Source: www.cybertalk.org – Author: slandau By Zac Amos, Features Editor, Rehack.com Supply chain cyber attacks are on the rise, and industry professionals must work to protect their...
Day: August 4, 2023
Mastering shadow AI: Your guide to gaining control – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: For many organizations, artificial intelligence has become a critical tool. A staggering 37% of companies are currently using AI...
Black Hat Fireside Chat: Easy come, easy go access strengthens ‘Identity Threat Detection & Response’ – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido The rise of the remote workforce, post Covid-19, did nothing to make the already difficult task of...
News Alert: Vaultree partners with Tableau to uniquely blend encryption, data visualization – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Francisco and Cork, Ireland, Aug. 3, 2023 — Vaultree, a cybersecurity leader pioneering Fully Functional Data-In-Use Encryption (FFDUE), today announces...
Microsoft Warns of Growing Cyber-Threats to Sporting Events – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by Sporting events and venues are increasingly vulnerable to cyber-attacks, a new study from Microsoft has found. The Microsoft Threat...
Credentials Account For Over Half of Cloud Compromises – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over half (55%) of public cloud compromises investigated by Google in the first three months of the year were down to...
Legacy Flaws Dominate Top 12 Vulnerabilities List – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security agencies from the Five Eyes intelligence alliance yesterday released their list of the 12 most exploited vulnerabilities of 2022, highlighting...
UK Government: Cyber-Attacks Could Kill or Maim Thousands – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The government has warned that a serious cyber-attack on UK critical infrastructure has a 5–25% chance of happening over the coming...
Qualys Announces First-Party Software Risk Management Solution – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 FOSTER CITY, Calif., Aug. 3, 2023 /PRNewswire/ — Qualys, Inc. (NASDAQ: QLYS), a provider of disruptive cloud-based IT, security and compliance solutions, today announced it is...
Mission Secure, Idaho National Laboratory Announce Partnership to Protect Critical Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 CHARLOTTESVILLE, Va., Aug. 3, 2023 /PRNewswire/ — Mission Secure announced today that it has partnered with Idaho National Laboratory, a U.S. Department of Energy national...
Center for Cyber Safety and Education Awards $174K in Cybersecurity Scholarships – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ALEXANDRIA, Va., Aug. 3, 2023 /PRNewswire/ — The Center for Cyber Safety and Education, the charitable foundation of nonprofit membership association (ISC)², has announced the...
Hacktivist Group ‘Mysterious Team Bangladesh’ Goes on DDoS Rampage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A gang of hacktivists driven by religious and political motives has emerged as a prodigious new threat,...
Cult of the Dead Cow Hacktivists Give Life to ‘Privacy-First’ App Framework – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading One of the longest-running US hacktivist groups, the “Cult of the Dead Cow” (which goes by cDc),...
World Cup Glory Looms, and So Do Cyber Threats, Microsoft Warns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading As the 2023 FIFA Women’s World Cup enters the knockout stages of the tournament, Microsoft, which...
Exclusive: CISA Sounds the Alarm on UEFI Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Against the backdrop of the debacle that mitigating the BlackLotus bootkit has become, the Cybersecurity and Infrastructure...
As Artificial Intelligence Accelerates, Cybercrime Innovates – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dr. Sean Costigan, Director of Cyber Policy, Red Sift Cybercrime might be the world’s fastest-growing entrepreneurial venture. Over the past decade, no...
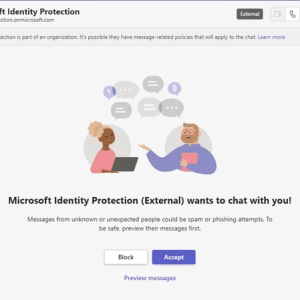
Russia’s ‘Midnight Blizzard’ Hackers Launch Flurry of Microsoft Teams Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The Russian state-sponsored hackers behind the SolarWinds attacks are back again, now using the Microsoft...
CISA, FBI, and NSA published the list of 12 most exploited vulnerabilities of 2022 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA, the FBI, and NSA, along with Five Eyes cybersecurity agencies published a list of the 12 most exploited vulnerabilities...
Decommissioned medical infusion pumps sold on secondary market could reveal Wi-Fi configuration settings – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn that decommissioned medical infusion pumps sold via the secondary market could expose Wi-Fi configuration settings. The sale of...
OWASP Top 10 for LLM (Large Language Model) applications is out! – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The OWASP Top 10 for LLM (Large Language Model) Applications version 1.0 is out, it focuses on the potential security risks...
Rapid7 found a bypass for the recently patched actively exploited Ivanti EPMM bug – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered a bypass for a recently fixed actively exploited vulnerability in Ivanti Endpoint Manager Mobile (EPMM). Rapid7 cybersecurity researchers...
Russian APT29 conducts phishing attacks through Microsoft Teams – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked APT29 group targeted dozens of organizations and government agencies worldwide with Microsoft Teams phishing attacks. Microsoft Threat Intelligence reported...
Malicious npm Packages Found Exfiltrating Sensitive Data from Developers – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered a new bunch of malicious packages on the npm package registry that are designed to exfiltrate sensitive...
Major Cybersecurity Agencies Collaborate to Unveil 2022’s Most Exploited Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 04, 2023THNSoftware Security / Cyber Theat A four-year-old critical security flaw impacting Fortinet FortiOS SSL has emerged as one of...
Could C2PA Cryptography be the Key to Fighting AI-Driven Misinformation? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Adobe, Arm, Intel, Microsoft and Truepic put their weight behind C2PA, an alternative to watermarking AI-generated content. Image: Sascha/Adobe Stock...
Cybersecurity: How Can Companies Benefit From FBI and Homeland Security Collaboration? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ray Fernandez Image: nicescene/Adobe Stock The latest cybercrime studies confirm that attacks are once again at an all-time high. But as ransomware...
Arc Browser Review (2023): Pricing, Features, Alternatives and More – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ray Fernandez Arc browser: Fast facts Key features: User-centered, highly customizable design, rich in features, integrates apps with web browsing to create...
Cisco Announces General Availability of XDR Platform – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg In alliance with Cohesity and others, Cisco is fueling near-zero latency between ransomware detection and remediation with its Extended Detection...
How Malicious Android Apps Slip Into Disguise – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Researchers say mobile malware purveyors have been abusing a bug in the Google Android platform that lets them sneak malicious code...
New Microsoft Azure AD CTS feature can be abused for lateral movement – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Microsoft’s new Azure Active Directory Cross-Tenant Synchronization (CTS) feature, introduced in June 2023, has created a new potential attack surface...