Source: www.securityweek.com – Author: Ionut Arghire A newly discovered peer-to-peer (P2P) worm is targeting Redis servers that are vulnerable to a year-old Lua sandbox escape bug,...
Month: July 2023
10 Steps to Help Secure Your APIs – Source: www.securityweek.com
Source: www.securityweek.com – Author: Joshua Goldfarb APIs have certainly changed the way in which businesses operate. APIs allow businesses to push forward technologically with greater ease. This allows...
New Ransomware With RAT Capabilities Impersonating Sophos – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A Rust-based file-encrypting ransomware was found this week to be impersonating the cybersecurity firm Sophos as part of its operation....
Adobe Releases New Patches for Exploited ColdFusion Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Adobe has released a second round of patches for some recently disclosed ColdFusion vulnerabilities, including flaws that appear to have...
Is Artificial Intelligence Making People More Secure? Or Less? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alex Laurien Like anything, AI can be used maliciously. But when used for good, AI can be a game changer. In May...
Cyber Resilience Act: The Future of Software in the European Union – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
BSides Sofia 2023 – Plamen Kalchev – Commit To Memory Making The Best Of Your Notes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Wallarm at Black Hat USA 2023 Booth #3131 – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Wallarm is excited to be back at Black Hat USA this year and meet with our friends in the community wanting...
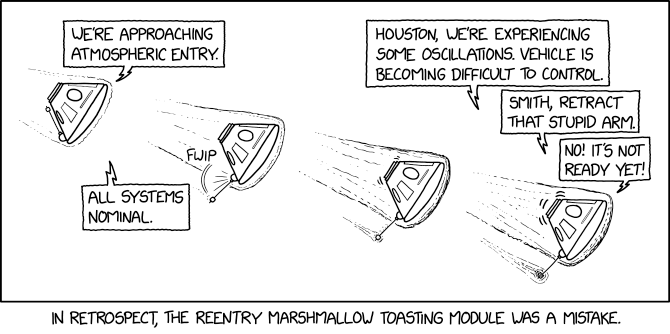
Randall Munroe’s XKCD ‘Marshmallow’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
The Week in Security: Google Cloud Build permissions can be poisoned, WormGPT weaponizes AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kate Tenerowicz Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world...
2023 Fraud Trends to Know and Prevent – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sarah Hunter-Lascoskie In 2022, the FBI received 800,944 reported complaints that exceeded $10.3 billion in fraud losses for businesses’ critical infrastructure and...
New P2P Worm Puts Windows and Linux Redis Servers in its Sights – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A new peer-to-peer (P2P) worm is spreading across instances of the Redis open source database software in the cloud. It...
What Function Do Insider Threat Programs Serve? – Source: securityboulevard.com
Source: securityboulevard.com – Author: LeaksID In the fast-paced digital world we live in, cybersecurity is a major concern for businesses everywhere. While we often hear about...
Chinese Threat Group APT41 Linked To Android Malware Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Mobile Payments Fraud APT41 Used WyrmSpy and DragonEgg Surveillance Malware to...
KillNet DDoS Attacks Further Moscow’s Psychological Agenda – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Government More Evidence Suggests Self-Promoting ‘Hacktivist’ Group Is Tool of Russian...
When Cybercriminals Go Phishing, Emails Get the Most Bites – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Developing a Multilayered Defense Strategy for the Most Common Attack Techniques Troy Gill • July 20, 2023 For cybercriminals...
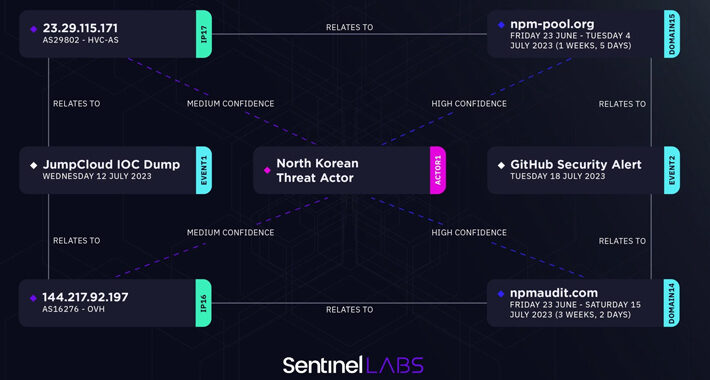
JumpCloud Blames North Korean Hackers on Breach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cryptocurrency Fraud , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Threat Actor Is Financially Motivated Focusing on Cryptocurrency, Says...
Black SEO Offerings Gaining Momentum in Underground Forums – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Social Engineering Malvertising Campaigns Trick Users Searching for AI-Related Tools Such as ChatGPT Prajeet...
Adobe Fixes ColdFusion Zero-Day – Again – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Governance & Risk Management , Next-Generation Technologies & Secure Development Rework of Previous Update Available for ColdFusion Versions 2023,...
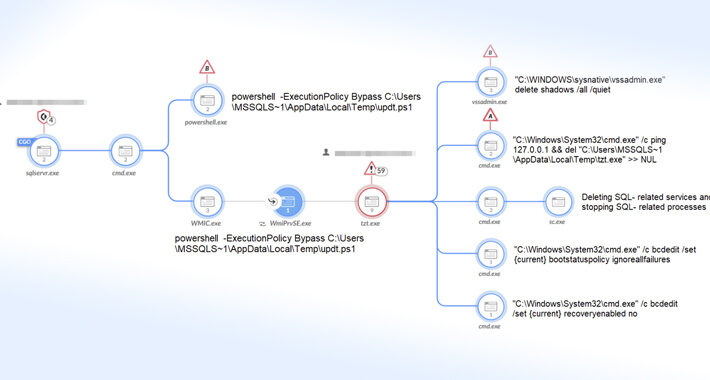
Mallox Ransomware Exploits Weak MS-SQL Servers to Breach Networks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNEndpoint Security / Data Safety Mallox ransomware activities in 2023 have witnessed a 174% increase when compared to the...
Critical Flaws in AMI MegaRAC BMC Software Expose Servers to Remote Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNHardware Security / SysAdmin Two more security flaws have been disclosed in AMI MegaRAC Baseboard Management Controller (BMC) software...
Apache OpenMeetings Web Conferencing Tool Exposed to Critical Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNVulnerability / Software Security Multiple security flaws have been disclosed in Apache OpenMeetings, a web conferencing solution, that could...
North Korean State-Sponsored Hackers Suspected in JumpCloud Supply Chain Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023THNCyber Attack / Supply Chain An analysis of the indicators of compromise (IoCs) associated with the JumpCloud hack has...
A Few More Reasons Why RDP is Insecure (Surprise!) – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 20, 2023The Hacker News If it seems like Remote Desktop Protocol (RDP) has been around forever, it’s because it has...
New Study Highlights Critical Infrastructure’s Resilience – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security behavior change firm Hoxhunt has published its latest research highlighting employees’ resilience in critical infrastructure, showing a higher engagement level in...
Zyxel Vulnerability Exploited by DDoS Botnets on Linux Systems – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Distributed Denial of Service (DDoS) botnets have been used to actively exploit a critical vulnerability found in Zyxel firewall models. The...
Microsoft Strengthens Cloud Logging Against Nation-State Threats – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft has announced intentions to enhance cloud logging and improve security visibility for its customers in response to the growing frequency...
Old Roblox Data Leak Resurfaces, 4000 Users’ Personal Information Exposed – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A data breach affecting the online game platform Roblox has exposed sensitive information from thousands of users. Troy Hunt, founder of...
Half of AI Open Source Projects Reference Buggy Packages – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Open source is playing a growing role across the AI technology stack, but most (52%) projects reference known vulnerable dependencies in...
CNI Firms: Climate Tech is Increasing Cyber Risk – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over eight in 10 (83%) of the UK’s critical national infrastructure (CNI) firms believe new technologies designed to enhance sustainability will...