Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Day: July 30, 2023
Gathering dust and data: How robotic vacuums can spy on you. – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
ESET Threat Report H1 2023 – Source:
Source: – Author: 1 A view of the H1 2023 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Emotet: sold or on vacation? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Originally a banking trojan, Emotet later evolved into a full-blown botnet and went on to become one of the most dangerous cyberthreats...
What’s up with Emotet? – Source:
Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: – Views:...
Deepfaking it: What to know about deepfake-driven sextortion schemes – Source:
Source: – Author: 1 Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns Original Post...
Verizon 2023 DBIR: What’s new this year and top takeaways for SMBs – Source:
Source: – Author: 1 Here are some of the key insights on the evolving data breach landscape as revealed by Verizon’s analysis of more than 16,000...
Linux version of Abyss Locker ransomware targets VMware ESXi servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The Abyss Locker operation is the latest to develop a Linux encryptor to target VMware’s ESXi virtual machines platform in...
Browser developers push back on Google’s “web DRM” WEI API – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google’s plans to introduce the Web Environment Integrity (WEI) API on Chrome has been met with fierce backlash from internet...
CISA warns about SUBMARINE Backdoor employed in Barracuda ESG attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warns of threat actors deploying the SUBMARINE Backdoor in Barracuda ESG attacks....
Now Abyss Locker also targets VMware ESXi servers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A Linux variant of the Abyss Locker designed to target VMware ESXi servers appeared in the threat landscape, experts warn....
BSides Leeds 2023 – Janette Bonar Law – Hackanory: The Power Of Stories – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
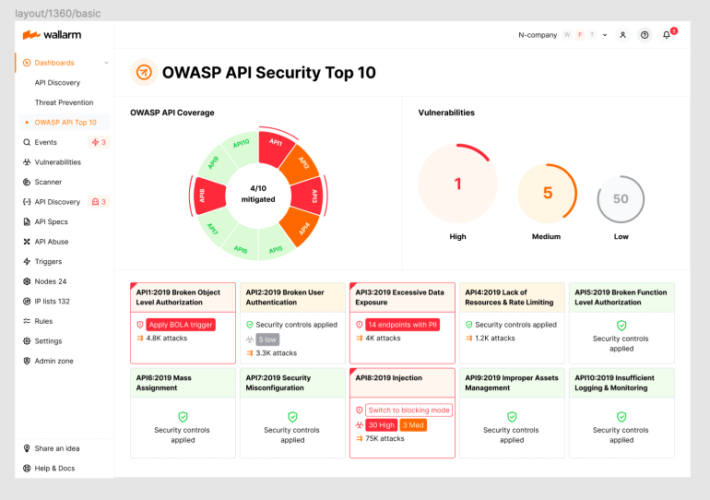
2023 OWASP Top-10 Series: API1:2023 Broken Object Level Authorization – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Welcome to the 2nd post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...
Ivanti Says Second Zero Day Used in Norway Govt Breach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Cybercrime , Fraud Management & Cybercrime Exploitation No Longer Requires Admin Authentication When Chained with Earlier...
N Korean Hackers Phishing With US Army Job Lures – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Anti-Phishing, DMARC , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Researchers Say APT37 Group Likely Behind Campaign Targeting South...
Ivanti Says Second Zero Day Used in Norway Govt Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Cybercrime , Fraud Management & Cybercrime Exploitation No Longer Requires Admin Authentication When Chained with Earlier...
N Korean Hackers Phishing With US Army Job Lures – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Anti-Phishing, DMARC , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Researchers Say APT37 Group Likely Behind Campaign Targeting South...