Source: www.infosecurity-magazine.com – Author: 1 Researchers have warned of a new multi-factor authentication (MFA) phishing campaign targeting thousands of users, including a large share of C-suite...
Day: August 10, 2023
NIST Expands Cybersecurity Framework with New Pillar – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US National Institute of Standards and Technology (NIST) has released a new draft version of its popular best practice security...
#BHUSA: New Zero-Day Vulnerabilities Could Instantly Drain Crypto Wallets – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Multiple zero-day vulnerabilities have been discovered in some of the most used cryptographic multi-party computation (MPC) protocols, putting consumers’ cryptocurrency funds...
Smashing Security podcast #334: Acoustic attacks, and the tears of a crypto rapper – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Razzlekhan, the self-proclaimed Crocodile of Wall Street, pleads guilty to the biggest crypto laundering scheme in history, and just how...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
‘MoustachedBouncer’ APT Spies on Embassies, Likely via ISPs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading BLACK HAT USA – Las Vegas – Thursday, Aug. 10 — A Belarus-linked APT spied on...
DARPA Launches 2-Year Contest to Build AI Tools to Fix Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9 — The Defense Advanced Research Projects...
LastPass Announces Availability of FIDO2 Authenticators for Passwordless Login – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 BOSTON — (BUSINESS WIRE) — LastPass today announced the availability of FIDO2 authenticators, including biometrics, such as finger print or face ID, and...
Sweet Security Lands $12M in Seed Funding to Shift Cloud Security Right – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 TEL AVIV, Israel, Aug. 9, 2023 /PRNewswire/ — Sweet Security today announced $12 million in seed funding and the launch of its Cloud Runtime Security...
Symmetry Systems Closes $17.7M To Scale its AI-Powered Data Security Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN JOSE, Calif., Aug. 9, 2023 /PRNewswire/ — Symmetry Systems, a next generation AI-powered data-centric security company, today announced an $17.7 million inside round of funding...
Checkmarx CISO Study Finds 96% of CISOs Say Their Business Prospects Consider Their Organizations’ AppSec Maturity When Making Deal Decisions – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ATLANTA, Aug. 9, 2023 /PRNewswire/ — Checkmarx today released its “Global CISO Survey: The Growing Impact of AppSec on Business” report, based on survey...
Blockchain Signing Bug Cracks Open Crypto Investors’ Wallets Worldwide – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading BLACK HAT USA — Las Vegas – Wednesday, Aug. 9 Vulnerabilities in protocols used by major cryptocurrency...
Black Hat Opens With Call to Steer AI from Predictions to Policy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9 – A lot has changed, “but...
Windows Defender-Pretender Attack Dismantles Flagship Microsoft EDR – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9: Among the 97 CVEs that Microsoft patched...
Disposed-of Gadgets Can Lead to Wi-Fi Network Hacks, Kaspersky Says – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading When disposing of old technology — such as old phones, computers, printers, and smartwatches — it’s essential...
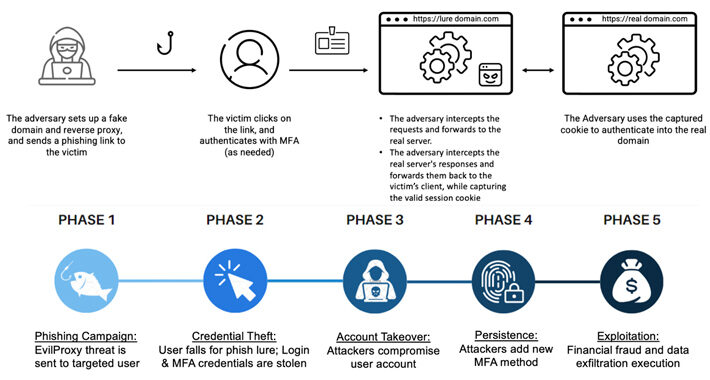
Cybercriminals Increasingly Using EvilProxy Phishing Kit to Target Executives – Source:thehackernews.com
Source: thehackernews.com – Author: . Threat actors are increasingly using a phishing-as-a-service (PhaaS) toolkit dubbed EvilProxy to pull off account takeover attacks aimed at high-ranking executives...