Source: www.securityweek.com – Author: Ryan Naraine Infisical, a San Francisco startup working on open-source technology to help organizations manage secrets sprawl, has banked $2.8 million in...
Day: July 5, 2023
Japan’s Nagoya Port Suspends Cargo Operations Following Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Port of Nagoya, Japan’s largest port in terms of cargo capacity, has suspended loading and unloading following a ransomware...
Exploited Solar Power Product Vulnerability Could Expose Energy Organizations to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Hundreds of energy organizations could be exposed to attacks due to an actively exploited vulnerability affecting a solar power monitoring...
Sweden Orders Four Companies to Stop Using Google Tool – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Sweden on Monday ordered four companies to stop using a Google tool that measures and analyses web traffic as doing so...
Ransomware Criminals Are Dumping Kids’ Private Files Online After School Hacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The confidential documents stolen from schools and dumped online by ransomware gangs are raw, intimate and graphic. They describe student...
Firefox 115 Patches High-Severity Use-After-Free Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Mozilla on Tuesday announced the release of Firefox 115 to the stable channel with patches for a dozen vulnerabilities, including...
Cybersecurity M&A Roundup: 23 Deals Announced in June 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Twenty-three cybersecurity-related merger and acquisition (M&A) deals were announced in June 2023. An analysis conducted by SecurityWeek shows that more...
EU Court Deals Blow to Meta in German Data Case – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Facebook, Instagram and WhatsApp may need to overhaul how they collect the data of users in Europe after the top EU...
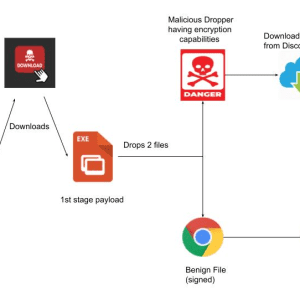
RedEnergy Stealer-as-a-Ransomware employed in attacks in the wild – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini RedEnergy is a sophisticated stealer-as-a-ransomware that was employed in attacks targeting energy utilities, oil, gas, telecom, and machinery sectors. Zscaler...
The Port of Nagoya, the largest Japanese port, suffered a ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Port of Nagoya, the largest port in Japan, suffered a ransomware attack that severely impacted its operations. The Port...
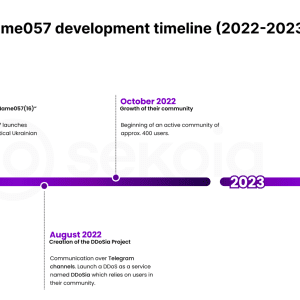
NoName(057)16’s DDoSia Project’s gets an upgrade – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The DDoSia attack tool received an upgrade, it supports a new security mechanism to conceal the list of targets. Researchers at the...
Swedish data protection authority rules against the use of Google Analytics – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Swedish data protection watchdog warns companies against using Google Analytics due to the risk of surveillance operated by the US...
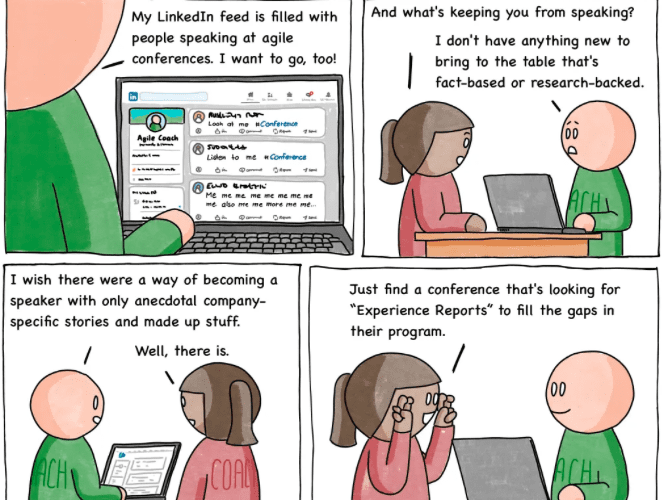
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #249 — How to Become a Speaker at Conferences – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #249 — How to Become a Speaker at Conferences How...
How to Secure Your Container Registries With GitGuardian’s Honeytoken – Source: securityboulevard.com
Source: securityboulevard.com – Author: Guest Expert Sponsorships Available Keshav Malik Keshav is a full-time Security Engineer who loves to build and break stuff. He is constantly...
Fortinet Bug: RUN — Don’t Walk — to Patch Critical RCE – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Or just get it off the internet, stat. Fortinet FortiOS security devices have yet another nasty bug. Is your shop...
BSidesSF 2023 – Tom DNetto – Sandboxes All The Way Down – A Hitchhiker’s Guide To Platform Containment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Here’s MITRE’s top-25 CWE list — with your old vulnerability category favorites – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings MITRE has published this year’s list of vulnerability categories. The list of the top 25 types from the Common Weakness Enumeration (CWE) system...
How Audits + Testing = Long-Term Savings – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ray Overby Data breaches have reached record highs in recent years. In the past three years alone, nearly nine in 10 companies...
How to Use FAIR Analysis to Quantify Risk from the MOVEit Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jacqueline Lebo The Russian-speaking CL0P ransomware gang is on a tear exploiting zero-day vulnerabilities in the managed file transfer (MFT) solution MOVEit...
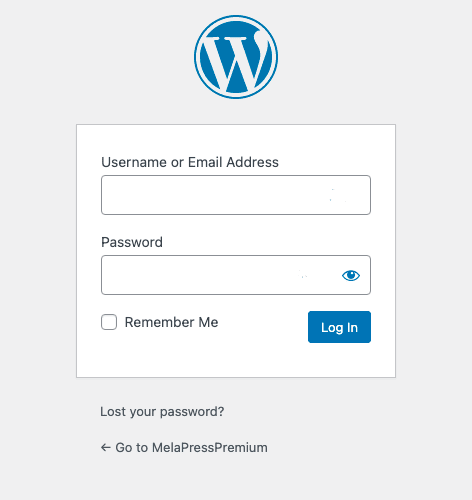
How to change your WordPress login URL – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joel Barbara Changing the WordPress login URL is a security practice recommended by several WordPress bloggers and security professionals. Even so, many...
Adventures in Software Audits, Part Three: The Paradigm Battle – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Gary Maynard III Many commercial disputes are launched with a demand letter. The form of those letters is familiar: The author...
Email crypto phishing scams: stealing from hot and cold crypto wallets – Source: securelist.com
Source: securelist.com – Author: Roman Dedenok, Konstantin Zykov The higher the global popularity of cryptocurrencies and the more new ways of storing them, the wider the...
Password Management Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy from TechRepublic Premium provides guidelines for the consistent and secure management of passwords for employees and system and service accounts....
High-Severity Flaws Fixed in Firefox 115 Update – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Mozilla Foundation has released Firefox 115 to its stable channel. The update addresses several high-level vulnerabilities. One of them, CVE-2023-37201, involved...
Sophisticated Email Attacks Target Cryptocurrency Wallets – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new malicious campaign relying on email attacks has been discovered targeting the most popular forms of cryptocurrency storage: hot and...
UK Citizens Wary of NHS AI Use, Citing Privacy Concerns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over half (56%) of UK citizens do not trust the NHS to use AI to analyze patient data due to security...
European Commission to Tweak GDPR For Cross-Border Cases – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The European Commission has proposed changes to the GDPR intended to improve cooperation between Data Protection Authorities (DPAs) working on enforcement...
New Tool Helps Devs Check For Manifest Confusion Mismatches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A security researcher has released a new tool designed to help developers check npm packages impacted by the recently discovered manifest...
Security Experts Raise Major Concerns With Online Safety Bill – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Dozens of the UK’s leading experts on security and privacy have raised grave concerns with Online Safety Bill provisions which call...
Class-Action Lawsuit for Scraping Data without Permission – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier I have mixed feelings about this class-action lawsuit against OpenAI and Microsoft, claiming that it “scraped 300 billion words from...