Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading John Shier of Sophos shares findings of a company report on “Royal,” a dangerous new variation of...
Day: August 17, 2023
Israel-US Binational Industrial R&D Foundation to Invest $3.85M in Critical Infrastructure Cybersecurity Projects – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TEL AVIV, Israel, Aug. 17, 2023 /PRNewswire/ — While the cybersecurity industry experienced record-breaking investments and continuous growth in recent years, most cyber...
Intelligent Vigilance: Empowering Security with Threat Intel’s CoPilot AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Cybersixgill’s Michael-Angelo Zummo talks about the impact of artificial intelligence, and the issues and questions it creates...
Cisco: Bringing More Intelligence to Bear on the Threat Landscape – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Cisco’s Nick Biasini describes how attackers’ tactics, techniques, and procedures continue to increase in sophistication, and what...
ISC2 Announces Milestone as Community Grows to Half a Million – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ALEXANDRIA, Va., Aug. 17, 2023 /PRNewswire/ — The world’s leading nonprofit member organization for cybersecurity professionals, formerly known as (ISC)², has today announced that...
Foretrace Announces Launch of “Tim,” Generative AI Analyst for Assessing and Responding to Data Leaks – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 COLUMBIA, Md,, Aug. 17, 2023 /PRNewswire-PRWeb/ — Foretrace, the leader in data leak and exposure management, today announced the release of “Tim,” a generative...
How to Protect Against Nation-State APT Attackers Leveraging Mobile Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Justin Albrecht of Lookout takes on the phenomenon of nation-state-sponsored attackers targeting mobile users with advanced persistent...
CrowdSec: What the ‘Network Effect’ Brings to the Cybersecurity Table – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The value of a utility increases as more people use it —and Philippe Humeau of CrowdSec shows...
Securing Critical Infrastructure in the Face of Evolving Cyber Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Benny Czarny of OPSWAT outlines the threat landscape affecting critical infrastructure sectors, and how those organizations can...
Bitsight Leverages SPM to Bolster External Attack Surface Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Bitsight’s Greg Keshian checks the status of external attack surface management and how the emerging discipline of...
Cyber Alert: Global Campaign Targets LinkedIn Accounts – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In a sweeping global campaign, LinkedIn users are falling victim to a surge of account hijacks, leaving many locked out...
Raccoon Stealer 2.3.0 Malware – A Stealthier Comeback – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In a notable comeback, the creators of the notorious Raccoon Stealer information-stealing malware have reemerged after a six-month hiatus. This...
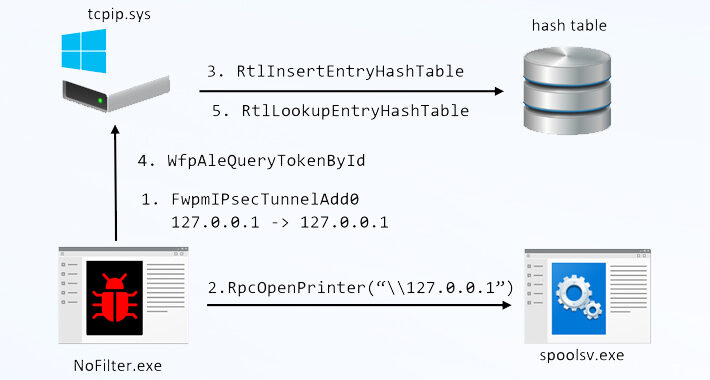
NoFilter Attack: Sneaky Privilege Escalation Method Bypasses Windows Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 17, 2023THNEndpoint Security / Vulnerability A previously undetected attack method called NoFilter has been found to abuse the Windows Filtering...
China-Linked Bronze Starlight Group Targeting Gambling Sector with Cobalt Strike Beacons – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 17, 2023THNCyber Attack / Malware An ongoing cyber attack campaign originating from China is targeting the Southeast Asian gambling sector...
New LABRAT Campaign Exploits GitLab Flaw for Cryptojacking and Proxyjacking Activities – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 17, 2023THNCryptojacking / Proxyjacking A new, financially motivated operation dubbed LABRAT has been observed weaponizing a now-patched critical flaw in...
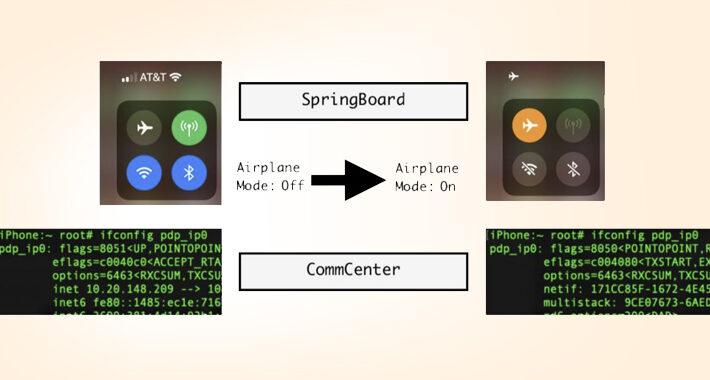
New Apple iOS 16 Exploit Enables Stealthy Cellular Access Under Fake Airplane Mode – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 17, 2023THNMobile Security / Vulnerability Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could be...
Why You Need Continuous Network Monitoring? – Source:thehackernews.com
Source: thehackernews.com – Author: . Changes in the way we work have had significant implications for cybersecurity, not least in network monitoring. Workers no longer sit...
File sharing site Anonfiles shuts down due to overwhelming abuse – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Anonfiles, a popular service for sharing files anonymously, has shut down after saying it can no longer deal with the...
CISA warns of critical Citrix ShareFile flaw exploited in the wild – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams CISA is warning that a critical Citrix ShareFile secure file transfer vulnerability tracked as CVE-2023-24489 is being targeted by unknown...
Detecting “Violations of Social Norms” in Text with AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Detecting “Violations of Social Norms” in Text with AI Researchers are trying to use AI to detect “social norms...
UK Electoral Commission Hacked – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The UK Electoral Commission discovered last year that it was hacked the year before. That’s fourteen months between the hack...
Russian Hackers Use Zulip Chat App for Covert C&C in Diplomatic Phishing Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 17, 2023THNCyber Espionage / Malware An ongoing campaign targeting ministries of foreign affairs of NATO-aligned countries points to the involvement...
CISA Adds Citrix ShareFile Flaw to KEV Catalog Due to In-the-Wild Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 17, 2023THNVulnerability / Enterprise Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw in...
German Police Warn of Increased Foreign Cybercrime Threat – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime BKA Says Cybercrime From Overseas Actors Surged by 8% in 2022 Akshaya...
Cisco Secure Access: SSE That Enables the Business – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud-Delivered Security Service Edge Solution Gives Efficient Hybrid Work Security Jeff Scheaffer, Vice President of Product Management (SSE, SASE and Security...
AI in XDR: When Does It Make Sense? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cisco’s AJ Shipley on When Generative AI Is Useful and When It’s Dangerous AJ Shipley, Vice President, Product – Threat Detection...
How Generative AI Will Improve Incident Response – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Generative AI will play a role in the future of incident response. It will be used in EDR tools and vulnerability...
RiskLens, Axio Lead Cyber Risk Quantification Forrester Wave – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , IT Risk Management , Risk Assessments ThreatConnect Earns High Marks as CRQ Helps CISOs Prove Return...
LIVE Webinar | Before & After AWS: Transforming Cloud’s Most Common Pitfalls into Progress – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Nate Kettlewell Principal, Application Security, Coalfire Nate Kettlewell is a specialist in information security, network engineering, and web application security. His...
Advocate Aurora to Settle Web Tracker Claims for $12.25M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Healthcare , HIPAA/HITECH Attorneys to Get $4.3M and Class Reps to Get $3,500 Each Under Proposed...