Source: thehackernews.com – Author: . Aug 18, 2023THNCyber Crime / Hacking News A coordinated law enforcement operation across 25 African countries has led to the arrest...
Day: August 18, 2023
The Vulnerability of Zero Trust: Lessons from the Storm 0558 Hack – Source:thehackernews.com
Source: thehackernews.com – Author: . While IT security managers in companies and public administrations rely on the concept of Zero Trust, APTS (Advanced Persistent Threats) are...
New Wave of Attack Campaign Targeting Zimbra Email Users for Credential Theft – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 18, 2023THNEmail Seucrity / Cyber Attack A new “mass-spreading” social engineering campaign is targeting users of the Zimbra Collaboration email...
New BlackCat Ransomware Variant Adopts Advanced Impacket and RemCom Tools – Source:thehackernews.com
Source: thehackernews.com – Author: . Microsoft on Thursday disclosed that it found a new version of the BlackCat ransomware (aka ALPHV and Noberus) that embeds tools...
BlackCat Sphynx: The Ransomware Operation Evolves Once Again – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Researchers at Microsoft discovered a new version of the BlackCat ransomware. Dubbed ‘Sphynx’, this version embeds the Impacket networking framework...
What Is Next-Generation Antivirus (NGAV) and How Does It Work? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac As the cybercrime landscape evolves, you may wonder if the old Antivirus solution that you have installed on your organization’s...
Patch Management vs Vulnerability Management: A Comparison – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Patch management is nowadays a necessity for every company that wants to stay safe from cyberattacks, and to ensure that...
Ongoing Phishing Campaign Targets Zimbra Collaborations Email Servers Worldwide – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Zimbra Collaboration email servers worldwide are being targeted by threat actors. Recently, cybersecurity researchers have uncovered an ongoing phishing campaign,...
Short Staffed in Cybersecurity? It’s Time for MXDR! – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal In today’s rapidly evolving digital landscape, cybersecurity has become a paramount concern for businesses and individuals alike. The increasing frequency...
Egregor Ransomware Analysis: Origins, M.O., Victims – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cezarina Dinu A new year brings about countless new opportunities, but also, unfortunately, the chance for old threats to make a comeback...
Unveiling the Hidden Risks of Routing Protocols – Source: www.darkreading.com
Source: www.darkreading.com – Author: Daniel dos Santos, Head of Security Research, Forescout’s Vedere Labs Routing protocols play a critical role in the functioning of the Internet...
Fastly Launches Certainly CA – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Edge cloud platform provider Fastly has announced the general availability of Certainly, its publicly trusted Transport Layer...
Confusion Surrounds SEC’s New Cybersecurity Material Rule – Source: www.darkreading.com
Source: www.darkreading.com – Author: Evan Schuman, Contributing Writer, Dark Reading One of the aims of the new cybersecurity disclosure rules approved by the Securities Exchange Commission...
Infoblox Blows Whistle On ‘Decoy Dog,’ Advocates For Better DNS Monitoring – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Renée Burton of Infoblox unveils the inner workings of Decoy Dog/Pupy, the RAT toolkit that uses the...
TXOne: How to Improve Your Operational Technology Security Posture – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading As operational technology (OT) gets more networked, these industrial networks are more prone to ransomware and supply...
Cribl, Exabeam Partner on Threat Detection, Investigation, and Response – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Abby Strong of Cribl and Chris Cesio of Exabeam talk about their companies’ recent partnership designed to...
Interpres: Getting the Most Out of Threat Intelligence Resources – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Nick Lantuh of Interpres talks about the shortcomings of the threat intel industry and how security pros...
Qualys Offers Threat Forecast For Cloud, and Tips For Reducing Cloud Risks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Sumedh Thakar of Qualys talks about how security vendors must translate cloud customer needs into effective solutions,...
Normalyze: How Focusing on Data Can Improve Cloud Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Normalyze’s Ravi Ithal deconstructs data security posture management (DPSM), how it differs from conventional data security management,...
White House Orders Federal Agencies to Bolster Cyber Safeguards – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The White House has ordered federal agencies to get their cybersecurity safeguards up to date as they...
Bots Are Better than Humans at Solving CAPTCHAs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting research: “An Empirical Study & Evaluation of Modern CAPTCHAs“: Abstract: For nearly two decades, CAPTCHAS have been widely used...
Google Chrome’s New Feature Alerts Users About Auto-Removal of Malicious Extensions – Source:thehackernews.com
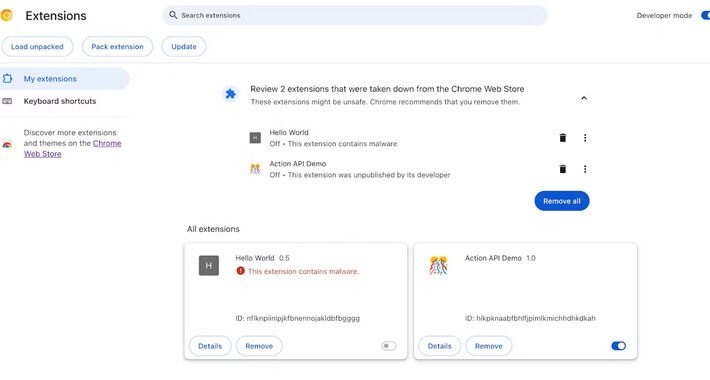
Source: thehackernews.com – Author: . Aug 18, 2023THNBrowser Security / Malware Google has announced plans to add a new feature in the upcoming version of its...
Microsoft: BlackCat’s Sphynx ransomware embeds Impacket, RemCom – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has discovered a new version of the BlackCat ransomware that embeds the Impacket networking framework and the Remcom hacking...
Hackers ask $120,000 for access to multi-billion auction house – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Hackers claim to have breached the network of a major auction house and offered access to whoever was willing to...
Microsoft PowerShell Gallery vulnerable to spoofing, supply chain attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Lax policies for package naming on Microsoft’s PowerShell Gallery code repository allow threat actors to perform typosquatting attacks, spoof popular...
Phishing campaign steals accounts for Zimbra email servers worlwide – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An ongoing phishing campaign has been underway since at least April 2023 that attempts to steal credentials for Zimbra Collaboration...
Windows Task Manager refresh can be paused using CTRL key – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A very useful and previously unknown Windows tip was revealed this week, where you can halt process jumping in Task...
Thousands of Android APKs use compression trick to thwart analysis – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Threat actors increasingly distribute malicious Android APKs (packaged app installers) that resist decompilation using unsupported, unknown, or heavily tweaked compression...
Triple Extortion Ransomware and the Cybercrime Supply Chain – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Flare Ransomware attacks continue to grow both in sophistication and quantity. 2023 has already seen more ransomware attacks involving data...
Malware Is Turning Windows Machines Into Proxies – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime as-a-service , Fraud Management & Cybercrime , Social Engineering Proxy App Is Covertly Installed Via Alluring Offers or Compromised Software...