Source: www.csoonline.com – Author: To find the right security job or hire the right candidate, you first need to find the right recruiter. Ready to get...
Month: June 2023
Top cybersecurity M&A deals for 2023 – Source: www.csoonline.com
Source: www.csoonline.com – Author: Shutterstock Uncertainty and instability marked the end of 2022 for many in the tech sector, a trend that bled into the beginning...
Convincing Colleagues that Zero Trust Adoption is in Their Interest – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nik Hewitt Zero trust adoption can be a stumbling block for our colleagues, but it doesn’t have to be that way We...
Enhancing cloud security posture with an effective cloud governance framework – Source: securityboulevard.com
Source: securityboulevard.com – Author: Synopsys Editorial Team Hot Topics Convincing Colleagues that Zero Trust Adoption is in Their Interest Enhancing cloud security posture with an effective...
Chrome Extensions Warning — Millions of Users Infected – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Perhaps as many as 87 million victims—maybe more. Google is under fire yet again for the lax way it manages...
FireTail Report Finds API Security Breaches are few but Lethal – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard An analysis of cybersecurity breaches in 2022 conducted by FireTail, a provider of a platform for securing application programming interfaces...
Acunetix sunsets support for Windows 8 and Server 2012 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tuncay Kayaoglu A new Acunetix Premium update has been released for Windows and Linux: 15.7 We are sunsetting the support for Windows...
5 AI threats keeping SOC teams up at night – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ericka Chickowski The explosion in the use of OpenAI’s ChatGPT and other large language models (LLMs) — along with a range of...
Killnet: Inside the World’s Most Prominent Pro-Kremlin Hacktivist Collective – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flashpoint Within the realm of digital warfare, the threat actor group known as “Killnet” has established itself as a high-visibility force. Emerging...
Red Sift Taps GPT-4 to Better Identify Cybersecurity Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Red Sift today announced it is employing the GPT-4 generative artificial intelligence (AI) platform via a Relevance Detection capability to...
When it Comes to Cybersecurity, Prepare, Protect, Deploy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Zachary Folk Attackers covet your data and never stop coming for it. In 2021, ransomware cases grew by 92.7%. Are you protecting...
Strengthen Cybersecurity with a Multi-Layered 3-2-1-0 Data Protection Strategy – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
LIVE Webinar | Protecting Microsoft SQL Server at Scale – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Chris Lumnah Solution Architect, Rubrik Chris Lumnah is an Advisory Solutions Architect with 20 years of database experience. He has spent...
Key Strategies for Secure Access to Private Apps – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Microsoft Attributes MOVEit Transfer Hack to Clop Affiliate – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Governance & Risk Management , Patch Management UK Payroll Provider Zellis’ MOVEit Hack Affects British Airways,...
Strengthen Cybersecurity with a Multi-Layered 3-2-1-0 Data Protection Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
LIVE Webinar | Protecting Microsoft SQL Server at Scale – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Chris Lumnah Solution Architect, Rubrik Chris Lumnah is an Advisory Solutions Architect with 20 years of database experience. He has spent...
Key Strategies for Secure Access to Private Apps – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Microsoft blames Clop ransomware gang for ‘MOVEit Transfer’ attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft attributes the recent campaign exploiting a zero-day in the MOVEit Transfer platform to the Clop ransomware gang. The Clop...
Idaho Hospitals hit by a cyberattack that impacted their operations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Last week two eastern Idaho hospitals and their clinics were hit by a cyberattack that temporarily impacted their operations. Last...
Experts warn of a surge of TrueBot activity in May 2023 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini VMware’s Carbon Black Managed Detection and Response (MDR) team observed a surge of TrueBot activity in May 2023. Researchers at...
Magecart campaign abuses legitimate sites to host web skimmers and act as C2 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A new ongoing Magecart web skimmer campaign abuse legitimate websites to act as makeshift command and control (C2) servers. Akamai...
Spanish bank Globalcaja confirms Play ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Play ransomware group claims responsibility for a ransomware attack that hit Globalcaja, one of the major banks in Spain. Globalcaja...
Security Affairs newsletter Round 422 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Satacom delivers browser extension that steals cryptocurrency – Source: securelist.com
Source: securelist.com – Author: Haim Zigel, Oleg Kupreev Satacom downloader, also known as LegionLoader, is a renowned malware family that emerged in 2019. It is known...
Microsoft: Lace Tempest Hackers Behind Active Exploitation of MOVEit Transfer App – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 05, 2023Ravie LakshmananZero Day / Cyber Attack Microsoft has officially linked the ongoing active exploitation of a critical flaw in...
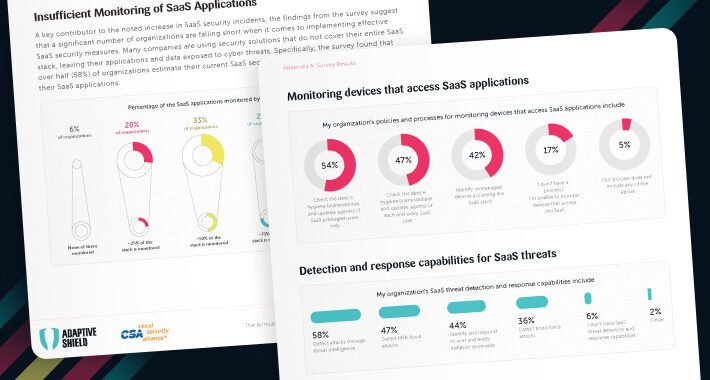
The Annual Report: 2024 Plans and Priorities for SaaS Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Over 55% of security executives report that they have experienced a SaaS security incident in the past two years — ranging...
Magento, WooCommerce, WordPress, and Shopify Exploited in Web Skimmer Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 05, 2023Ravie LakshmananWebsite Security / Magecart Cybersecurity researchers have unearthed a new ongoing Magecart-style web skimmer campaign that’s designed to...
Brazilian Cybercriminals Using LOLBaS and CMD Scripts to Drain Bank Accounts – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 05, 2023Ravie LakshmananBanking Security / Malware An unknown cybercrime threat actor has been observed targeting Spanish- and Portuguese-speaking victims to...
Alarming Surge in TrueBot Activity Revealed with New Delivery Vectors – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 05, 2023Ravie LakshmananMalware / Cyber Threat A surge in TrueBot activity was observed in May 2023, cybersecurity researchers disclosed. “TrueBot...