Source: thehackernews.com – Author: . A nation-state actor with links to China is suspected of being behind a series of attacks against industrial organizations in Eastern...
Day: August 1, 2023
Cybercriminals Renting WikiLoader to Target Italian Organizations with Banking Trojan – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 01, 2023THNCyber Attack / Malware Organizations in Italy are the target of a new phishing campaign that leverages a new...
Reducing Generative AI Hallucinations and Trusting Your Data: Interview With Cognite CPO Moe Tanabian – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse In a conversation with Cognite CPO Moe Tanabian, learn how industrial software can combine human and AI skills to create...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you. – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
ESET Threat Report H1 2023 – Source:
Source: – Author: 1 A view of the H1 2023 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Emotet: sold or on vacation? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Originally a banking trojan, Emotet later evolved into a full-blown botnet and went on to become one of the most dangerous cyberthreats...
What’s up with Emotet? – Source:
Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: – Views:...
Deepfaking it: What to know about deepfake-driven sextortion schemes – Source:
Source: – Author: 1 Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns Original Post...
Verizon 2023 DBIR: What’s new this year and top takeaways for SMBs – Source:
Source: – Author: 1 Here are some of the key insights on the evolving data breach landscape as revealed by Verizon’s analysis of more than 16,000...
Mastering shadow AI: Your guide to gaining control – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: For many organizations, artificial intelligence has become a critical tool. A staggering 37% of companies are currently using AI...
News Alert: Nile raises $175 million in series C funding to deliver network-as-a-service (NaaS) – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Jose, Calif. – Aug.1, 2023 – Nile the leader in next-generation enterprise networks, today announced a $175 million Series C...
Protecting Intellectual Property When It Needs to Be Shared – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer Protecting intellectual property (IP) when it is on the corporate network or in the cloud is difficult enough...
China’s Volt Typhoon APT Burrows Deeper Into US Critical Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The US military was reckoning with two major cyber concerns over the weekend — one the...
Air-Gapped ICS Systems Targeted by Sophisticated Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Security teams in industrial control systems (ICS) environments are fighting a worm that gets past air-gapped defenses. Researchers...
Abyss Locker Ransomware Looks to Drown VMware’s ESXi Servers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The Abyss Locker ransomware gang is now a threat to industrial control systems (ICS), enterprises, and public-sector organizations...
New WikiLoader Malware Goes to Extreme Lengths to Hide – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have uncovered new loader malware under active development which uses multiple mechanisms to evade detection. Proofpoint said it detected...
Call of Duty Self-Spreading Worm Takes Aim at Player Lobbies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Activision, the video game publisher behind Call of Duty: Modern Warfare II, the popular first-person shooter, has...
Experts discovered a previously undocumented initial access vector used by P2PInfect worm – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cado Security observed a new variant of the P2PInfect worm targets Redis servers with a previously undocumented initial access vector....
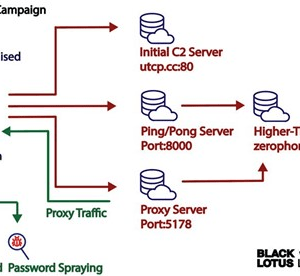
Experts link AVRecon bot to the malware proxy service SocksEscort – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The AVRecon botnet relies on compromised small office/home office (SOHO) routers since at least May 2021. In early July, researchers...
Three flaws in Ninja Forms plugin for WordPress impact 900K sites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of vulnerabilities impacting the Ninja Forms plugin for WordPress that could be exploited for escalating privileges and data...
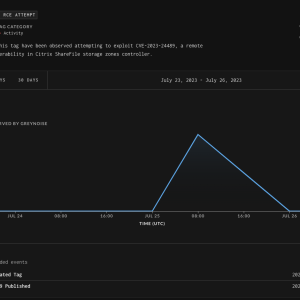
Experts warn attackers started exploiting Citrix ShareFile RCE flaw CVE-2023-24489 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn that threat actors started exploiting Citrix ShareFile RCE vulnerability CVE-2023-24489 in the wild. Citrix ShareFile is a widely...