech. This Is What Will Change When You Sign On – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Starting Friday, Europeans will see their online life change. People in the 27-nation European Union can alter some of what...
Google Workspace Introduces New AI-Powered Security Controls – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Thursday introduced new AI-powered security controls for its Workspace customers, targeting zero trust, digital sovereignty, and threat defense....
Nearly 1,000 Organizations, 60 Million Individuals Impacted by MOVEit Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Nearly 1,000 organizations and 60 million individuals are reportedly impacted by the recent MOVEit campaign conducted by the Russian-speaking Cl0p...
Court finds autistic members of LAPSUS$ gang responsible for GTA 6 hack and other high profile breaches – Source: www.bitdefender.com
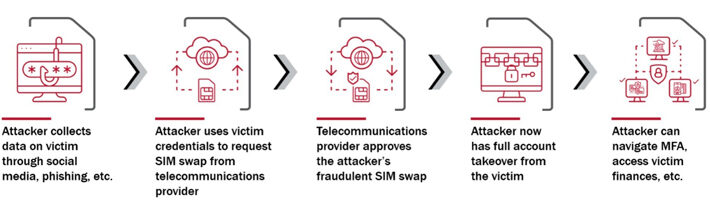
Source: www.bitdefender.com – Author: Graham Cluley A London court has found two British teens responsible for a spree of high profile hacks, including one that saw...
North Korea ready to cash out more than $40 million in Bitcoin after summer of hacks, warns FBI – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley After a series of high-profile cryptocurrency heists, a state-sponsored North Korean malicious hacking group is poised to cash out millions...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 16
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 16
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 0
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 17
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 16
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Lockbit leak, research opportunities on tools leaked from TAs – Source: securelist.com
Source: securelist.com – Author: Eduardo Ovalle, Francesco Figurelli Lockbit is one of the most prevalent ransomware strains. It comes with an affiliate ransomware-as-a-service (RaaS) program offering...
Cerby Announces $17M in Series A Funding to Secure Nonstandard Applications – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ALAMEDA, Calif., Aug. 22, 2023 /PRNewswire/ — Cerby, the comprehensive access management platform for nonstandard applications, today announced that the company has raised $17 million in...