Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Operational Technology (OT) Hackers Could Exploit Inherent Vulnerabilities in OT Systems, Dutch...
Month: July 2023
CISA’s New ‘CyberSentry’ Program to Tighten ICS Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Government Program to Monitor IT, OT Networks of Enrolled Critical Infrastructure Partners...
Lumu, ExtraHop Lead Network Analysis, Visibility: Forrester – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Network Detection & Response , Next-Generation Technologies & Secure Development Arista, Trend Micro Earn High Marks...
DDoSia Attack Tool Evolves with Encryption, Targeting Multiple Sectors – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actors behind the DDoSia attack tool have come up with a new version that incorporates a new mechanism to...
Mexico-Based Hacker Targets Global Banks with Android Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 04, 2023Ravie LakshmananCyber Crime / Mobile Security An e-crime actor of Mexican provenance has been linked to an Android mobile...
Alert: 330,000 FortiGate Firewalls Still Unpatched to CVE-2023-27997 RCE Flaw – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 04, 2023Ravie LakshmananNetwork Security / Exploit No less than 330000 FortiGate firewalls are still unpatched and vulnerable to CVE-2023-27997, a...
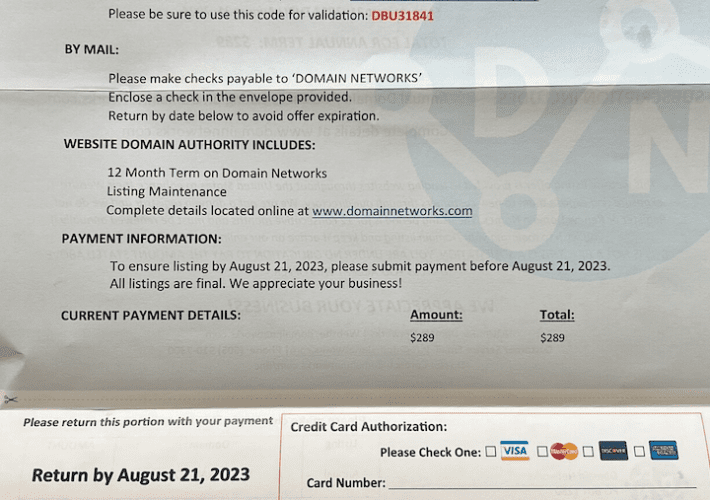
Who’s Behind the DomainNetworks Snail Mail Scam? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs If you’ve ever owned a domain name, the chances are good that at some point you’ve received a snail mail letter...
Weekly Update 354 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I’m in Thailand! It’s spectacular here, and even more so since recording this video and getting out of Bangkok and...
USPTO’s API Flaw Leads to Years-Long Data Leak – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Patent and Trademark Office (USPTO) has recently disclosed a data security incident involving domicile information in certain trademark filings...
Chinese Threat Actors Target Europe in SmugX Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A malicious campaign by Chinese threat actors has been spotted targeting government entities in Europe, specifically focusing on foreign and domestic...
Meduza Stealer Targets Windows Users With Advanced Tactics – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new malware called “The Meduza Stealer” has been observed targeting Windows users with advanced data theft tactics. The Uptycs Threat Research...
VMware, Other Tech Giants Announce Push for Confidential Computing Standards – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire In conjunction with the 2023 Confidential Computing Summit last week, VMware announced a partnership with tech giants to accelerate the...
Apple, Civil Liberty Groups Condemn UK Online Safety Bill – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The latest variant of the crypto wars is happening now, with the UK and EU governments attempting to force backdoors...
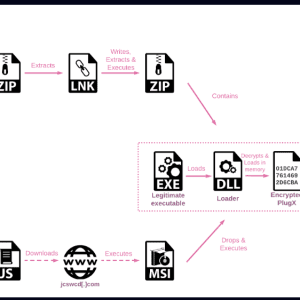
Chinese Hackers Use HTML Smuggling to Infiltrate European Ministries with PlugX – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 03, 2023Ravie LakshmananMalware Attack / Cyberespionage A Chinese nation-state group has been observed targeting Foreign Affairs ministries and embassies in...
Researchers Develop Exploit Code for Critical Fortinet VPN Bug – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Researchers have written exploit code for a critical remote code execution (RCE) vulnerability in Fortinet’s FortiGate...
Russian Satellite Internet Downed via Attackers Claiming Ties to Wagner Group – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Russian satellite Internet provider Dozor-Teleport was knocked offline in the early hours of June 29, dealing a...
Israel Aided UAE in Defending Against DDoS Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Israel earlier this year aided the United Arab Emirates (UAE) in helping repel a major distributed...
SSH Servers Hit in ‘Proxyjacking’ Cyberattacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Threat actors are exploiting vulnerable secure shell protocol (SSH) servers to launch Docker services that take advantage...
Name That Edge Toon: Three-Ring Circus – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist Let’s see you tame this contest beast! Come up with a witty cybersecurity-related caption to explain the scary scene...
A CISO’s Guide to Paying Down Software Supply Chain Security Debt – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Lorenc, Founder & CEO, Chainguard There has always been a tradeoff in IT between shipping new features and functionality versus paying...
Microsoft denies data breach, theft of 30 million customer accounts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Microsoft has denied the claims of the so-called hacktivists “Anonymous Sudan” that they breached the company’s servers and stole credentials...
Hackers target European government entities in SmugX campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A phishing campaign that security researchers named SmugX and attributed to a Chinese threat actor has been targeting embassies and...
Microsoft Edge upgrades built-in Cloudflare VPN with 5GB of data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft’s Edge browser has recently enhanced its ‘Edge Secure Network’ feature, which now offers 5GB of data, significantly increasing from...
300,000+ Fortinet firewalls vulnerable to critical FortiOS RCE bug – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hundreds of thousands of FortiGate firewalls are vulnerable to a critical security issue identified as CVE-2023-27997, almost a month after...
Twitter’s bot spam keeps getting worse — it’s about porn this time – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Forget crypto spam accounts, Twitter’s got another problem which involves bots and accounts promoting adult content and infiltrating Direct Messages and...
Snappy: A tool to detect rogue WiFi access points on open networks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cybersecurity researchers have released a new tool called ‘Snappy’ that can help detect fake or rogue WiFi access points that...
BlackCat ransomware pushes Cobalt Strike via WinSCP search ads – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Bing Create The BlackCat ransomware group (aka ALPHV) is running malvertizing campaigns to lure people into fake pages that...
SmugX: Chinese APT uses HTML smuggling to target European Ministries and embassies – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini China-linked APT group was spotted using HTML smuggling in attacks aimed at Foreign Affairs ministries and embassies in Europe. A...
The Impacts of Data Loss on Your Organization – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini What are the causes of Data Loss and which are their impact on your organization? In today’s digital age, data...
CISA adds Samsung and D-link bugs to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added actively exploited Samsung and D-Link vulnerabilities to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure Security...