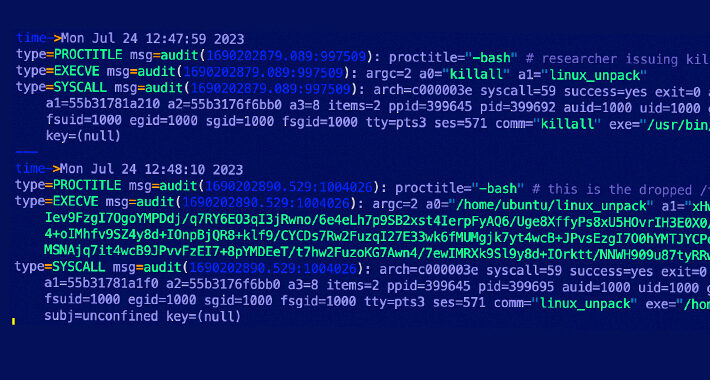
Source: thehackernews.com – Author: . Jul 31, 2023THNCyber Threat / Botnet The P2PInfect peer-to-peer (P2) worm has been observed employing previously undocumented initial access methods to...
Day: August 1, 2023
BAZAN Group, Israel’s Largest Oil Refinery, Had Its Website Hit by a DDoS Attack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The BAZAN Group’s website is inaccessible since this weekend due to a DDoS attack. The Iranian hacktivist group, “Cyber Avengers”...
Locky Ransomware 101: Everything You Need to Know – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Josefine Lödby In the fast-evolving landscape of cybersecurity threats, ransomware has consistently remained a top concern for individuals and organizations. Among the...
ARIA Cybersecurity Brings Real-Time AI to OT Platforms – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard ARIA Cybersecurity Solutions, an arm of CSPi, has launched a platform that applies artificial intelligence (AI) in memory directly on...
Insights from a Leading API Security Vendor: Understanding the Joint Cybersecurity Advisory on IDOR Vulnerabilities by ACSC, CISA, and NSA – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jason Kent The Australian Signals Directorate’s Australian Cyber Security Centre (ACSC), U.S. Cybersecurity and Infrastructure Security Agency (CISA), and U.S. National Security...
BSides Leeds 2023 – Andy Gill – Pentests: The Jason Bourne Approach Turning Regular Biros Into Weapons – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
How Generative AI Will Transform Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Peter Klimek One of the most promising developments in the fight against cybersecurity threats is the use of artificial intelligence (AI). This...
Randall Munroe’s XKCD ‘Daytime Firefly’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Must-See Sessions at the Black Hat USA 2023 Conference – Source: securityboulevard.com
Source: securityboulevard.com – Author: Esther Shein Premier cybersecurity conference Black Hat USA 2023 is coming up in a few weeks, making this a good time to...
The Product Pulse – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalie Anderson Monthly Release Notes for July Looking to learn about Apptega’s latest and greatest product updates? Well, you’re in the right...
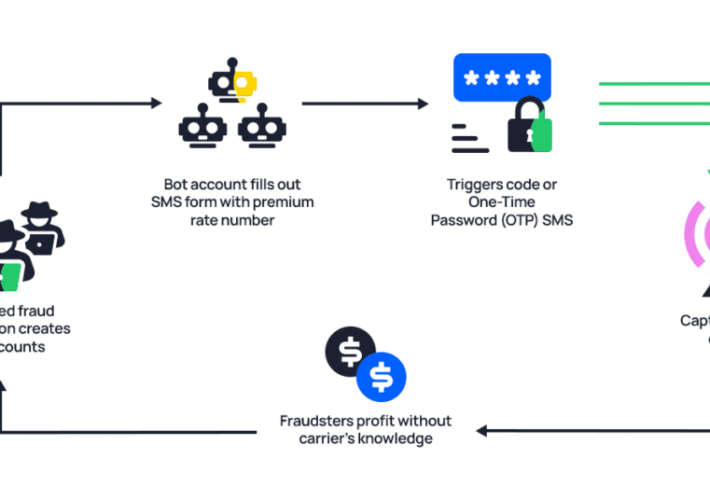
SMS Fraud Takes A Toll: The Evolving Threat of SMS Pumping and Toll Fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexa Bleecker SMS has become a popular channel to engage customers, verify identities, and offer promotions. Unfortunately, this growing reliance on SMS...
BSides Leeds 2023 – Ayoub Safa – Uncommon And Advanced Techniques For Account Takeover Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Podcast Episode 2: Summer Phishing Season is Hot, but so is DEFCON – Source: securityboulevard.com
Source: securityboulevard.com – Author: Assura Team Ever wondered how safe your digital life really is? Prepare to open your eyes to the unseen dangers lurking in...
New Malware WikiLoader Targeting Italian Organizations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Campaign Uses Malicious Microsoft Office Attachments Prajeet Nair (@prajeetspeaks) • July 31, 2023 ...
What Causes a Rise or Fall in Fresh Zero-Day Exploits? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Google Report Lauds Transparency and Researchers, Warns Against Incomplete Fixes Mathew J. Schwartz (euroinfosec)...
AMTD: The Final Layer of Defense – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 As the security stack evolved from antivirus to next-generation antivirus to endpoint protection, endpoint detection and response, and extended detection and...
How AI-Driven Identity Security Can Enable Clinician Autonomy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare entities are “stressed,” in the words of SailPoint’s Rob Sebaugh, and identity security has paid a steep toll. But modernization,...
Ukraine Cracks Down on Illicit Financing Network – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cryptocurrency Fraud , Fraud Management & Cybercrime Network Converted Russian Rubles Into Ukrainian Hryvnia Via Cryptocurrency Mihir Bagwe (MihirBagwe) • July...
Live Webinar | Modernizing your Identity Governance Program – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Bill Willis Field CTO, IDMWORKS A leading thinker in the areas of Security, Compliance, Cryptography, Biometrics, Credentialing, and Identity Management with...
Known MOVEit Attack Victim Count Reaches 545 Organizations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations Allegheny County Advises 1 Million Victims: Don’t Trust Promises to Delete Data Mathew J....
European Governments Targeted in Russian Espionage Campaign – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Russian Foreign Intelligence Service Targets Diplomatic and Foreign Policy Entities Akshaya Asokan...