Source: thehackernews.com – Author: . Aug 10, 2023THNCyber Crime / Hacking Interpol has announced the takedown of a phishing-as-a-service (PhaaS) platform called 16Shop, in addition to...
Day: August 10, 2023
Common TTPs of attacks against industrial organizations – Source: securelist.com
Source: securelist.com – Author: Kirill Kruglov, Vyacheslav Kopeytsev, Artem Snegirev In 2022 we investigated a series of attacks against industrial organizations in Eastern Europe. In the...
Hackers use open source Merlin post-exploitation toolkit in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Ukraine is warning of a wave of attacks targeting state organizations using ‘Merlin,’ an open-source post-exploitation and command and control...
New BitForge cryptocurrency wallet flaws lets hackers steal crypto – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney Multiple zero-day vulnerabilities named ‘BitForge’ in the implementation of widely used cryptographic protocols like GG-18, GG-20, and Lindell...
Missouri warns that health info was stolen in IBM MOVEit data breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Missouri’s Department of Social Services warns that protected Medicaid healthcare information was exposed in a data breach after IBM suffered...
Rhysida ransomware behind recent attacks on healthcare – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Rhysida ransomware operation is making a name for itself after a wave of attacks on healthcare organizations has forced...
Popular open source project Moq criticized for quietly collecting data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Open source project Moq (pronounced “Mock”) has drawn sharp criticism for quietly including a controversial dependency in its latest release. Distributed...
Google to fight hackers with weekly Chrome security updates – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google has changed the Google Chrome security updates schedule from bi-weekly to weekly to address the growing patch gap problem...
The Aftermath: Dallas Ransomware Attack- 26K Residents Affected – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In a recent development, it has come to light that an APT group managed to infiltrate the city of Dallas’...
Preventative medicine for securing IoT tech in healthcare organizations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 The widespread adoption of a digital transformation workspace and the shift to web applications has led to a global...
EvilProxy phishing campaign targets 120,000 Microsoft 365 users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas EvilProxy is becoming one of the more popular phishing platforms to target MFA-protected accounts, with researchers seeing 120,000 phishing emails...
Microsoft Patch Tuesday, August 2023 Edition – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Microsoft Corp. today issued software updates to plug more than 70 security holes in its Windows operating systems and related products,...
The Power of Risk-Based Authentication With HYPR Adapt – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Rothschild, VP of Product Marketing, HYPR Organizations globally face unprecedented challenges in safeguarding their sensitive data, critical assets, and reputation from...
Anton’s Security Blog Quarterly Q3 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin Wednesday, August 9, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Hacking With Your Nemesis – Source: securityboulevard.com
Source: securityboulevard.com – Author: Will Schroeder In the first post in this series, On (Structured) Data, we talked about the gap area of offensive structured data...
Cequence named winner in the Enterprise Security Tech 2023 Cyber Top 20 Awards List – Source: securityboulevard.com
Source: securityboulevard.com – Author: Varun Kohli Cequence is pleased to announce that we have been named to the Enterprise Security Tech 2023 Cyber Top 20 Awards...
Fortra Introduces New Integrations for Offensive Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by HelpSystems Combining pen testing, red teaming, and vulnerability management for more robust security MINNEAPOLIS – Aug 9, 2023 –...
CrowdStrike Launches Managed Service Focused on Protecting Credentials – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard CrowdStrike this week added a managed service to disrupt the operations of cybercriminals that have evolved their tactics and techniques...
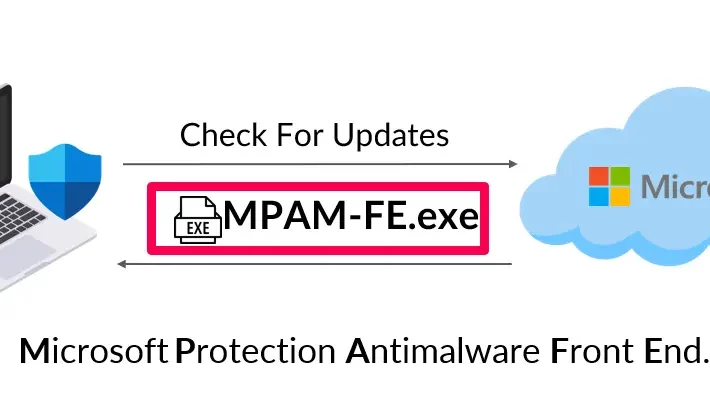
Defender Pretender: When Windows Defender Updates Become a Security Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tomer Bar Author: Tomer Bar, Director of Security Research, SafeBreach The SafeBreach Labs team is committed to conducting original research to uncover...
BSides Leeds 2023 – Michael Ndon – Stop Breaking Into Cyber Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsides-leeds-2023-michael-ndon-stop-breaking-into-cyber-security/ Category & Tags: CISO Suite,Governance, Risk &...
Threat Roundup: Microsoft August Patch Tuesday & New PaperCut Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire August is off to a busy start for cyberthreats. In this article, we’ll recap Microsoft’s August Patch Tuesday announcement and...
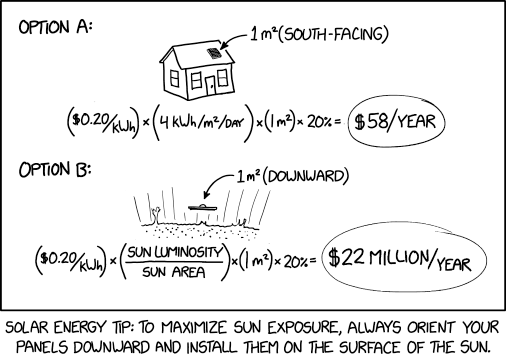
Randall Munroe’s XKCD ‘Solar Panel Placement’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/randall-munroes-xkcd-solar-panel-placement/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
Law Enforcement Takes Down Phishing As A Service Site – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime as-a-service , Fraud Management & Cybercrime Authorities In Multiple Countries Arrest Operators of 16Shop Mihir Bagwe (MihirBagwe) • August 9,...
Defending Against Real-Time Financial Fraud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The Federal Reserve Board launched its real-time payment tool, the FedNow Service, in July. Cash transfer applications that make instant payments...
Live Webinar | SaaS: The Gaping Hole in Your Disaster Recovery Plan – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
US Restricts Investment in Chinese AI, Other Technologies – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Executive Order Targets Dual-Use AI, Semiconductors and Quantum IT David...
Live Webinar | Best Strategies for Transferring Sensitive Financial Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Encryption & Key Management , Finance & Banking Presented by Fortra 60 mins For...
Live Webinar | Beyond Zero Trust: Incorporating SASE for Secure Remote Access – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Marcus Ward GM & Product Director, Datto Networking Marcus Ward is the GM and Product Director for Datto Networking and brings...
Lawsuits Mounting Against Florida Hospital in Wake of Breach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Governance & Risk Management , Healthcare So Far, 3 Proposed Class Actions Allege Negligence in Case Affecting 1.3M...
Ukraine Fends Off Sandworm Battlefield Espionage Ploy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Endpoint Security , Fraud Management & Cybercrime Russian Military Hackers Planned Mobile Device Malware Campaign Mihir...