Source: www.securityweek.com – Author: Ionut Arghire The US government announced on Friday that the DHS’s Cyber Safety Review Board (CSRB) will conduct a review on malicious...
Day: August 15, 2023
Power Management Product Flaws Can Expose Data Centers to Damaging Attacks, Spying – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Vulnerabilities in power management products made by CyberPower and Dataprobe could be exploited in attacks aimed at data centers, allowing...
US Shuts Down Bulletproof Hosting Service LolekHosted, Charges Its Polish Operator – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire US authorities have announced the seizure of LolekHosted.net, the domain used by the bulletproof hosting service LolekHosted, as well as...
Ford Says Wi-Fi Vulnerability Not a Safety Risk to Vehicles – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire American car maker Ford says that a vulnerability in the Wi-Fi driver of the SYNC 3 infotainment system on certain...
Iagona ScrutisWeb Vulnerabilities Could Expose ATMs to Remote Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Several vulnerabilities discovered in the ScrutisWeb ATM fleet monitoring software made by French company Iagona could be exploited to remotely...
FBI: Mobile Beta-Testing Apps Are Major Security Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The FBI has warned consumers not to download apps labelled as in beta test mode as they might be involved in...
China Hacked Japan’s Military Networks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The NSA discovered the intrusion in 2020—we don’t know how—and alerted the Japanese. The Washington Post has the story: The...
Threat actors use beta apps to bypass mobile app store security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The FBI is warning of a new tactic used by cybercriminals where they promote malicious “beta” versions of cryptocurrency investment...
Discord.io confirms breach after hacker steals data of 760K users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Updated: Added further information from Akihirah about the sale of the database. The Discord.io custom invite service has temporarily shut down...
Over 100K hacking forums accounts exposed by info-stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Researchers discovered 120,000 infected systems that contained credentials for cybercrime forums. Many of the computers belong to hackers, the researchers...
Microsoft enables Windows Kernel CVE-2023-32019 fix for everyone – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has enabled a fix for a Kernel information disclosure vulnerability by default for everyone after previously disabling it out...
FBI warns of increasing cryptocurrency recovery scams – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The FBI is warning of an increase in scammers pretending to be recovery companies that can help victims of cryptocurrency...
Monti ransomware targets VMware ESXi servers with new Linux locker – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Monti ransomware gang has returned, after a two-month break from publishing victims on their data leak site, using a new...
Criminal IP Teams Up with PolySwarm to Strengthen Threat Detection – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Criminal IP In today’s ever-evolving digital landscape, the significance of effective malware detection remains paramount. With the escalating threat of...
Colorado warns 4 million of data stolen in IBM MOVEit breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney The Colorado Department of Health Care Policy & Financing (HCPF) is alerting more than four million individuals of a...
MaginotDNS attacks exploit weak checks for DNS cache poisoning – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A team of researchers from UC Irvine and Tsinghua University has developed a new powerful cache poisoning attack named ‘MaginotDNS,’...
Top 10 Key Takeaways on Navigating End-User Computing (EUC) Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kimberly Rose In today’s digital age, as businesses heavily rely on End-User Computing (EUC) tools, the landscape of risks they face has...
Diligere, Equity-Invest Are New Firms of U.K. Con Man – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs John Clifton Davies, a convicted fraudster estimated to have bilked dozens of technology startups out of more than $30 million through...
Blameless Locks Down Security Incident Management Over Slack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Blameless is making it simpler for security operations (SecOps) teams to manage multiple conversations across the Slack instant messaging platform...
BSides Leeds 2023 – Samantha Humphries – Destination Unknown: Career Musings Of A Former [Redacted] Agent – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Monti Returns From 2-Month Break with Revamped Ransomware Variant – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The Monti ransomware group that emerged in June 2022 used source code, tools, and tactics – not to mention an...
The Price of Convenience: How Security Vulnerabilities in Global Transportation Payment Systems Can Cost You – Source: securityboulevard.com
Source: securityboulevard.com – Author: Omer Attias Public transportation payment systems have undergone significant changes over the years. Mobile payment solutions have become increasingly popular, allowing passengers...
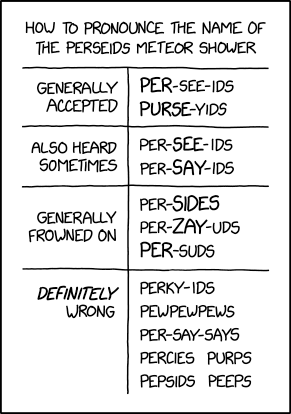
Randall Munroe’s XKCD ‘Perseids Pronunciation’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Mitigating Human Errors in Cybersecurity & Compliance: Practical Tips for Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Adar Givoni, Director of Compliance, Scytale The Importance of Cybersecurity Cybersecurity is of paramount importance in today’s digital world. With the increasing...
OWASP researcher: Supply chain attacks show organizations must shift beyond vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Carolynn van Arsdale It’s not news that software supply chain attacks have become a pervasive threat. They have increased greatly — while...
Activist Investor Directs OneSpan to Pursue ‘Immediate Sale’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Identity & Access Management , Security Operations Legion Partners Calls on Identity Verification Provider to Reduce Costs, Find Buyer Michael Novinson...
Live Webinar | Security Leaders: How to Achieve SEC Compliance – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
How to Block API Attacks in Real Time – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 API Security The Different Types of API Attacks and Best Practices for API Security Shay Levi • August 3, 2023 ...
Multiple Flaws Uncovered in Data Center Systems – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Vulnerabilities Found in CyberPower and Dataprobe Products Prajeet Nair (@prajeetspeaks) • August 14, 2023...
Live Webinar | Government Intervention: The Rise of the SBOM and the Evolution of Software Supply Chain Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Ilkka Turunen Field CTO, Sonatype lkka Turunen is Field CTO at Sonatype, working with leading companies across the globe to understand...


















![bsides-leeds-2023-–-samantha-humphries-–-destination-unknown:-career-musings-of-a-former-[redacted]-agent-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2023/08/74074/bsides-leeds-2023-samantha-humphries-destination-unknown-career-musings-of-a-former-redacted-agent-source-securityboulevard-com-710x500.jpg)