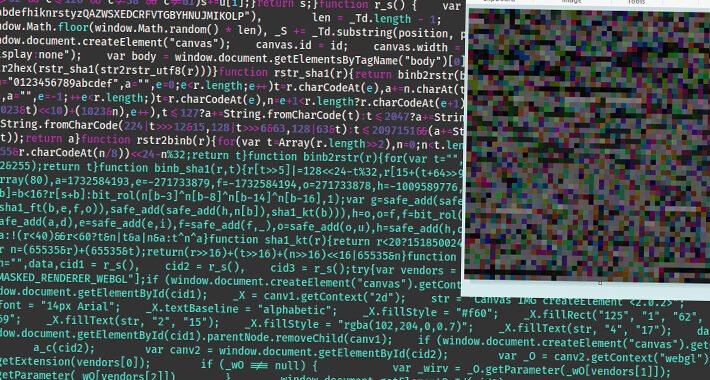
Source: www.bleepingcomputer.com – Author: Ax Sharma Serde, a popular Rust (de)serialization project, has decided to ship its serde_derive macro as a precompiled binary. The move has generated a fair...
Day: August 19, 2023
WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 19, 2023THNMalvertising / Website Security Cybersecurity researchers have detailed an updated version of an advanced fingerprinting and redirection toolkit called...
Friday Squid Blogging: Squid Brand Fish Sauce – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Squid Brand Fish Sauce Squid Brand is a Thai company that makes fish sauce: It is...
CyCognito Finds Large Volume of Personal Identifiable Information in Vulnerable Cloud and Web Applications – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ALO ALTO, Calif., Aug. 16, 2023 /PRNewswire/ — CyCognito, an External Attack Surface Management platform, today released its semi-annual “State of External Exposure Management,”...
ProjectDiscovery Announces $25M Series A Financing and Launch of Cloud Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 San Francisco, CA – August 17, 2023 – ProjectDiscovery, the open source powered security company that specializes in the detection of new,...
Phishing Attack Targets Hundreds of Zimbra Customers in 4 Continents – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Despite its simplicity, a phishing campaign targeting customers of the Zimbra Collaboration software suite has spread...
CISA Committee Tackles Remote Monitoring and Management Protections – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Just two years after Cybersecurity and Infrastructure Security Agency (CISA) Director Jen Easterly unveiled the Joint Cyber...
Bugcrowd Unleashes Hacker Ingenuity for Proactive, Crowdsourced Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Casey Ellis and Dave Gerry of Bugcrowd stress the importance of crowdsourced threat intelligence, and also detail...
Hubble Urges Customers, Security Pros to Return to Infosec Basics – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Hubble CEO Tom Parker has been encouraging a “back to basics” approach to cybersecurity for at least...
Comcast: How to Wrap Enterprise Cybersecurity In the Data Fabric – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Comcast’s Noopur Davis discusses how big data is reshaping the fundamentals around security management, along with the...
Securonix: Making Sense of AI’s Rapid Acceleration in Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Nayaki Nayyar of Securonix and Chris Inglis, former US National Cyber Director in the Biden administration, take...
Fortra Joins With Microsoft, Health-ISAC to Combat Cobalt Blue Fraud – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Bob Erdman of Fortra joins Dark Reading’s News Desk to talk about why his company teamed with...
New Juniper Junos OS Flaws Expose Devices to Remote Attacks – Patch Now – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 19, 2023THNNetwork Security / Vulnerability Networking hardware company Juniper Networks has released an “out-of-cycle” security update to address multiple flaws...
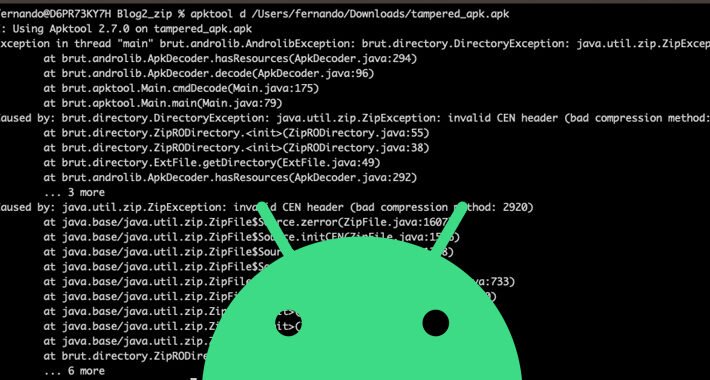
Thousands of Android Malware Apps Using Stealthy APK Compression to Evade Detection – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 19, 2023THNMobile Security / Malware Threat actors are using Android Package (APK) files with unknown or unsupported compression methods to...
BlackCat Ransomware Variant Incorporates Impacket, RemCom – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware Version Uses Open-Source Communication Framework Tool for Lateral Movement Prajeet Nair (@prajeetspeaks) • August 18,...
Endpoint Security Challenges in Manufacturing and Strategies to Alleviate Associated Risks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Massimo Carlotti Solutions Engineering Manager, Italy, CyberArk A sales engineer for more than 15 years, Carlotti excelled in consultant, business developer,...
Using AI to Separate the Good Signals From the Bad – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 SOC analysts and CISOs are experiencing burnout because the increased number of threats and the large amount of tools being used...
Critical Gaps in Securing Identities: Survey Results and Analysis – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Mass Phishing Campaign Targets Zimbra Users Worldwide – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Targets Include Small and Medium Businesses and Government Agencies Mihir Bagwe (MihirBagwe) • August...
LIVE Webinar | Fight (Ransomware) or Flight: A Threat Mitigation Discussion – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
ISMG Editors: Lessons Learned From the Lapsus$ Crime Group – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Video Also: Highlights from BlackHat 2023; Latest Cybersecurity M&A Activity Anna Delaney (annamadeline) •...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 0
Black Hat 2023 – AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 1
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 0
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 0