Source: heimdalsecurity.com – Author: Mihaela Popa The ransomware operation known as Rhysida has rapidly gained notoriety, especially following a series of attacks on healthcare organizations. This...
Day: August 11, 2023
Gafgyt malware exploits five-years-old flaw in EoL Zyxel router – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Fortinet has issued an alert warning that the Gafgyt botnet malware is actively trying to exploit a vulnerability in the...
Microsoft Exchange updates pulled after breaking non-English installs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has pulled Microsoft Exchange Server’s August security updates from Windows Update after finding they break Exchange on non-English installs. On...
MoustachedBouncer hackers use AiTM attacks to spy on diplomats – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney A cyberespionage group named ‘MoustachedBouncer’ has been observed using adversary-in-the-middle (AitM) attacks at ISPs to hack foreign embassies...
CISA: New Whirlpool backdoor used in Barracuda ESG hacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has discovered a new backdoor malware named ‘Whirlpool’ used in...
Dell Compellent hardcoded key exposes VMware vCenter admin creds – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas An unfixed hardcoded encryption key flaw in Dell’s Compellent Integration Tools for VMware (CITV) allows attackers to decrypt stored vCenter...
Safeguarding Against Silent Cyber Threats: Exploring the Stealer Log Lifecycle – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Flare The first seven months of 2023 have seen a continued rapid evolution of the cybercrime ecosystem. Ransomware data exfiltration...
Lexmark Command Injection Vulnerability ZDI-CAN-19470 Pwn2Own Toronto 2022 – Source: securityboulevard.com
Source: securityboulevard.com – Author: James Horseman In December 2022, we competed at our first pwn2own. We were able to successfully exploit the Lexmark MC3224i using a...
Traceable AI Extends Reach to Combat Fraudulent API Activity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Traceable AI has extended the reach of its application security platform to detect and thwart fraudulent activities enabled by the...
What is the democratization of fraud? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team Advancements in technology have come a long way to enable fraud teams, but cybercriminals are getting more...
BSides Leeds 2023 – Sean Wright – Docker To The Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsides-leeds-2023-sean-wright-docker-to-the-security/ Category & Tags: CISO Suite,Governance, Risk &...
My Favorite Things: Hardware Hacking and Reverse Engineering – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Asadoorian Favorite (Hacking) Things I really enjoy researching and acquiring “gadgets”. Recently, I spent a little time with Eclypsium’s research team...
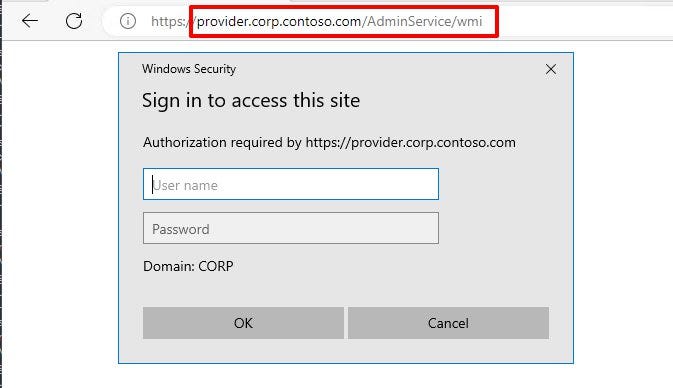
Site Takeover via SCCM’s AdminService API – Source: securityboulevard.com
Source: securityboulevard.com – Author: Garrett Foster tl:dr: The SCCM AdminService API is vulnerable to NTLM relaying and can be abused for SCCM site takeover. Prior Work...
SSPM to the Rescue: Accelerating SaaS Incident Response by 90% – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emile Antone With the SaaS market on pace to grow by nearly 19 percent annually and become a $900 billion dollar industry...
Zero-Day Flaws an Evolving Weapon in Ransomware Groups’ Arsenals – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Ransomware gangs have for years gotten their malicious payloads into targeted systems primarily through phishing attacks or being dropped as...
Randall Munroe’s XKCD ‘What to Do’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/randall-munroes-xkcd-what-to-do/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
Validating the Security Posture of Cohesity DataPlatform with StorageGuard – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jon Ruback and Yaniv Valik In today’s digital landscape, data management solutions have become a critical component of every enterprise’s operations. Cohesity...
Attackers Use EvilProxy to target C-suite Excecutives – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Phishing Kit Primarily Used in Attacks Against Employees of Fortune 500 Companies Prajeet Nair...
Secondary Market Medical Device Security Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Healthcare , Industry Specific Researcher Deral Heiland of Rapid7 on Legacy Device Security Issues Marianne Kolbasuk McGee (HealthInfoSec)...
Researchers Uncover ‘Inception’ Flaw in AMD CPUs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Hardware / Chip-level Security Vulnerability Allows Manipulation of CPU to Leak Data Akshaya Asokan (asokan_akshaya) • August 10,...
Proof of Concept: Managing Software Supply Chain Woes – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Governance & Risk Management , Standards, Regulations & Compliance Also: Lessons Learned From the MOVEit Breaches;...
Chinese RedHotel Spy Group Linked to Hacks in 17 Countries – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Motives, Operations Closely Linked to China’s Ministry...