Source: thehackernews.com – Author: . Cybersecurity researchers have disclosed details of a trio of side-channel attacks that could be exploited to leak sensitive data from modern...
Day: August 9, 2023
China-Linked Hackers Strike Worldwide: 17 Nations Hit in 3-Year Cyber Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 09, 2023THNCyber Espionage / Cyber Attacks Hackers associated with China’s Ministry of State Security (MSS) have been linked to attacks...
Continuous Security Validation with Penetration Testing as a Service (PTaaS) – Source:thehackernews.com
Source: thehackernews.com – Author: . Validate security continuously across your full stack with Pen Testing as a Service. In today’s modern security operations center (SOC), it’s...
EU General Data Protection Regulation Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: The EU General Data Protection Regulation is a comprehensive set of rules designed to keep the personal data of all EU citizens...
Top 3 Insights I Learned at Recent Cybersecurity Events – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michael Adams, Chief Information Security Officer, Zoom In the dynamic world of cybersecurity, organizations must work together to keep people safe. Attending...
C-Suite Cybersecurity Sign-off Hinges on Customer Trust, Digital Opps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9 Security teams looking to justify more cyber...
OWASP Lead Flags Gaping Hole in Software Supply Chain Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9 The founder and lead of the open-source OWASP‘s...
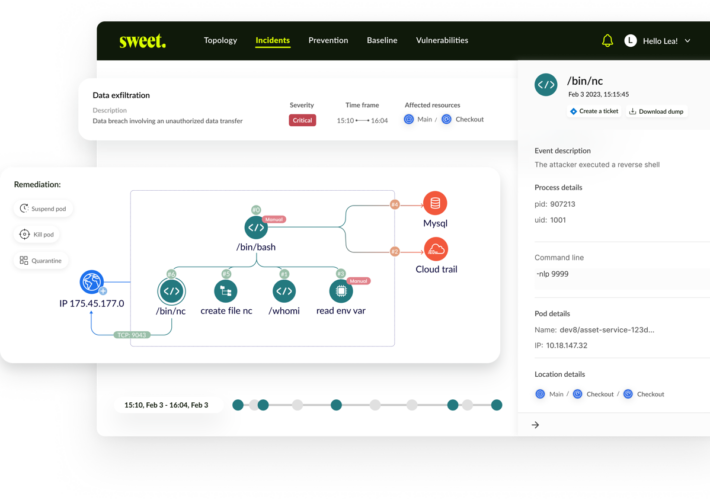
Sweet Security Debuts Runtime Management for Cloud – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Israeli cloud security startup Sweet Security has introduced its first product, Cloud Runtime Security Suite. Founded by...
Interpol Shuts Down African Cybercrime Group, Seizes $2 Million – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A cross-border investigation into West African cybercriminal groups has resulted in 103 arrests and the seizure of...
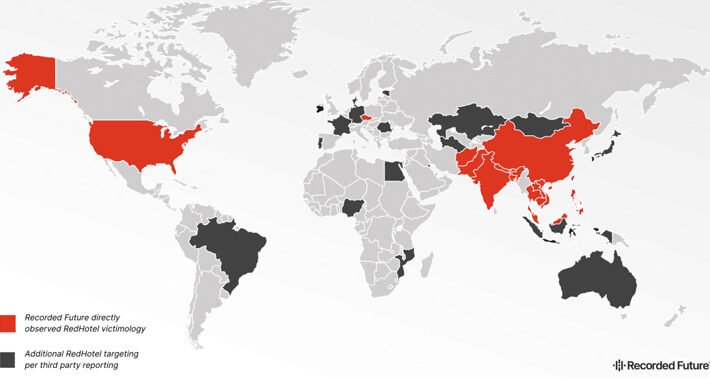
RedHotel Checks in as Dominant China-Backed Cyberspy Group – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading An advanced persistent threat (APT) is pulling ahead in a crowded field of China state-sponsored actors as...
AI Risk Database Tackles AI Supply Chain Risks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer, Dark Reading An emerging free tool that analyzes artificial intelligence (AI) models for risk has set a path...
Why Shellshock Remains a Cybersecurity Threat After 9 Years – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeremy Ventura, Director, Security Strategy, Field CISO, @ThreatX The Shellshock vulnerability got a lot of attention when it was first disclosed in...
TUNE IN Dark Reading News Desk: Live at Black Hat USA 2023 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Dark Reading News Desk Live at Black Hat USA 2023 Source: Dark Reading, Informa Tech Welcome to...
Zero trust and beyond – Navigating the era of generative AI challenges – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau At Check Point, I am responsible for enabling National Channel Partners to drive sales and increase revenue by developing technical training...
Rhysida Ransomware Analysis Reveals Vice Society Connection – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Rhysida ransomware group, a recent addition to the growing threat landscape, has been implicated in a string of high-impact attacks...
Breach Connected to MOVEit Flaw Affects Missouri Medicaid Recipients – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Missouri Department of Social Services (DSS) has issued an alert urging residents to safeguard their personal information following a cyber-attack...
High-Severity Access Control Vulnerability Found in Spring WebFlux – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new security loophole has been found in Spring Security’s latest versions. Tracked as CVE-2023-34034, the flaw has a CVSS score...
Rapid7 Lays Off 18% of Employees Amid Shift to MDR Services – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Managed Detection & Response (MDR) , Security Information & Event Management (SIEM) , Security Operations Loss of 470 Workers Is Cybersecurity...
Defending Against Real-Time Financial Fraud – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 The Federal Reserve Board launched its real-time payment tool, the FedNow Service, in July. Cash transfer applications that make instant payments...
Northern Ireland Police at Risk After Serious Data Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Security Operations Current PSNI Employees’ Surnames and Locations Revealed Via Public Spreadsheet Mathew J. Schwartz (euroinfosec) • August...
How to Implement a Modern Security Tech Stack to Increase Detection Coverage – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Rahul Gupta Head of Security & GRC, Sigma Computing Rahul is a Cyber Security and compliance leader with 17 years of...
UK Electoral Commission Suffered ‘Complex’ Hack in 2021 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Incident & Breach Response , Security Operations Agency Detected the Incident in October 2022 – Over 1 Year After the Hack...
Rubrik Buys Startup Laminar to Unify Cyber Posture, Recovery – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Data Loss Prevention (DLP) , Endpoint Security Rubrik Spent More Than $100M to Acquire the Data Security Posture Management Vendor Michael...
Using Machine Learning to Detect Keystrokes – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Researchers have trained a ML model to detect keystrokes by sound with 95% accuracy. “A Practical Deep Learning-Based Acoustic Side...
Downfall Intel CPU side-channel attack exposes sensitive data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google researcher Daniel Moghimi devised a new side-channel attack technique, named Downfall, against Intel CPU. Google researcher Daniel Moghimi devised...
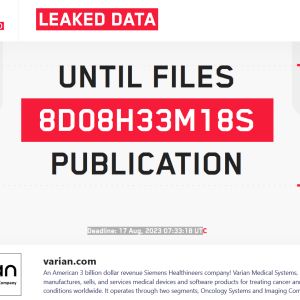
LockBit threatens to leak medical data of cancer patients stolen from Varian Medical Systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The LockBit ransomware group threatens to leak medical data of cancer patients stolen from Varian Medical Systems. The LockBit ransomware...
Microsoft Patch Tuesday for August 2023 fixed 2 actively exploited flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft Patch Tuesday security updates for August 2023 addressed 74 vulnerabilities, including two actively exploited flaws. Microsoft Patch Tuesday security...
UK Electoral Commission discloses a data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The UK Electoral Commission suffered a data breach that exposed voters’ personal information between 2014 and 2022. The UK Electoral...
Sweet Security Emerges From Stealth With $12 Million Seed Funding and a Cloud Runtime Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Israeli startup Sweet Security has emerged from stealth, launched a Cloud Runtime Security Suite, and announced a $12 million seed...
Microsoft Paid Out $13 Million via Bug Bounty Programs for Fourth Consecutive Year – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs For the fourth consecutive year, Microsoft has announced paying out more than $13 million through its bug bounty programs. The...