Source: www.bleepingcomputer.com – Author: Ax Sharma Microsoft Edge web browser has been displaying security warnings after Twitter changed its name to ‘X’. Amid its rapid rebranding...
Month: July 2023
CISA warns of breach risks from IDOR web app vulnerabilities – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA warned today of the significant breach risks linked to insecure direct object reference (IDOR) vulnerabilities impacting web applications in...
New Android malware uses OCR to steal credentials from images – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Two new Android malware families named ‘CherryBlos’ and ‘FakeTrade’ were discovered on Google Play, aiming to steal cryptocurrency credentials and...
Hawai’i Community College pays ransomware gang to prevent data leak – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Hawaiʻi Community College has admitted that it paid a ransom to ransomware actors to prevent the leaking of stolen...
CoinsPaid blames Lazarus hackers for theft of $37,300,000 in crypto – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Estonian crypto-payments service provider CoinsPaid has announced that it experienced a cyber attack on July 22nd, 2023, that resulted in...
IT Ops and Security Teams Need Automation, Not Couples Therapy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ramin Ettehad, Co-Founder, Oomnitza There are a growing set of essential business processes for which security and IT operations teams share accountability....
Why CISOs Should Get Involved With Cyber Insurance Negotiation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer Sometimes being the CISO can be a no-win position. According to a recent survey by human resources and...
Despite Post-Log4j Security Gains, Developers Can Still Improve – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Developers are increasingly adopting security testing as part of the development pipeline, but companies still have...
7 in 10 MSPs Name Data Security and Network Security As Their Top IT Priorities for 2023 – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 FRISCO, Texas, July 27, 2023 /PRNewswire/ — Netwrix, a cybersecurity vendor, today announced additional findings for the MSP sector from its survey of more than...
CompTIA ChannelCon Technology Vendor Fair Highlights Tech Solutions – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 DOWNERS GROVE, Ill., July 27, 2023 /PRNewswire/ — More than 160 product vendors and distributors will be on hand for the Technology Vendor...
Ryanair Hit With Lawsuit Over Use of Facial Recognition Technology – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Ryanair has become the latest organization to face legal action over its use of facial recognition...
Millions of People Affected in MOVEit Attack on US Gov’t Vendor – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The MOVEit breach has claimed yet another target: Maximus Inc., a US government contractor. Though the...
10 Free Purple Team Security Tools to Check Out – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer, Dark Reading Keep up with the latest cybersecurity threats, newly-discovered vulnerabilities, data breach information, and emerging trends. Delivered...
Actively Exploited Apple Zero-Day Affects iPhone Kernel – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Apple has addressed multiple security vulnerabilities in an emergency patch drop, one of which is a zero-day...
A Data Exfiltration Attack Scenario: The Porsche Experience – Source:thehackernews.com
Source: thehackernews.com – Author: . As part of Checkmarx’s mission to help organizations develop and deploy secure software, the Security Research team started looking at the...
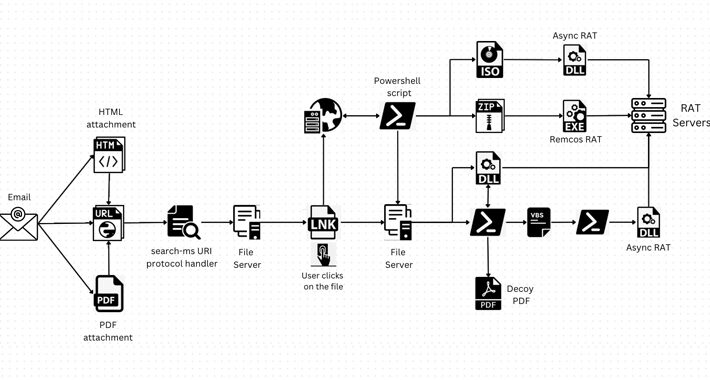
Hackers Abusing Windows Search Feature to Install Remote Access Trojans – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 28, 2023THNMalware / Cyber Threat A legitimate Windows search feature could be exploited by malicious actors to download arbitrary payloads...
BlueBravo Deploys GraphicalProton Backdoor Against European Diplomatic Entities – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 28, 2023THNCyber Espionage / Malware The Russian nation-state actor known as BlueBravo has been observed targeting diplomatic entities throughout Eastern...
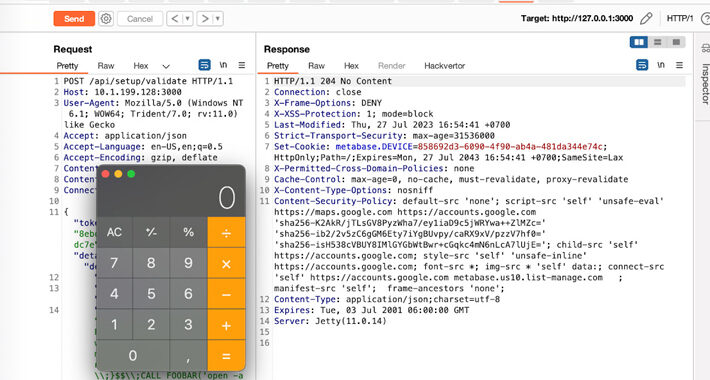
Major Security Flaw Discovered in Metabase BI Software – Urgent Update Required – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 28, 2023THNSoftware Security / Zero Day Users of Metabase, a popular business intelligence and data visualization software package, are being...
Cybersecurity Agencies Warn Against IDOR Bugs Exploited for Data Breaches – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 28, 2023THNSoftware Security / Data Safety Cybersecurity agencies in Australia and the U.S. have published a joint cybersecurity advisory warning...
Fooling an AI Article Writer – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier World of Warcraft players wrote about a fictional game element, “Glorbo,” on a subreddit for the game, trying to entice...
Top strategies: How CISOs can become board-ready – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Corporate boards are actively searching for CISOs who demonstrate technical expertise, but who also possess strong leadership skills, can...
Monoculture: Could this risk affect your organization in a major way? – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Marco Eggerling, Field CISO, EMEA Quick introduction to monocultures As an information security professional, you’ve likely heard the term ‘monoculture’...
News Alert: QBE North America launches new cyber insurance program with Converge – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido New York, NY, July 27, 2023 – QBE North America today announced the launch of a cyber insurance program with new MGA, Converge, acting as...
News Alert: Perception Point reports rates of ‘BEC,’ phishing attacks climb in the first half of 2023 – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel, July 27, 2023 — Perception Point, a leading provider of advanced threat prevention across digital communication channels, today published...
News Alert: CrowdSec report highlights the rise of IPv6 in cyber criminal activities – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Paris, France, July 27, 2023 – CrowdSec, the pioneering open source and collaborative cybersecurity company, today released its Q2 2023 Majority...
News Alert: Protect AI raises $35M in Series A financing to secure AI, ML software supply chain – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Seattle, Wash., July 26, 2023 — Protect AI, the artificial intelligence (AI) and machine learning (ML) security company, today announced it has...
Heart monitor manufacturer hit by cyberattack, takes systems offline – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley CardioComm, a Canadian company which provides heart-monitoring technology to hospitals and consumers, has revealed that it has been forced to...
SEC requires firms to report cyberattacks within 4 days, but not everyone may like it – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley New rules requiring publicly-listed firms to disclose serious cybersecurity incidents within four days have been adopted by the US Securities...
Gathering dust and data: How robotic vacuums can spy on you. – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...