Source: krebsonsecurity.com – Author: BrianKrebs In large metropolitan areas, tourists are often easy to spot because they’re far more inclined than locals to gaze upward at...
Day: August 22, 2023
Vulnerabilities in TP-Link IoT Devices Can Get You Hacked – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Four new vulnerabilities have been discovered in the TP-Link Tapo L530E smart bulb and TP-Link’s Tapo app. Researchers from Universita...
VMware Explore 2023: Keynote Highlights – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Explore enterprise applications and infrastructure, AI, tools for the remote workforce, machine learning, and more from VMware Explore 2023. Image:...
How to Quickly Give Users sudo Privileges in Linux – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Phil Hajjar on August 22, 2023, 10:23 AM EDT How to Quickly Give Users sudo Privileges in Linux If you have users...
Innovation Hides in Plain Sight and Openly Delights – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Smart spaces bring together universal connectivity, security, and intelligence to modernize the workspace experience. But what are technology leaders saying about this...
Reimagining Your Video Data Strategy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Did you know that about 99% of surveillance video goes unviewed? What if you could use that video data to simplify operations,...
Akamai Report: LockBit, Cl0P Expand Ransomware Efforts – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Adobe Stock/Jimon Akamai’s ransomware report released at Black Hat 2023 revealed that exploitation of zero-day and one-day vulnerabilities has...
Chinese APT Targets Hong Kong in Supply Chain Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading An emerging China-backed advanced persistent threat (APT) group targeted organizations in Hong Kong in a supply chain...
Ivanti Issues Fix for Critical Vuln In Its Sentry Gateway Technology – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Organizations using almost any version of the Ivanti Sentry security gateway product might want to immediately...
Tesla Data Breach Investigation Reveals Inside Job – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Tesla acknowledged In a filing with Maine’s attorney general that a recent data breach it experienced affecting...
Fed Warning: US Space Industry Subject To Foreign Spying, Disruptions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading Foreign adversaries are waging cyber espionage campaigns against the US space industry, according to a joint...
Energy One Investigates Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Wholesale energy software software provider Energy One reported on Friday a cyberattack had affected “certain corporate systems”...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker’s convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the convention due to a...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 12
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 0
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 0
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 1
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Carderbee Attacks: Hong Kong Organizations Targeted via Malicious Software Updates – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 22, 2023THNSoftware Supply Chain / Malware A previously undocumented threat cluster has been linked to a software supply chain attack...
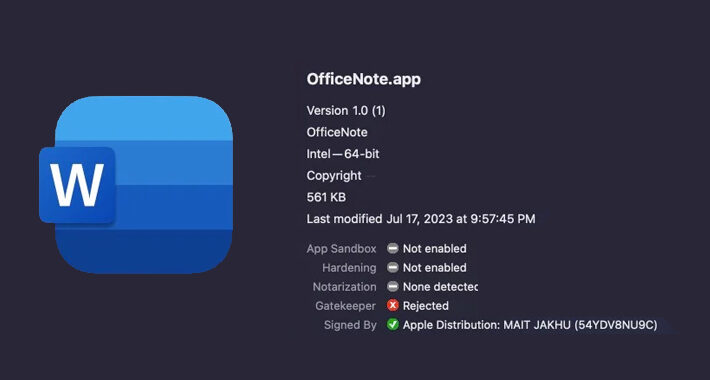
New Variant of XLoader macOS Malware Disguised as ‘OfficeNote’ Productivity App – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 22, 2023THNMalware / Endpoint Security A new variant of an Apple macOS malware called XLoader has surfaced in the wild,...
Ivanti Warns of Critical Zero-Day Flaw Being Actively Exploited in Sentry Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 22, 2023THNZero-Day / Software Security Software services provider Ivanti is warning of a new critical zero-day flaw impacting Ivanti Sentry...