Source: heimdalsecurity.com – Author: Livia Gyongyoși Citrix urged customers to patch NetScaler ADC and Gateway products after discovering a critical-severity zero-day vulnerability. The flaw was dubbed...
Day: July 19, 2023
Microsoft Relents, Offers Free Key Logging to All 365 Customers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Microsoft dropped the fees associated with expanded logging access for all levels of 365 license holders, after...
P2P Self-Replicating Cloud Worm Targets Redis – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Researchers have identified a cross-platform, Rust-based, peer-to-peer (P2) worm that’s targeting the Redis open-source database application; specifically, containers in...
China’s APT41 Linked to WyrmSpy, DragonEgg Mobile Spyware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Researchers have attributed two known Android surveillanceware programs — WyrmSpy and DragonEgg — to China’s APT41....
Seed Group Brings Resecurity Options to UAE Region – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The United Arab Emirates-based Seed Group has announced a strategic partnership with American cybersecurity company Resecurity. According...
3 Ways AI Could Improve Authentication – Source: www.darkreading.com
Source: www.darkreading.com – Author: Blair Cohen, Founder & President, AuthenticID No matter where you turn, everyone seems to be talking about artificial intelligence (AI) right now....
Reducing Security Debt in the Cloud – Source: www.darkreading.com
Source: www.darkreading.com – Author: Terence Harper, CISSP, Senior Sales Engineer, Ermetic Debt is a big topic of discussion these days — household debt in inflationary times,...
Leverage Threat Intelligence, AI, and Data at Scale to Boost Cyber Defenses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft As security tooling grows more sophisticated and insight into cybercriminal activity becomes more comprehensive, our collective ability to detect...
Startup Spotlight: Binarly Hardens Firmware Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Karen Spiegelman, Features Editor The December discovery of moderate to severe vulnerabilities in the baseboard management controllers (BMCs) used by 15 different...
How AI-Augmented Threat Intelligence Solves Security Shortfalls – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Security-operations and threat-intelligence teams are chronically short-staffed, overwhelmed with data, and dealing with competing demands —...
Microsoft ‘Logging Tax’ Hinders Incident Response, Experts Warn – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading A human rights organization was alerted by Microsoft that it was compromised as part of a July...
Meta confirms WhatsApp is down worldwide – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar WhatsApp, the globally renowned messaging app, unexpectedly went offline today, leaving its vast user base unable to send or receive...
Adobe emergency patch fixes new ColdFusion zero-day used in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Adobe released an emergency ColdFusion security update that fixes critical vulnerabilities, including a fix for a new zero-day exploited in...
OpenAI credentials stolen by the thousands for sale on the dark web – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Threat actors are showing an increased interest in generative artificial intelligence tools, with hundreds of thousands of OpenAI credentials for...
Microsoft: Hackers turn Exchange servers into malware control centers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft and the Ukraine CERT warn of new attacks by the Russian state-sponsored Turla hacking group, targeting the defense industry...
Microsoft expands access to cloud logging data for free after Exchange hacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft is expanding access to additional cloud logging data for customers worldwide at no additional cost, allowing easier detection of...
Facebook behavioral ads banned by Norwegian privacy watchdog – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Norwegian Data Protection Authority (DPA), the country’s data privacy watchdog, has banned behavioral advertising on Meta’s Facebook and Instagram...
Ukraine takes down massive bot farm, seizes 150,000 SIM cards – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Cyber Police Department of the National Police of Ukraine dismantled another massive bot farm linked to more than 100...
US govt bans European spyware vendors Intellexa and Cytrox – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. government has banned European commercial spyware manufacturers Intellexa and Cytrox, citing risks to U.S. national security and foreign...
FBI: Tech support scams now use shipping companies to collect cash – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan FBI warns of a surge in tech support scams targeting the elderly across the United States and urging victims to...
U.S. preparing Cyber Trust Mark for more secure smart devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu A new cybersecurity certification and labeling program called U.S. Cyber Trust Mark is being shaped to help U.S. consumers choose...
Comprehensive analysis of initial attack samples exploiting CVE-2023-23397 vulnerability – Source: securelist.com
Source: securelist.com – Author: Francesco Figurelli, Eduardo Ovalle On March 14, 2023, Microsoft published a blogpost describing an Outlook Client Elevation of Privilege Vulnerability (CVSS: 9.8...
How to Manage Your Attack Surface? – Source:thehackernews.com
Source: thehackernews.com – Author: . Attack surfaces are growing faster than security teams can keep up. To stay ahead, you need to know what’s exposed and...
CISA and NSA Issue New Guidance to Strengthen 5G Network Slicing Against Threats – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 19, 2023THNNetwork Security U.S. cybersecurity and intelligence agencies have released a set of recommendations to address security concerns with 5G...
Chinese APT41 Hackers Target Mobile Devices with New WyrmSpy and DragonEgg Spyware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 19, 2023THNSpyware / Mobile Security The prolific China-linked nation-state actor known as APT41 has been linked to two previously undocumented...
Exploring the Dark Side: OSINT Tools and Techniques for Unmasking Dark Web Operations – Source:thehackernews.com
Source: thehackernews.com – Author: . On April 5, 2023, the FBI and Dutch National Police announced the takedown of Genesis Market, one of the largest dark...
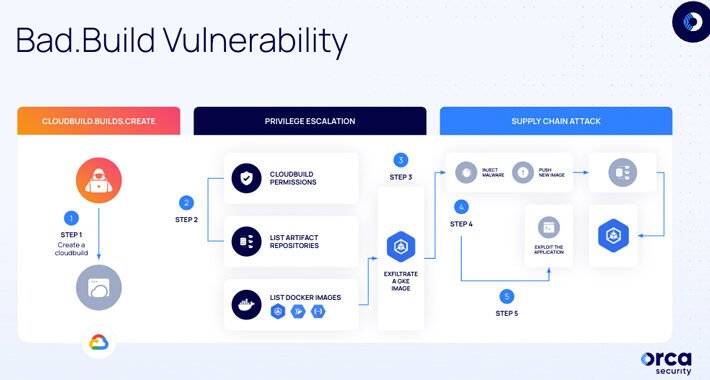
Bad.Build Flaw in Google Cloud Build Raises Concerns of Privilege Escalation – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 19, 2023THNCloud Security / Vulnerability Cybersecurity researchers have uncovered a privilege escalation vulnerability in Google Cloud that could enable malicious...
U.S. Government Blacklists Cytrox and Intellexa Spyware Vendors for Cyber Espionage – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 19, 2023THNCyber Espionage / Spyware The U.S. government on Tuesday added two foreign commercial spyware vendors, Cytrox and Intellexa, to...
Zero-Day Attacks Exploited Critical Vulnerability in Citrix ADC and Gateway – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 19, 2023THNVulnerability / Cyber Threat Citrix is alerting users of a critical security flaw in NetScaler Application Delivery Controller (ADC)...
Defend Against Insider Threats: Join this Webinar on SaaS Security Posture Management – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 14, 2023The Hacker NewsSaaS Security / Cybersecurity As security practices continue to evolve, one primary concern persists in the minds...