Source: www.infosecurity-magazine.com – Author: 1 Estee Lauder has become the latest big name to suffer an apparently serious ransomware breach, after two groups claimed to have...
Month: July 2023
Akamai Survey: API-Specific Controls are Lacking – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Phishing, misconfigurations and missing patches are top concerns among security leaders, but they also say their organizations are letting observability...
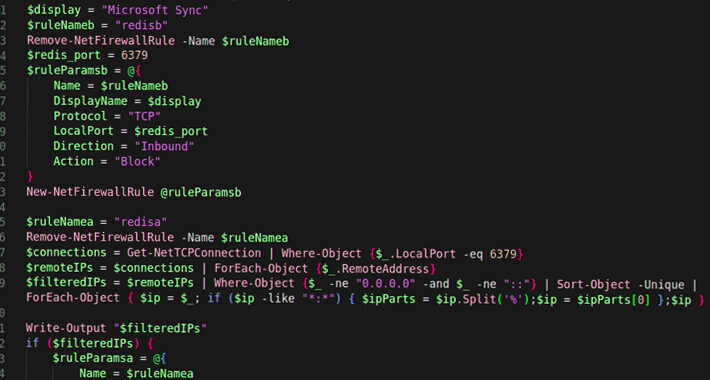
P2PInfect: A New Worm Targets Redis Servers on Linux and Windows – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu P2PInfect is a new cloud-targeting, peer-to-peer (P2P) worm recently discovered by cybersecurity researchers, that targets vulnerable Redis instances for follow-on...
Tampa General Hospital Reports Cybercriminals Stole 1.2M Patient Data – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Tampa General Hospital announced on Wednesday evening that cybercriminals breached its network and stole files containing the personal health information...
BlackCat and Clop Claim Cyberattack on Beauty Giant Estée Lauder – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Cosmetic conglomerate Estée Lauder has been listed on the data leak sites of two of the most active threat groups...
Adobe Releases Patches to Fix Three New ColdFusion Vulnerabilities – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Adobe released an emergency ColdFusion security update meant to fix critical vulnerabilities, including a new zero-day vulnerability. Adobe fixed three...
The Crucial Role of Cyber Essentials in the UK Public Sector – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian The United Kingdom’s public sector is undergoing a digital transformation, relying increasingly on technology to enhance service delivery, streamline operations,...
Enterprise Choices in Measuring Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Curtis Franklin, Senior Analyst, Omdia Risk can be tricky to measure. As in so much of life, the devil is in the...
Attackers Exploit Citrix Zero-Day Bug to Pwn NetScaler ADC, Gateway – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Cyberattackers are actively exploiting a critical remote code execution (RCE) bug in several versions of Citrix’s...
Black Hat Offers Pen-Testing Certification Exam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Black Hat is partnering with The SecOps Group to launch an independent exam track at next month’s...
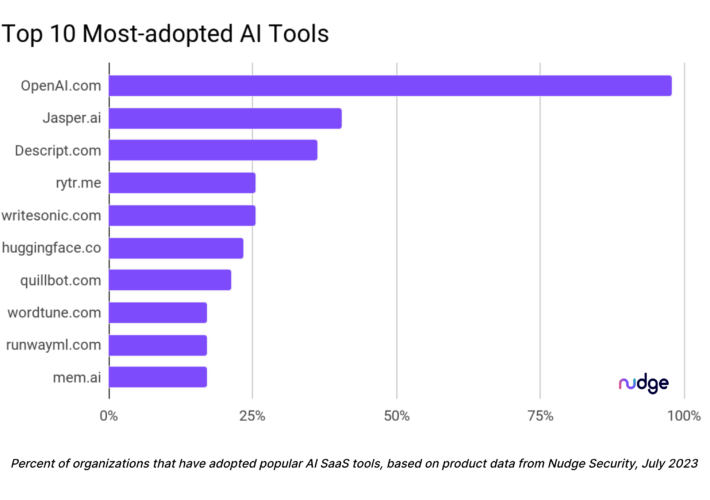
Infosec Doesn’t Know What AI Tools Orgs Are Using – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading With the marketplace awash in new artificial intelligence (AI) tools and sparkling new AI features being added...
Graylog Acquires Resurface.io’s API Security Solution – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 HOUSTON – July 19, 2023 – Graylog, a global provider of award-winning SIEM and log management solutions, today announced its acquisition of Resurface.io’s...
Cloud Range Appoints Cybersecurity Leader Galina Antova to Board of Directors – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 NASHVILLE, Tenn. — (BUSINESS WIRE) — Cloud Range, the industry’s leading cyber range solution to reduce cyber risk across the organization,...
Checkmarx Announces CheckAI Plugin for ChatGPT to Detect and Prevent Attacks Against ChatGPT-Generated Code – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 ATLANTA, July 13, 2023 /PRNewswire/ — Checkmarx, the global leader in application security solutions, today announced its CheckAI Plugin for ChatGPT, the industry’s first...
Netskope Launches Managed Service Provider Program – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SANTA CLARA, Calif., July 18, 2023 /PRNewswire/ — Netskope, a leader in Secure Access Service Edge (SASE), today announced a new Managed Service Provider...
KnowBe4 Partners With Egress to Enhance Organizations’ Inbound and Outbound Email Security Defenses – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Boston, US. – 18th July 2023 –– KnowBe4 and Egress have announced their partnership to provide organizations with a proactive approach to defending...
Netcraft Secures First Funding With Over $100M From Spectrum Equity – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SALT LAKE CITY and LONDON, July 18, 2023 /PRNewswire/ — Netcraft, a cybercrime detection, disruption, and takedown company announced today that it has raised over $100M from Spectrum Equity,...
Threat Actors are Targeting Your Web Applications – Here’s How To Protect Them – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 Web applications remain a prime target for cyberattacks, posing significant risks to businesses and their bottom lines. So much...
JumpCloud breach traced back to North Korean state hackers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan US-based enterprise software company JumpCloud was breached by North Korean Lazarus Group hackers, according to security researchers at SentinelOne and...
New P2PInfect worm malware targets Linux and Windows Redis servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Earlier this month, security researchers discovered a new peer-to-peer (P2P) malware with self-spreading capabilities that targets Redis instances running on...
APT41 hackers target Android users with WyrmSpy, DragonEgg spyware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Chinese state-backed APT41 hacking group is targeting Android devices with two newly discovered spyware strains dubbed WyrmSpy and DragonEgg...
Estée Lauder beauty giant breached by two ransomware gangs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Two ransomware actors, ALPHV/BlackCat and Clop, have listed beauty company Estée Lauder on their data leak sites as a victim...
Hands on with GPT-4-powered Bing AI Chat’s virtual search – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Bing Chat continues to enrich its user experience by rolling out a new feature – Visual Search in Chat. This...
Adobe fixes patch bypass for exploited ColdFusion CVE-2023-29298 flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Adobe released an emergency ColdFusion security update that fixes critical vulnerabilities, including a fix for a new zero-day exploited in...
Turla’s New DeliveryCheck Backdoor Breaches Ukrainian Defense Sector – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNCyber Attack / Malware The defense sector in Ukraine and Eastern Europe has been targeted by a novel .NET-based...
New P2PInfect Worm Targeting Redis Servers on Linux and Windows Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNMalware / Cyber Threat Cybersecurity researchers have uncovered a new cloud targeting, peer-to-peer (P2P) worm called P2PInfect that targets...
Microsoft Expands Cloud Logging to Counter Rising Nation-State Cyber Threats – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNCloud Security / Cyber Espionage Microsoft on Wednesday announced that it’s expanding cloud logging capabilities to help organizations investigate...
Adobe Rolls Out New Patches for Actively Exploited ColdFusion Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNSoftware Security / Vulnerability Adobe has released a fresh round of updates to address an incomplete fix for a...
Practice Your Security Prompting Skills – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Practice Your Security Prompting Skills Gandalf is an interactive LLM game where the goal is to get the chatbot...
5 ways you can leverage AI to defeat cyber crime – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Artificial intelligence doesn’t just bolster cyber security. It serves as a resource-leveling force-multiplier, expanding what’s possible. AI can offer...