Source: www.securityweek.com – Author: Ryan Naraine Threat hunters at Microsoft have caught a Chinese government-backed APT actor hacking into organizations in Taiwan with minimal use of...
Day: August 24, 2023
University of Minnesota Confirms Data Breach, Says Ransomware Not Involved – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The University of Minnesota has confirmed that a threat actor has exfiltrated data from its systems, but says no malware...
Cisco Patches Vulnerabilities Exposing Switches, Firewalls to DoS Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced patches for six vulnerabilities in its products, including three high-severity bugs in NX-OS and FXOS software...
Mysterious Malware Uses Wi-Fi Scanning to Get Location of Infected Device – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers at Secureworks have come across a mysterious piece of malware that scans for nearby Wi-Fi access points in an...
FBI: Patches for Recent Barracuda ESG Zero-Day Ineffective – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Federal Bureau of Investigation says that the patches released for a recent Barracuda Email Security Gateway (ESG) vulnerability were...
Rockwell ThinManager Vulnerabilities Could Expose Industrial HMIs to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Vulnerabilities discovered by researchers in Rockwell Automation’s ThinManager ThinServer product could be exploited in attacks aimed at industrial control systems...
Digital Identity Protection Firm SpyCloud Raises $110 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Account takeover and fraud prevention company SpyCloud on Wednesday announced that it has raised $110 million in a funding round...
Traders Targeted by Cybercriminals in Attack Exploiting WinRAR Zero-Day – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A financially motivated cybercrime group has exploited a zero-day vulnerability in the popular file archiving utility WinRAR to deliver malware...
Hosting Provider CloudNordic Loses All Customer Data in Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Danish cloud hosting services provider CloudNordic has announced that all its systems were rendered unusable following a ransomware attack. The...
UK Court Concludes Teenager Behind Huge Hacking Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP A UK court on Wednesday found a teenager responsible for a hacking campaign that included one of the biggest breaches in...
FBI Flags $40M Crypto Cash-Out Plot By North Korean Hackers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Federal Bureau of Investigation (FBI) has issued a stark warning to cryptocurrency firms regarding a surge in blockchain activity linked...
Data of 2.6 Million Duolingo Users Leaked on Hacking Forum – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Data from 2.6 million users of Duolingo, a language learning platform with over 74 million monthly users, has been leaked on...
New Study Sheds Light on Adhubllka Ransomware Network – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity researchers have unveiled a complex web of interconnected ransomware strains that trace their origins back to a common source: the...
NIST Publishes Draft Post-Quantum Cryptography Standards – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Draft post-quantum cryptography (PQC) standards have been published by the US National Institute of Standards and Technology (NIST). The new framework...
Sensitive Data of 10 Million at Risk After French Employment Agency Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The French national employment agency, Pôle emploi, has been hit by a cyber-attack potentially exposing critical information of up to 10...
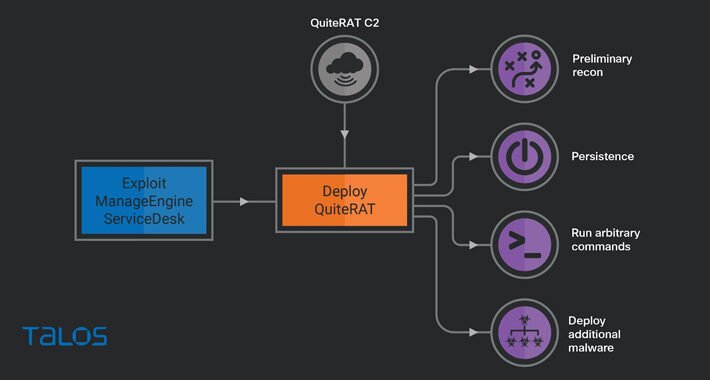
Lazarus Group Exploits Critical Zoho ManageEngine Flaw to Deploy Stealthy QuiteRAT Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 24, 2023THNCyber Attack / Hacking The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched...
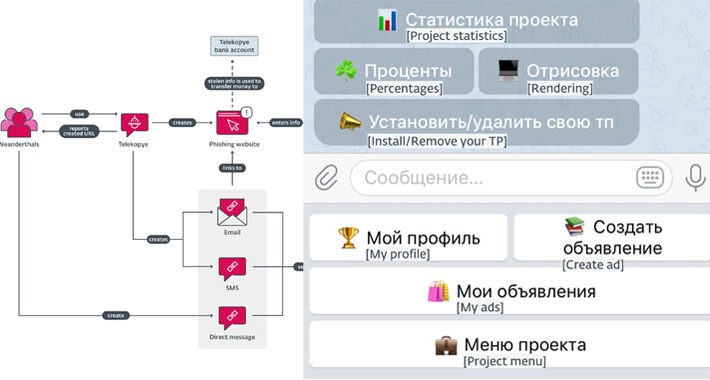
New Telegram Bot “Telekopye” Powering Large-scale Phishing Scams from Russia – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 24, 2023THNCyber Threat / Phishing A new financially motivated operation is leveraging a malicious Telegram bot to help threat actors...
The Hidden Dangers of Public Wi-Fi – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 24, 2023The Hacker NewsNetwork Security / DNS Public Wi-Fi, which has long since become the norm, poses threats to not...
New “Whiffy Recon” Malware Triangulates Infected Device Location via Wi-Fi Every Minute – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 24, 2023THNMalware / Privacy The SmokeLoader malware is being used to deliver a new Wi-Fi scanning malware strain called Whiffy...
WinRAR Security Flaw Exploited in Zero-Day Attacks to Target Traders – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 24, 2023THNEndpoint Security / Zero-Day A recently patched security flaw in the popular WinRAR archiving software has been exploited as...
Ransomware With an Identity Crisis Targets Small Businesses, Individuals – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Researchers have identified a new strain of ransomware that dates back to 2019 and targets individuals and...
eBay Users Beware Russian ‘Telekopye’ Telegram Phishing Bot – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Russian-language Telegram users are using a bot to automate end-to-end phishing campaigns against users of popular ecommerce...
What the Hive Ransomware Case Says About RaaS and Cryptocurrency – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ryan Estes, Intrusion Analyst, WatchGuard Technologies Earlier this year, law enforcement officials disrupted the operations of the Hive cybercriminal group, which profited...
5 Best Practices for Implementing Risk-First Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kaus Phaltankar, Co-Founder & CEO, Caveonix Organizations face an uphill battle to safeguard hybrid cloud assets and sensitive data from evolving cyber...
North Korea’s Lazarus APT Uses GUI Framework to Build Stealthy RAT – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading In recent attacks against healthcare organizations and an Internet infrastructure company, North Korea’s famous Lazarus Group...
eSentire Labs Open Sources Project to Monitor LLMs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading eSentire Labs announced the eSentire LLM Gateway, an open source implementation framework that provides security teams with...
Prelude Security Tackles Continuous Security Testing in Containers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Prelude Security has enhanced its Probes technology to help security teams run continuous security tests on all...
New Windows updates cause UNSUPPORTED_PROCESSOR blue screens – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says the August 2023 preview updates released this week for Windows 11 and Windows 10 systems are causing blue...
New Whiffy Recon malware uses WiFi to triangulate your location – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cybercriminals behind the Smoke Loader botnet are using a new piece of malware called Whiffy Recon to triangulate the location...
Exploit released for Ivanti Sentry bug abused as zero-day in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Proof-of-concept exploit code is now available for a critical Ivanti Sentry authentication bypass vulnerability that enables attackers to execute code...