Source: www.govinfosecurity.com – Author: 1 Cloud Security , Security Operations Amit Yoran Says Microsoft Left Critical Azure Vulnerability Unpatched for 4 Months Michael Novinson (MichaelNovinson) •...
Day: August 2, 2023
Why Open Source License Management Matters – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Application Security & Online Fraud , Fraud Management & Cybercrime Adam Murray • August 1, 2023 The ongoing rise...
What You Should Know About Open Source License Compliance for M&A Activity – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Application Security & Online Fraud , Fraud Management & Cybercrime Sam Quakenbush • August 1, 2023 Companies are increasingly...
Malware Campaign Targets Eastern European Air-Gapped Systems – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Operational Technology (OT) Kaspersky Identifies Campign From Beijing-aligned APT31 Threat Actor Prajeet Nair (@prajeetspeaks) • August...
Expel: Firms Still Threatened by Old Vulnerabilities – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Video , Vulnerability Assessment & Penetration Testing (VA/PT) Solution Architecture Director Andrew Hoyt Shares Expel’s Q1...
Privacy Watchdog Slams Sharing of Patient Data Via WhatsApp – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 General Data Protection Regulation (GDPR) , Healthcare , Industry Specific Shadow IT Incident: Health Staff Shared Images and Video Using Unauthorized...
Shield and Visibility Solutions Target Phishing From Inside the Browser – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Menlo Security has introduced two anti-phishing solutions that tackle the problem from within the browser; that is, by analyzing what...
New hVNC macOS Malware Advertised on Hacker Forum – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A new Hidden Virtual Network Computing (hVNC) malware targeting macOS devices is being advertised on a prominent cybercrime forum, Israeli...
Cyble Raises $24 Million for AI-Powered Threat Intelligence Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat intelligence firm Cyble has raised $24 million in a Series B funding round that brings the total invested in...
Firefox 116 Patches High-Severity Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Mozilla on Tuesday announced the release of Firefox 116, Firefox ESR 115.1, and Firefox ESR 102.14, which include patches for...
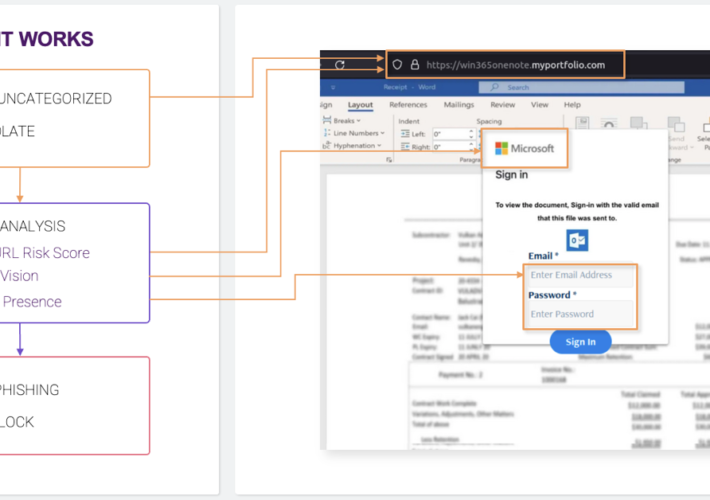
Google AMP Abused in Phishing Attacks Aimed at Enterprise Users – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat actors have been observed abusing Google Accelerated Mobile Pages (AMP) in phishing campaigns, as a new tactic to evade...
Ivanti Zero-Day Exploited by APT Since at Least April in Norwegian Government Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The recently patched zero-day vulnerability affecting Ivanti’s Endpoint Manager Mobile (EPMM) product has been exploited by an advanced persistent threat...
BeyondTrust’s Identity Security Insights Provides Unprecedented Visibility into Identity Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Atlanta, GA – August 2, 2023 – BeyondTrust, the worldwide leader in intelligent identity and access security, today announced the general availability...
Guardio Uncovers Zero-Day Vulnerability in Salesforce’s Email Services – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Tel Aviv, Israel – August 2, 2023 – Guardio, a cybersecurity company leveraging cutting-edge machine learning and proprietary algorithms to deliver top-tier security...
Tanium Selected by DHS CISA to Join the Joint Cyber Defense Collaborative – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 KIRKLAND, Wash.–(BUSINESS WIRE) — Tanium, the industry’s only provider of Converged Endpoint Management (XEM), today announced it has been selected by the...
SynSaber and ICS Advisory Project Identify Vulnerability Trends Within The Critical Infrastructure Sector – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 CHANDLER, Ariz., Aug. 2, 2023 /PRNewswire/ — SynSaber, an industrial asset and network monitoring company dedicated to protecting OT and IT systems and defending...
Global Optical Sensor Market to Reach $45.56B by 2030, Rising Demand in Consumer Electronics and IoT Applications – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 This report on global optical sensor market report provides holistic understanding of the market along with market sizing, forecast, drivers, challenges,...
New SEC Rules around Cybersecurity Incident Disclosures – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The US Securities and Exchange Commission adopted final rules around the disclosure of cybersecurity incidents. There are two basic rules:...
VALIC Retirement Services Company Experiences PBI Data Breach Exposing Approximately 798,000 Social Security Numbers – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 MARLTON, N.J., Aug. 1, 2023 /PRNewswire/ — An estimated 798,000 consumers are being notified that their Social Security numbers and other confidential information were...
Instagram Flags AI-Generated Content – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Instagram appears to be implementing a feature that would label social media posts created by ChatGPT and...
Iranian Company Plays Host to Reams of Ransomware, APT Groups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Cloudzy, purportedly an American company though one with deep roots in Iran, is alleged to be...
Iran’s APT34 Hits UAE With Supply Chain Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading The Iran-linked advanced persistent threat known as APT34 is at it again, this time mounting a supply chain...
Eyes on IDOR Vulnerabilities! US and Australia Release Joint Advisory – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Cybersecurity agencies in Australia and the U.S. issued an advisory that warns about security flaws in web applications that could...
Staff at NHS Lanarkshire Exposed Patient`s Data on Unauthorized WhatsApp Group – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși The Information Commissioner’s Office (ICO) revealed that 26 staff members of NHS Lanarkshire shared patients` information on a WhatsApp group....
Hot Topic Announces Potential Data Breach Due to Stolen Account Credentials – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși The American clothing company Hot Topic announced they identified suspicious login activity on a series of Reword accounts. Hot Topic...
New SEC Regulations: US Businesses Must Report Cyberattacks within 4 Days – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici The U.S. Securities and Exchange Commission (SEC) has approved new rules requiring publicly traded companies to disclose cyberattack details within...
8 Best CrowdStrike Competitors & Alternatives in 2023 [Features, Pricing & Reviews] – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Adelina Deaconu Due to the constantly changing nature of cyber threats, businesses must implement strong security solutions. Here is where CrowdStrike competitors...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
























![8-best-crowdstrike-competitors-&-alternatives-in-2023-[features,-pricing-&-reviews]-–-source:-heimdalsecurity.com](https://ciso2ciso.com/wp-content/uploads/2023/08/72007/8-best-crowdstrike-competitors-alternatives-in-2023-features-pricing-reviews-source-heimdalsecurity-com-710x360.png)