Source: – Author: 1 A view of the H1 2023 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Month: July 2023
Emotet: sold or on vacation? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Originally a banking trojan, Emotet later evolved into a full-blown botnet and went on to become one of the most dangerous cyberthreats...
What’s up with Emotet? – Source:
Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: – Views:...
Deepfaking it: What to know about deepfake-driven sextortion schemes – Source:
Source: – Author: 1 Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns Original Post...
Verizon 2023 DBIR: What’s new this year and top takeaways for SMBs – Source:
Source: – Author: 1 Here are some of the key insights on the evolving data breach landscape as revealed by Verizon’s analysis of more than 16,000...
The good, the bad and the ugly of AI – Week in security with Tony Anscombe – Source:
Source: – Author: 1 The growing use of synthetic media and the difficulties in distinguishing between real and fake content raise a slew of legal and...
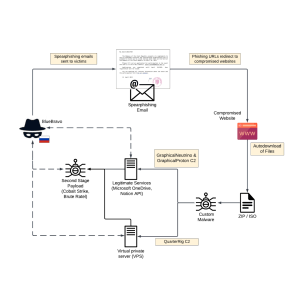
Russian APT BlueBravo targets diplomatic entities with GraphicalProton backdoor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked BlueBravo has been spotted targeting diplomatic entities in Eastern Europe with the GraphicalProton Backdoor. The Russia-linked threat-state actor BlueBravo...
CoinsPaid blames North Korea-linked APT Lazarus for theft of $37M worth of cryptocurrency – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Crypto-payments service provider CoinsPaid suffered a cyber attack that resulted in the theft of $37,200,000 worth of cryptocurrency. CoinsPaid, a...
Monitor Insider Threats but Build Trust First – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The issue of how to prevent insider threats without infringing on employee privacy is one that has been a hot...
GROUP-IB Co-Founder ILYA SACHKOV SENTENCED TO 14 YEARS IN A STRICT PRISON COLONY – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ilya Sachkov, former CEO and co-founder of Group-IB was sentenced to 14 years in a high security prison colony according...
The Business Impact of Infostealers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Keon Ramzani In the last several years, consumer identity protection offers have become nearly ubiquitous. Service providers ranging from credit cards and...
5 Top Data Center Infrastructure Management (DCIM) Trends – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi Data center infrastructure management (DCIM) is the process of monitoring, managing and optimizing the physical and logical components of a...
Nitrogen Campaign Starts with Fake Ads, Ends with Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Threat actors are using bogus advertisements for IT tools on sites like Google and Microsoft’s Bing in hopes of luring...
BSides Leeds 2023 – Kim Hendry – The NSM Ouroboros: Embracing The Endless Cycle Of Network Security Monitoring – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
How to Quantify the ROI of your GRC & Security Programs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tejas Ranade GRC programs are often viewed as cost centers. But, they can in fact be profit drivers by contributing to sales...
What to Expect at STRONGER 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cameron Delfin In an increasingly digitalized world, the significance of cybersecurity cannot be overstated. Cyber threats continue to evolve, posing immense challenges...
Senator Wyden: Microsoft is Responsible for China-Linked Group’s Hack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt US Senator Ron Wyden (D-OR) is asking government enforcement agencies to hold Microsoft responsible for the hack by a Chinese-linked...
Android Foils AirTag Stalkers and Thieves — While Apple Does Nothing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings “Unknown Tracker Detected,” your phone screams. What now? An Apple AirTag that’s not yours—but traveling with you—could be bad news. Perhaps...
Daniel Stori’s ‘The Monolith Retirement’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Cybersecurity Insights with Contrast CISO David Lindner | 7/28 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Insight #1 A recent report by Cohesity sees the top three things being required for cyber insurance...
Lazarus Group Targets Microsoft IIS Servers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering North Korean Group Uses Watering Hole Techniques to Access,...
Every Application Journey Needs a Cybersecurity Platform – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Application Security & Online Fraud , DevSecOps Taking a Cybersecurity Mesh Platform Approach to Securing Applications Vince Hwang,...
700,000 Sensitive Teacher, Student Records Exposed on Web – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Governance & Risk Management , Healthcare Researcher Says Hackers Could Have Seen Salary Info, Child Abuse Reports and...
US and Australia Warn Developers Over IDOR Vulnerabilities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 API Security Flaws That Give Back-End Access to an Object Can Cause Large Breaches, Agencies Say Mihir Bagwe (MihirBagwe) • July...
FBI: Hackers Use AI for Sextortion, Explosives, Bad Websites – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development China Seeks to Level AI Playing Field by Stealing IP...
Lazarus Group Targets Microsoft IIS Servers – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering North Korean Group Uses Watering Hole Techniques to Access,...
Every Application Journey Needs a Cybersecurity Platform – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Application Security , Application Security & Online Fraud , DevSecOps Taking a Cybersecurity Mesh Platform Approach to Securing Applications Vince Hwang,...
700,000 Sensitive Teacher, Student Records Exposed on Web – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Governance & Risk Management , Healthcare Researcher Says Hackers Could Have Seen Salary Info, Child Abuse Reports and...
US and Australia Warn Developers Over IDOR Vulnerabilities – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 API Security Flaws That Give Back-End Access to an Object Can Cause Large Breaches, Agencies Say Mihir Bagwe (MihirBagwe) • July...
FBI: Hackers Use AI for Sextortion, Explosives, Bad Websites – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development China Seeks to Level AI Playing Field by Stealing IP...