Source: www.techrepublic.com – Author: Cedric Pernet on August 18, 2023, 3:26 PM EDT About 2000 Citrix NetScalers Were Compromised in Massive Attack Campaigns About 2,000 Citrix...
Day: August 19, 2023
Top 5 Disaster Recovery as a Service Providers for 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jonathan Kalibbala Unitrends Backup and Recovery: Best for AI-based backups and disaster prevention Microsoft Azure Site Recovery: Best for easy disaster recovery...
Five Things To Know About PCI DSS 4.0 Authentication Requirements – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shelley Leveson, Director of Content Marketing, HYPR The Payment Card Industry Security Standards Council recently updated their Data Security Standard (PCI DSS)...
Securing the Cloud: Unveiling the Significance of Strong Identity and Access Management (IAM) Strategies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Solvo In today’s rapidly evolving digital landscape, where businesses are increasingly migrating their operations to the cloud, the importance of robust...
BSidesTLV 2023 – Georgios Karantzas – It’s Duck Season: Forensic Detection Of BadUsb Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Executive Threat Protection: Using Monitoring to Gain the Advantage – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yuzuka Akasaka The risk of cyber threats has become an everyday reality for many organizations. This risk is amplified when it comes...
IBM Extends Cloudflare Alliance to Combat Bots Using Machine Learning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard IBM has extended its alliance with Cloudflare to employ machine learning algorithms to combat malicious bot attacks that are growing...
Play Ransomware Targets Victims Via MSPs’ RMM Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The Play ransomware operators who took credit for the attack on the city of Oakland, California, in February is now...
KubeCrash Fall 2023: Multi-Cluster Deployments at Enterprise Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Cook With KubeCon approaching fast (yes, November will be here before we know it), we’ve been preparing for KubeCrash, your cloud...
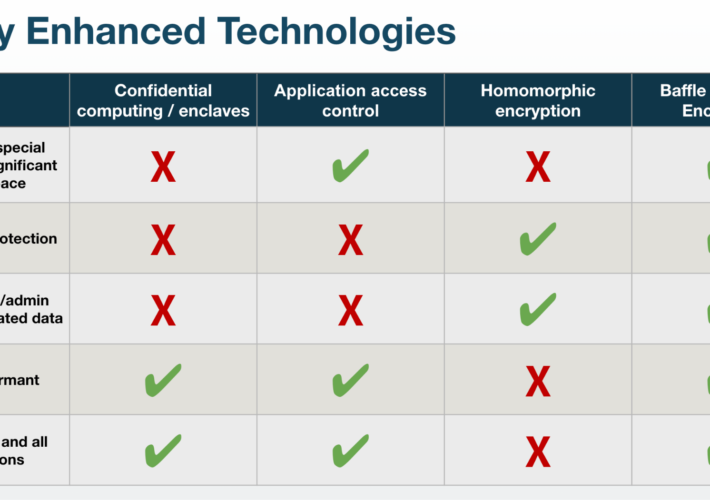
Privacy Enhanced Computation Technologies Advantages and Disadvantages – Source: securityboulevard.com
Source: securityboulevard.com – Author: Laura Case, Director of Product Management The acceleration of AI, machine learning, and large language model usage means more ways in which...
Daniel Stori’s ‘The (Sometimes Hard) Cloud Journey’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Impact of the New SEC Cyber Incident Reporting Rules on the C-Suite and Beyond – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog We recently hosted a compact and very engaging panel discussion about the new SEC Cyber Incident Reporting Rules due to come...
BlackCat Ransomware Variant Incorporates Impacket, RemCom – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Version Uses Open-Source Communication Framework Tool for Lateral Movement Prajeet Nair (@prajeetspeaks) • August 18,...
Endpoint Security Challenges in Manufacturing and Strategies to Alleviate Associated Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Massimo Carlotti Solutions Engineering Manager, Italy, CyberArk A sales engineer for more than 15 years, Carlotti excelled in consultant, business developer,...
Using AI to Separate the Good Signals From the Bad – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 SOC analysts and CISOs are experiencing burnout because the increased number of threats and the large amount of tools being used...
Critical Gaps in Securing Identities: Survey Results and Analysis – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Mass Phishing Campaign Targets Zimbra Users Worldwide – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Targets Include Small and Medium Businesses and Government Agencies Mihir Bagwe (MihirBagwe) • August...
LIVE Webinar | Fight (Ransomware) or Flight: A Threat Mitigation Discussion – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
ISMG Editors: Lessons Learned From the Lapsus$ Crime Group – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Video Also: Highlights from BlackHat 2023; Latest Cybersecurity M&A Activity Anna Delaney (annamadeline) •...