Source: www.infosecurity-magazine.com – Author: 1 Nominations are open for the eighth annual Security Serious Unsung Heroes Awards to be held in London and run by Eskenzi PR. The...
Day: July 29, 2023
New Android Malware CherryBlos Utilizing OCR to Steal Sensitive Data – Source:thehackernews.com
Source: thehackernews.com – Author: . A new Android malware strain called CherryBlos has been observed making use of optical character recognition (OCR) techniques to gather sensitive...
RFP Template for Browser Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 29, 2023The Hacker NewsBrowser Security / Data Security Increasing cyber threats and attacks have made protecting organizational data a paramount...
Apple Sets New Rules for Developers to Prevent Fingerprinting and Data Misuse – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 29, 2023THNData Security / Privacy Apple has announced plans to require developers to submit reasons to use certain APIs in...
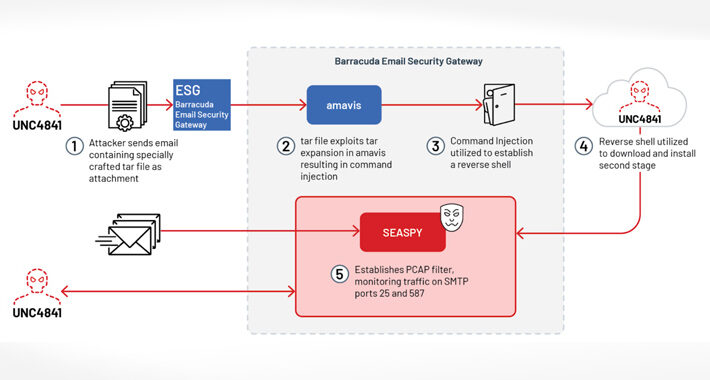
Hackers Deploy “SUBMARINE” Backdoor in Barracuda Email Security Gateway Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 29, 2023THNEmail Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday disclosed details of a “novel...
Ivanti Warns of Another Endpoint Manager Mobile Vulnerability Under Active Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 29, 2023THNVulnerability / Enterprise Security Ivanti has disclosed yet another security flaw impacting Endpoint Manager Mobile (EPMM), formerly known as...
Apple rejects new name ‘X’ for Twitter iOS app because… rules – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Mr. Musk may have successfully pushed Twitter’s new name and logo, ‘X’, and even made the vanity domain x.com redirect to...
CISA: New Submarine malware found on hacked Barracuda ESG appliances – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA says new malware known as Submarine was used to backdoor Barracuda ESG (Email Security Gateway) appliances on federal agencies’...
Apple says new App Store API rules will limit user fingerprinting – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Starting this fall, Apple has announced that developers will be required to provide a reason for using certain APIs that...
The Week in Ransomware – July 28th 2023 – New extortion tactics – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams With ransom payments declining, ransomware gangs are evolving their extortion tactics to utilize new methods to pressure victims. This was...
Ivanti patches new zero-day exploited in Norwegian govt attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Ivanti has fixed another vulnerability in the Endpoint Manager Mobile software (formerly MobileIron Core), exploited as a zero-day to breach the IT systems...
Weekly Update 358 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt IoT, breaches and largely business as usual so I’ll skip that in the intro to this post and jump straight...
Hack Crew Responsible for Stolen Data, NATO Investigates Claims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading SiegedSec, a hacktivist crew that targets government bodies, shared on their Telegram channel what they claim to...
CherryBlos Malware Uses OCR to Pluck Android Users’ Cryptocurrency – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Researchers this week warned of two related malware campaigns, dubbed CherryBlos and FakeTrade, targeting Android users for cryptocurrency...
Stark#Mule Malware Campaign Targets Koreans, Uses US Army Documents – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading A Korean-language malware campaign known as Stark#Mule is targeting victims using US military recruiting documents as...
Senator Blasts Microsoft for Negligence in 365 Email Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The heads of the Justice Department, the Cybersecurity and Infrastructure Security Agency, and the Federal Trade Commission...
Another AI Pitfall: Digital Mirroring Opens New Cyberattack Vector – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading “Digital twins” — AI assistants trained to service our many needs by learning about and in...
Beyond ChatGPT: Organizations Must Protect Themselves Against the Power of AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fred Kwong, Vice President & Chief Information Security Officer, DeVry University Society is on the frontier of new possibilities with artificial intelligence...
North Korean Cyberspies Target GitHub Developers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading The North Korean state-sponsored Lazarus advanced persistent threat (APT) group is back with yet another impersonation scam, this time...
Designing a Security Strategy for Defending Multicloud Architectures – Source: www.darkreading.com
Source: www.darkreading.com – Author: Etay Maor, Senior Director of Security Strategy, Cato Networks The rapid surge in cloud adoption, with 67% of enterprise infrastructure cloud-based, indicates...
Friday Squid Blogging: Zaqistan Flag – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Zaqistan Flag The fictional nation of Zaqistan (in Utah) has a squid on its flag. As...
Indirect Instruction Injection in Multi-Modal LLMs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Interesting research: “(Ab)using Images and Sounds for Indirect Instruction Injection in Multi-Modal LLMs“: Abstract: We demonstrate how images and sounds...
Flaw in Ninja Forms WordPress plugin allows hackers to steal submitted data – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Critical security vulnerabilities in a WordPress plugin used on around 900,000 websites, allow malicious hackers to steal sensitive information entered...
Hawaii Community College admits paying ransom to extortionists – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley After a ransomware attack which saw the personal information of 28,000 individuals stolen by hackers, Hawaii Community College has confirmed...
Elevating instant messaging security in 5 steps – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In our highly interconnected and fast-paced digital world, instant messaging has become an indispensable tool for business professionals of...
Gathering dust and data: How robotic vacuums can spy on you. – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...