Source: thehackernews.com – Author: . Aug 22, 2023THNVulnerability / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw in...
Day: August 22, 2023
10 top corporate account takeover prevention strategies – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: A corporate account takeover can present significant risks for any organization. A corporate account takeover can have detrimental, far-reaching...
News Alert: airSlate partners with Forthright to launch automated business-efficiency, workflow tool – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Boston, Mass, Aug. 22, 2023 – airSlate, a leader in document workflow automation solutions, today announced the launch of QuickStart in collaboration with...
GUEST ESSAY: Lessons to be learned from the waves of BofA phone number spoofing scams – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Richard Grant Phone number spoofing involves manipulating caller ID displays to mimic legitimate phone numbers, giving scammers a deceptive veil...
TP-Link smart bulbs can let hackers steal your WiFi password – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Researchers from Italy and the UK have discovered four vulnerabilities in the TP-Link Tapo L530E smart bulb and TP-Link’s Tapo...
Sneaky Amazon Google ad leads to Microsoft support scam – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A legitimate-looking ad for Amazon in Google search results redirects visitors to a Microsoft Defender tech support scam that locks...
Ongoing Duo outage causes Azure Auth authentication errors – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Cisco-owned multi-factor authentication (MFA) provider Duo Security is investigating an ongoing outage that has been causing authentication failures and errors...
Ivanti warns of new actively exploited MobileIron zero-day bug – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan US-based IT software company Ivanti warned customers today that a critical Sentry API authentication bypass vulnerability is being exploited in...
Japanese watchmaker Seiko breached by BlackCat ransomware gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The BlackCat/ALPHV ransomware gang has added Seiko to its extortion site, claiming responsibility for a cyberattack disclosed by the Japanese...
Ivanti fixed a new critical Sentry API authentication bypass flaw – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ivanti warned customers of a new critical Sentry API authentication bypass vulnerability tracked as CVE-2023-38035. The software company Ivanti released...
BlackCat ransomware group claims the hack of Seiko network – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The BlackCat/ALPHV ransomware group claims to have hacked the Japanese maker of watches Seiko and added the company to its...
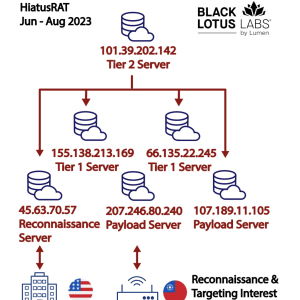
New HiatusRAT campaign targets Taiwan and U.S. military procurement system – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini HiatusRAT malware operators resurfaced with a new wave of attacks targeting Taiwan-based organizations and a U.S. military procurement system. In...
Spoofing an Apple device and tricking users into sharing sensitive data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini White hat hackers at the recent hacking conference Def Con demonstrated how to spoof an Apple device and trick users...
Israel and US to Invest $3.85 Million in projects for critical infrastructure protection through the BIRD Cyber Program – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Israel and US government agencies announced the BIRD Cyber Program, an investment of roughly $4M in projects to enhance the...
UK Competition Regulator Clears Broadcom, VMware Merger – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security Broadcom Anticipates It Can Close Deal Before Oct. 30 Akshaya Asokan (asokan_akshaya) • August 21, 2023 Image:...
US CISA Urges Security by Design for AI – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Part of Agency’s Campaign to Align Design, Development With Security...
Why Managed File Transfer Products Are a Hacker’s Paradise – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware , Video John Dwyer of IBM Security X-Force on Using Predictive Threat Intelligence Tom Field...
The Hidden Benefits of Negotiating With Ransomware Attackers – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware , Video GuidePoint Security’s Mark Lance on Ways to Delay and Gather Info on Cybercriminals...
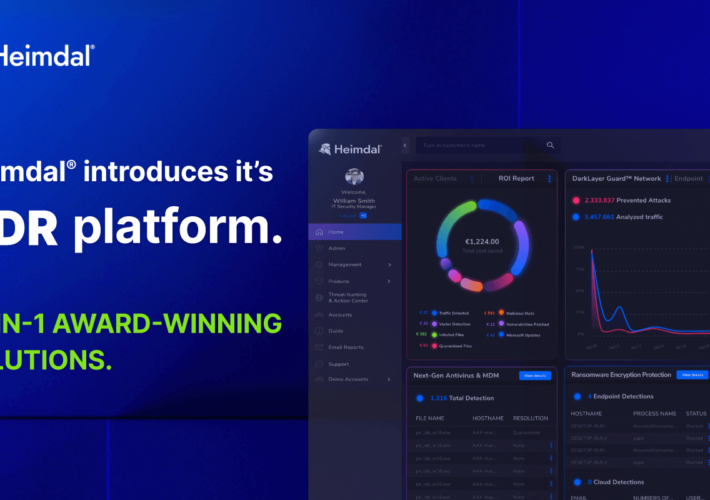
Introducing Heimdal XDR: A Game-Changer Disrupting the Market with the Widest Range of Next-Generation Solutions – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Heimdal® has announced its entry into the Extended Detection and Response (XDR) market with a disruptive SaaS platform. The company...
Cuba Ransomware Exploits Veeam Flaw, Targets U.S. and Latin American Entities – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici The Cuba ransomware gang has been seen launching attacks on critical infrastructure organizations in the U.S. and IT firms in...
WinRAR Vulnerability Allows Remote Code Execution – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici A vulnerability in WinRAR, the widely used file compression and archiving software for Windows, could allow remote attackers to execute...
What Is Network Access Control (NAC)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Antonia Din Network Access Control (NAC) is a cybersecurity technology that regulates access to network resources based on predefined policies and regulations....
News Alert: airSlate partners with Forthright to launch automated business-efficiency, workflow tool – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido Boston, Mass, Aug. 22, 2023 – airSlate, a leader in document workflow automation solutions, today announced the launch of QuickStart in collaboration with...
By Following the Crypto, Cyfirma Identifies Developer Behind CraxsRAT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The person responsible for developing the dangerous CraxsRAT malware that targets Android devices has been operating in Syria for more...
BSidesTLV 2023 – Andy Ellis – Hacking Harry Potter: The Untold Story Of Fantastical Social Engineering – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
GUEST ESSAY: Lessons to be learned from the waves of BofA phone number spoofing scams – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido Phone number spoofing involves manipulating caller ID displays to mimic legitimate phone numbers, giving scammers a deceptive veil of authenticity. Related:...
Randall Munroe’s XKCD ‘Electron Holes’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Cuba Ransomware Group Exploiting Veeam Flaw in Latest Campaign – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The high-profile Cuba ransomware group is abusing a security flaw in software from Veeam on recent attacks on a critical...
LOL WinRAR: Serious One-Click Bug (Patch NOW) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Fix for CVE-2023-40477 now available. Good old WinRAR has a serious security hole. If you still have it installed, get...
BSidesTLV 2023 – Aviad Carmel – Uh-OAuth! – Breaking (And Fixing) OAuth Implementations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...