Source: www.infosecurity-magazine.com – Author: 1 Security researchers have detected a 178% increase in sextortion emails between the first half of 2022 and the same period this...
Day: August 24, 2023
St Helens Council Warns of Phishing After Ransomware Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A UK local authority has warned citizens to watch out for follow-on scams after it was breached in a ransomware attack...
Teens Found Responsible For Lapsus$ Cyber-Attacks – Source: www.infosecurity-magazine.com
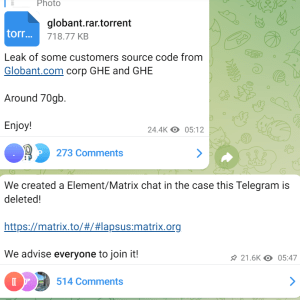
Source: www.infosecurity-magazine.com – Author: 1 An Oxford teenager has been found guilty of a series of hacking incidents impacting big-name brands, as part of the infamous...
Attack Dwell Times Fall but Threat Actors Are Moving Faster – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The dwell time of cyber-attacks fell to a median of eight days in the first half of 2023, but attackers are...
Lapsus$ member has been convicted of having hacked multiple high-profile companies – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini An 18-year-old member of the Lapsus$ gang has been convicted of having helped hack multiple high-profile companies. A teenage member of...
More than 3,000 Openfire servers exposed to attacks using a new exploit – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn that more than 3,000 unpatched Openfire servers are exposed to attacks using an exploit for a recent flaw....
DoJ charged Tornado Cash founders with laundering more than $1 billion – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. DoJ charged two men with operating the Tornado Cash service and laundering more than $1 Billion in criminal...
FBI identifies wallets holding cryptocurrency funds stolen by North Korea – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. FBI warned that North Korea-linked threat actors may attempt to cash out stolen cryptocurrency worth more than $40...
December’s Reimagining Democracy Workshop – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Imagine that we’ve all—all of us, all of society—landed on some alien planet, and we have to form a government:...
US FBI Urges Action on Barracuda ESG Hacking – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Chinese Hackers Adapt to Countermeaures David Perera...
Threat Actor Targets Hong Kong With Korplug Backdoor – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Previously Unknown APT Uses Supply Chain Hack to Reach Victims Jayant Chakravarti...
LIVE Webinar | Fight (Ransomware) or Flight: The Human Aspect of Threat Mitigation – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Data Protection and its Modern Role in Cyber Recovery (en français) – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Jury Finds 2 Teenagers Perpetrated Lapsus$ Group Hacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Rockstar, Uber, Okta, Microsoft and Other Big-Name Players Fell to Group’s Attacks Mathew J. Schwartz...
MOVEit Health Data Breach Tally Keeps Growing – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Healthcare , Incident & Breach Response , Industry Specific More Hacks Compromising Protected Health Info Being Reported to Regulators Marianne Kolbasuk...
Spin.AI: Browser Extensions Bring High Security Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Software-as-a-service (SaaS) applications have become foundational to enterprises that use them to drive productivity, improve the customer experience, and connect...
Unleashing Data Privacy Excellence: Our ISO 27018 Certification – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Phantis Since its beginning, ForgeRock has been focused on enabling people to simply and securely access the connected world. To support...
BSidesTLV 2023 – Ido Veltzman – (Lady|)Lord Of The Ring – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
Back from Hacker Summer Camp 2023: One CTO’s Experience – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Larkin Another August, another Hacker Summer Camp. The annual gathering of 25,000 like-minded hackers and security enthusiasts descended on Vegas for...
Enterprises Eyeing More Proactive Cybersecurity Strategies, Survey Finds – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Enterprise security teams are having problems keeping pace with the rapid evolution of increasingly sophisticated threat groups despite having the...
The Rise of the Startup CCO: Meet Mike Barker of HYAS – Source: securityboulevard.com
Source: securityboulevard.com – Author: HYAS HYAS Chief Commercial Officer (CCO), Mike Barker, has a broad and deep background in engineering as well as executive leadership roles....
Malware-as-a-Service: Redline Stealer Variants Demonstrate a Low-Barrier-to-Entry Threat – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aleksander W. Jarosz Multiple New Campaigns in 2023 Demonstrate The Malware Family Has Been Redeveloped to Remain a Popular And Prominent Threat...
BSidesTLV 2023 – Ariel Szarf, Doron Karmi – Google Workspace Forensics — Insights From Real-World Hunts & IR – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
HP Report Details Tactics Used to Evade Detection Tools – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard HP Inc. today published a report detailing how the tactics and techniques being used by cybercriminals to evade detection tools...
US FBI Urges Action on Barracuda ESG Hacking – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Chinese Hackers Adapt to Countermeaures David Perera...
Threat Actor Targets Hong Kong With Korplug Backdoor – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Previously Unknown APT Uses Supply Chain Hack to Reach Victims Jayant Chakravarti...
LIVE Webinar | Fight (Ransomware) or Flight: The Human Aspect of Threat Mitigation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Data Protection and its Modern Role in Cyber Recovery (en français) – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Jury Finds 2 Teenagers Perpetrated Lapsus$ Group Hacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Rockstar, Uber, Okta, Microsoft and Other Big-Name Players Fell to Group’s Attacks Mathew J. Schwartz...
MOVEit Health Data Breach Tally Keeps Growing – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Incident & Breach Response , Industry Specific More Hacks Compromising Protected Health Info Being Reported to Regulators Marianne Kolbasuk...